Analyzing the LZ Token hack
At 14:35, Vietnam time on February 27, 2023, LZ Token recorded a sudden dumping event as follows:
After receiving the information, Verichains conducted an analysis, and identified the reason for the hack was from exploiting a security vulnerability in a contract, temporarily called Contract X at address 0x6d8981847eb3cc2234179d0f0e72f6b6b2421a01, which has not been verified. It is worth noting that the "LZ Deployer" wallet had "approved" a large amount of LZ and BUSD to this contract over a year ago.
Attack flow analysis
LZ Token was exploited by an address labeled as DND Exploiter at 14:32 Vietnam time on February 27th, 2023. The transaction caused the price of LZ Token to be dumped: https://bscscan.com/tx/0xaee8ef10ac816834cd7026ec34f35bdde568191fe2fa67724fcf2739e48c3cae
The hacker deployed an "attack contract", the flow of the LZ Token attack is carried out in this contract as follows:
Call a function that finds a pair and performs a swap of LZ to BUSD on Biswap (called the swap function). This function belongs to Contract X mentioned above and more than 1 year ago, the "LZ Deployer" wallet approved 1 billion LZ, 39 million BUSD for this contract.
LZ Deployer approves 1 billion LZ for the contract: https://bscscan.com/tx/0x3ab13a622105fdcf0293ed1a0a7918375e1a05123160efdc5e23ec121ac6d944
LZ Deployer approves over 39 million BUSD for the contract: https://bscscan.com/tx/0x444edcefe7de6504ae70deb292c80211dbff0ddb13bf6689cb05d5a068307ca0
The hacker called the swap function of a third-party contract to swap 9.8 trillion LZ, receiving nearly 7 BUSD back to LZ Deployer through the BSW-LP Pair (Biswap).
Then, the hacker deposited 50 BUSD into the attack contract and immediately swapped 50 BUSD to get back more than 9.8 trillion LZ through Biswap.
Finally, the attacker swapped over 9.8 trillion LZ for nearly 88k BUSD through PancakeSwap. At this point, the price of LZ Token dropped 46 times.
When receiving nearly 88k BUSD, the hacker claimed these tokens to their own wallet and executed a self-destruct attack contract.
Some related addresses:
LZ Deployer: 0xdad254728A37D1E80C21AFae688C64d0383cc307
Attacker: 0x7d192FA3a48C307100C3E663050291Fff786aA1F
Attack Contract: 0x1C2B102f22c08694EEe5B1f45E7973b6EACA3e92
Contract X: 0x6D8981847Eb3cc2234179d0F0e72F6b6b2421a01
BSW-LP: 0xDb821BB482cfDae5D3B1A48EeaD8d2F74678D593
Vulnerability and cause analysis
Above is the behavior of the hacker exploiting the dump of LZ Token and profiting nearly 88k BUSD. The following is a detailed analysis of the security vulnerabilities and causes of the attack.
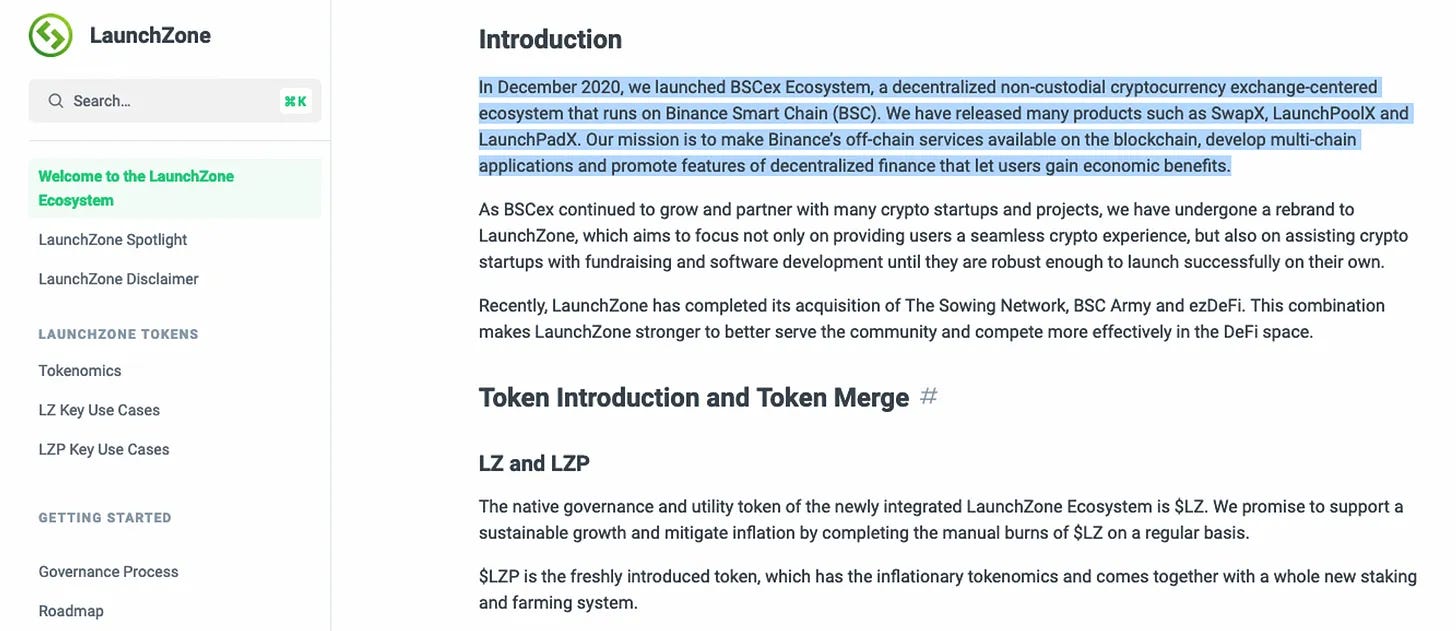
We have determined that Contract X mentioned above is the implementation contract of SwapX Proxy (not yet verified and audited), the Proxy will allow users to pass data and call the implementation contract: https://bscscan.com/address/0x0ccee62efec983f3ec4bad3247153009fb483551
SwapX is an AMM developed in the BSCex ecosystem and LZ Token is integrated within this ecosystem.
When reviewing the bytecode of the contract, some security vulnerabilities can be seen as follows:
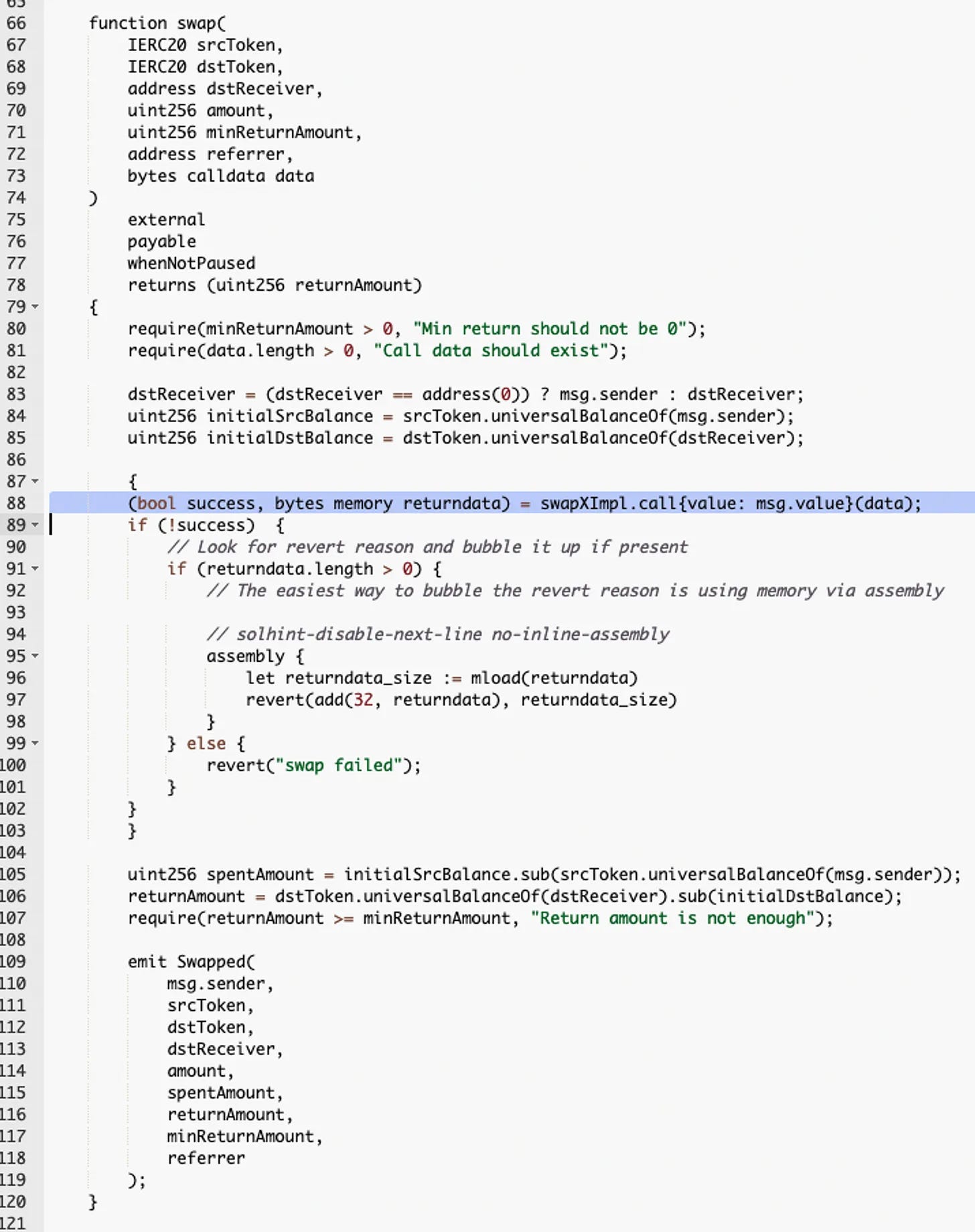
Call implementation using "call" instead of "delegatecall"
Functions in the implementation allow unrestricted external calls for each proxy
In particular, a serious vulnerability comes from the function responsible for the swap feature in the implementation, which executed "transferfrom()" from any address instead of the usual "msg.sender" transferfrom logic of other swaps. Therefore, a hacker can "help" someone else swap by controlling the data call passed in.
Combined with the "LZ Deployer" wallet, which previously used SwapX and approved a large amount of BUSD and LZ tokens (possibly due to carelessness when using SwapX's front-end when swapping), the hacker performed a large amount of LZ token swapping for BUSD, causing the price of LZ to drop drastically through the Biswap pair. The hacker then used 50 BUSD to buy back 9.8 million LZ tokens, and finally exchanged those 9.8 million tokens for nearly 88k BUSD on PancakeSwap's trading platform.
Verichains has sent detailed information and analysis of the incident to the LaunchZone project to be able to handle, fix and mitigate the damage.
Suggestions:
If you have ever used SwapX on BSCex, please check your wallet, especially previous approval transactions through online tools such as https://defi.krystal.app/token-approval-checker
Addresses holding large amounts of money in the ecosystem should be cautious when using it.
Only approve the amount necessary to perform the transaction, do not approve too much.
Each product before launch or trusted use must go through a security audit by reputable security companies.
==============
About Verichains
Since 2017, Verichains has been a pioneer and leading blockchain security firm in APAC, with extensive expertise in security, cryptography and core blockchain technology. More than 200 clients trust us with $50 billion in assets under protection, including several high-profile clients such as BNB Chain, Klaytn, Wemix, Multichain, Line Corp, Axie Infinity, Ronin Network, and Kyber Network.
Our world-class security and cryptography research team have found several vulnerabilities in layer-1 protocol, crypto library, bridge, and smart contracts. We are also proud to be the firm that helped to investigate, root cause analysis, and fix security issues in the two largest global crypto hacks: BNB Chain Bridge and Ronin Bridge (Sky Mavis).
With the in-depth research and development of blockchain technology, Verichains provides blockchain security services such as blockchain protocol and smart contract security audit, mobile application protection, key management solution, on-chain risk monitoring, and red team/penetration testing services.
Homepage:
https://www.verichains.io
Email: info@verichains.io
Twitter: https://twitter.com/Verichains
Linkedin: https://www.linkedin.com/company/verichains
Facebook: https://facebook.com/verichains
Telegram: https://t.me/+Y29xcaxJLJxjNDVl