Analyzing the Flawed Logic in the JokInTheBox Attack
Overview
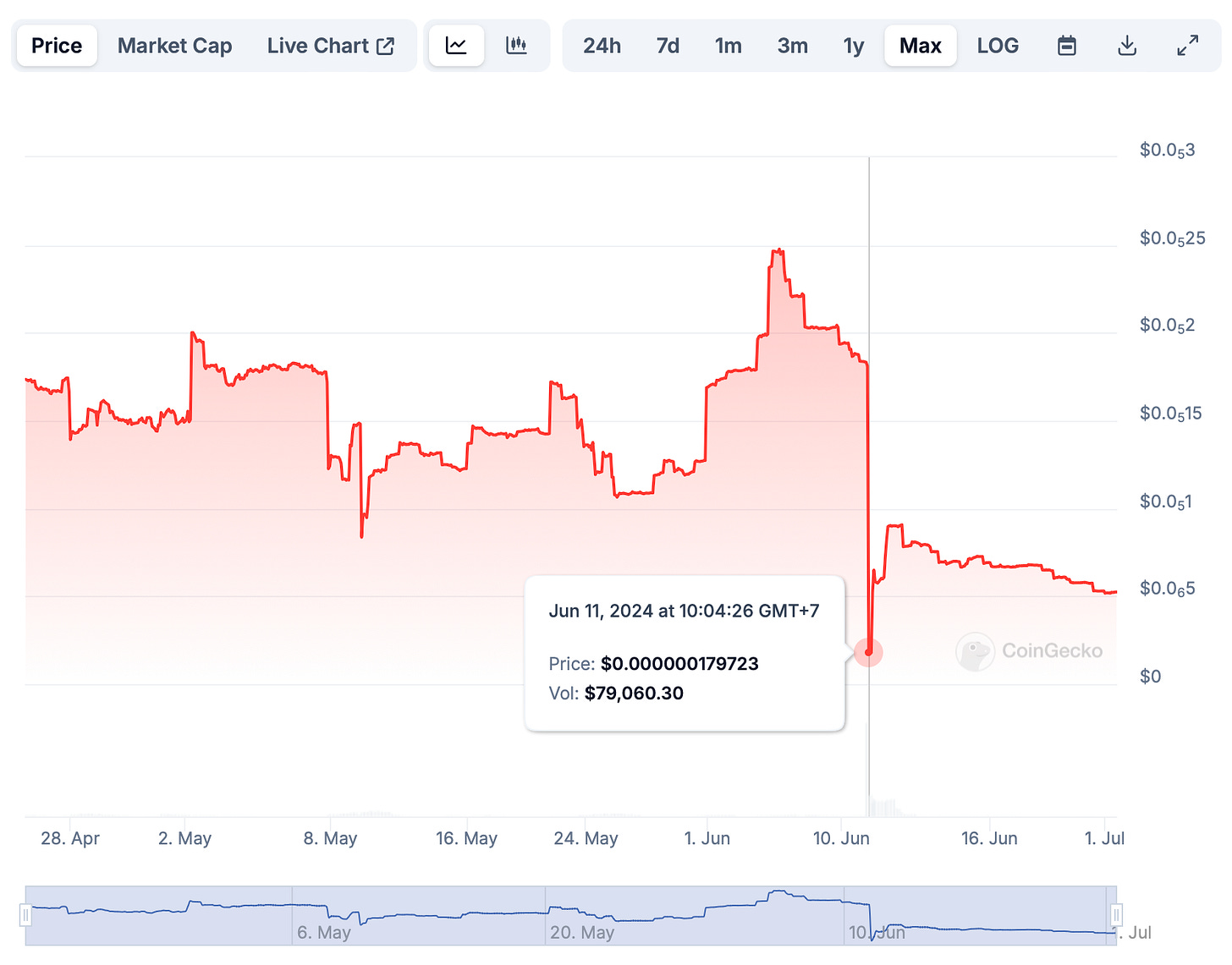
On June 11, 2024, a significant security breach was identified on the Ethereum network, specifically targeting the JokInTheBox project. This attack resulted in a financial loss of approximately $34,292 USD.
Chain: Ethereum
Attacker: 0xfcd4acbc55df53fbc4c9d275e3495b490635f113
Attack Contract: 0x9d3425d45df30183fda059c586543dcdeb5993e6
Victim: 0xa6447f6156effd23ec3b57d5edd978349e4e192d
$JOK Price Impact: ~90%
Analysis
The attack commenced with the perpetrator initiating a transaction (Etherscan link), using 0.2 ETH to acquire 366,060,210 JOK tokens via Uniswap V2. Subsequently, these tokens were transferred to the attack contract located at address 0x9d3425d45df30183fda059c586543dcdeb5993e6 and staked.
The critical phase of the attack unfolded as follows:
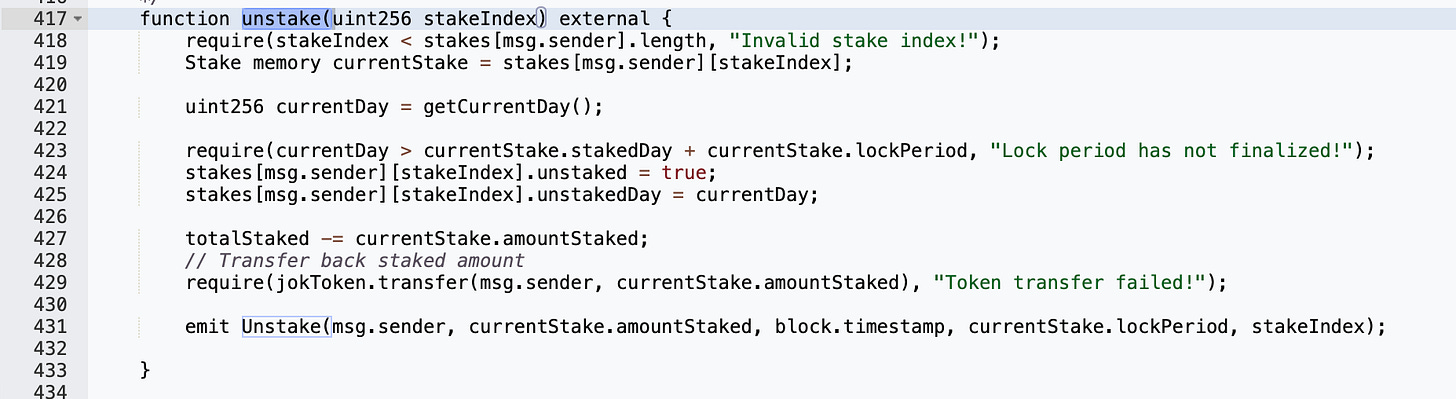
The vulnerability was rooted in the unstake function of the JokInTheBox contract.
The unstake function miss verifying whether stakes[msg.sender][stakeIndex].unstaked was true, thereby neglecting to check if the staked asset had already been withdrawn. This oversight permitted the attacker to repeatedly execute the unstake function, allowing them to withdraw all users' staked assets multiple times.
Conclusion
The primary vulnerability in the JokInTheBox contract was the lack of a verification mechanism to ensure that a stake had not already been unstaked and withdrawn during the unstake process. This flaw enabled the attacker to repeatedly unstake and siphon off all users' staked assets.
To mitigate such vulnerabilities, it is imperative that project teams rigorously validate their economic models and code logic during the design phase. Employing multiple auditing firms for comprehensive cross-audits before deploying contracts can significantly enhance security. Additionally, it is essential to focus on robust security measures throughout the development lifecycle, ensuring thorough testing and validation of all contract functions to prevent similar attacks in the future.