Anatomy of a Hack: How a Simple Logic Flaw Led to a $285k Exploit on Zoth
On March 1, 2025, Zoth (@zothdotio), a restaking layer for real-world assets (RWAs), was hit by a $285,000 exploit. The culprit wasn't a complex cryptographic puzzle, but a sneaky logic flaw hiding in plain sight within the mintWithStable() function.
Attack Summary
The attacker found a way to trick the system into thinking they had deposited far more collateral than they actually had, allowing them to mint ZeUSD tokens without proper backing and drain the funds. Let's break down exactly how it happened.
Attacker’s Address:
0x806D9Attack Transaction:
0xc3f70Vulnerable Zoth Contract:
0xe2574
Root Cause of Vulnerability
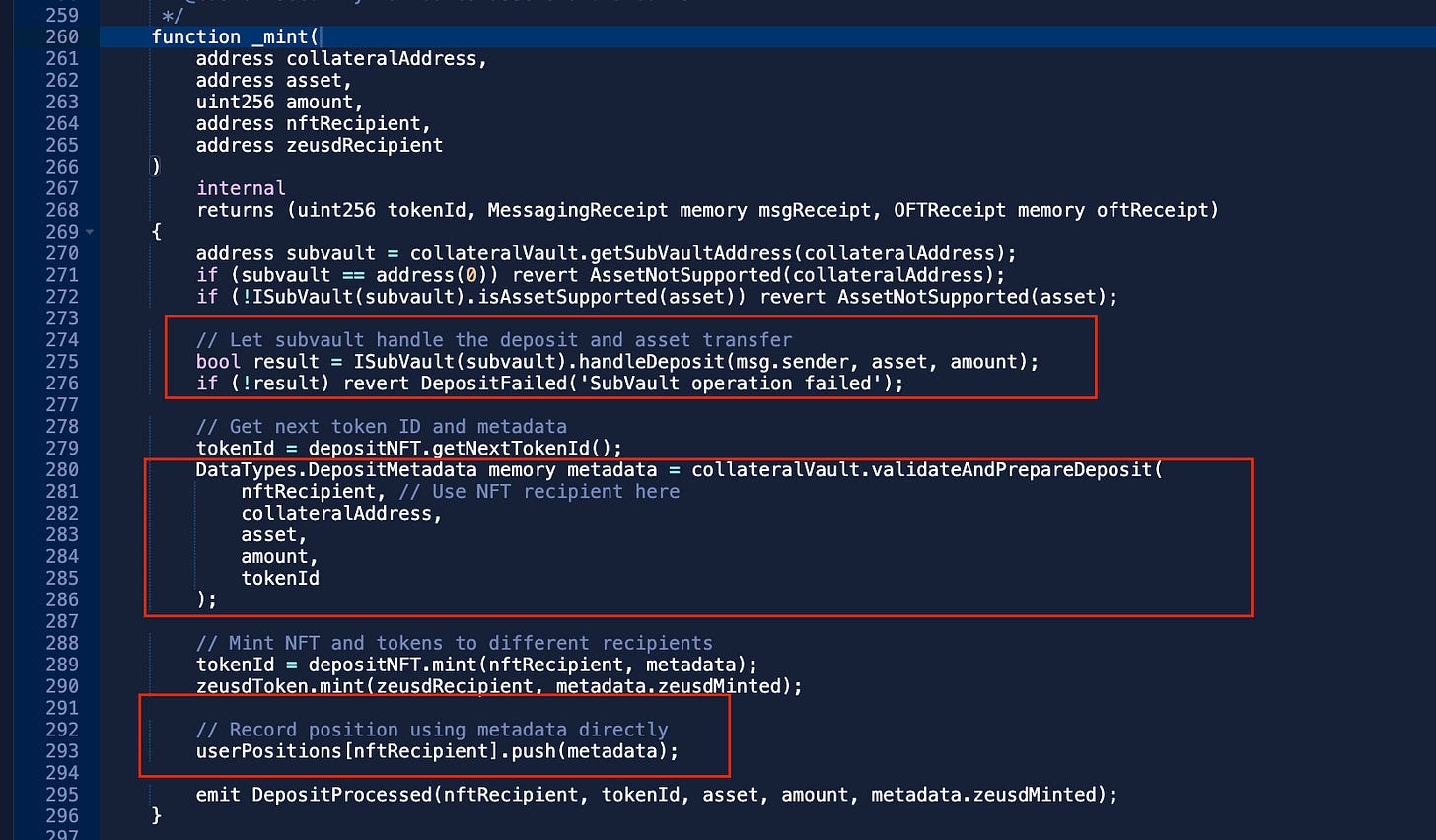
The root of the problem was a critical validation error. Here’s how the mintWithStable() function was supposed to work:
A user deposits a stablecoin, like
USDC.The contract swaps that
USDCfor a collateral token (e.g.,wM).The contract then calculates how much
ZeUSDthe user can mint based on the value of the collateral received.
The problem was in step #3. The contract made a fatal mistake: it checked the value of the initial USDC deposit, not the actual amount of collateral received after the swap.
This happened because the validateAndPrepareDeposit() function used the amount variable (the initial deposit) for the Loan-to-Value (LTV) check, instead of the collateralReceived variable, which holds the true amount of collateral obtained after the swap.
To make matters worse, the contract had no slippage protection. This meant the attacker could manipulate the price in a Uniswap V3 pool, ensuring the swap would return a tiny amount of collateral while the contract remained completely unaware.
Step by Step
The attacker followed a simple but brilliant plan:
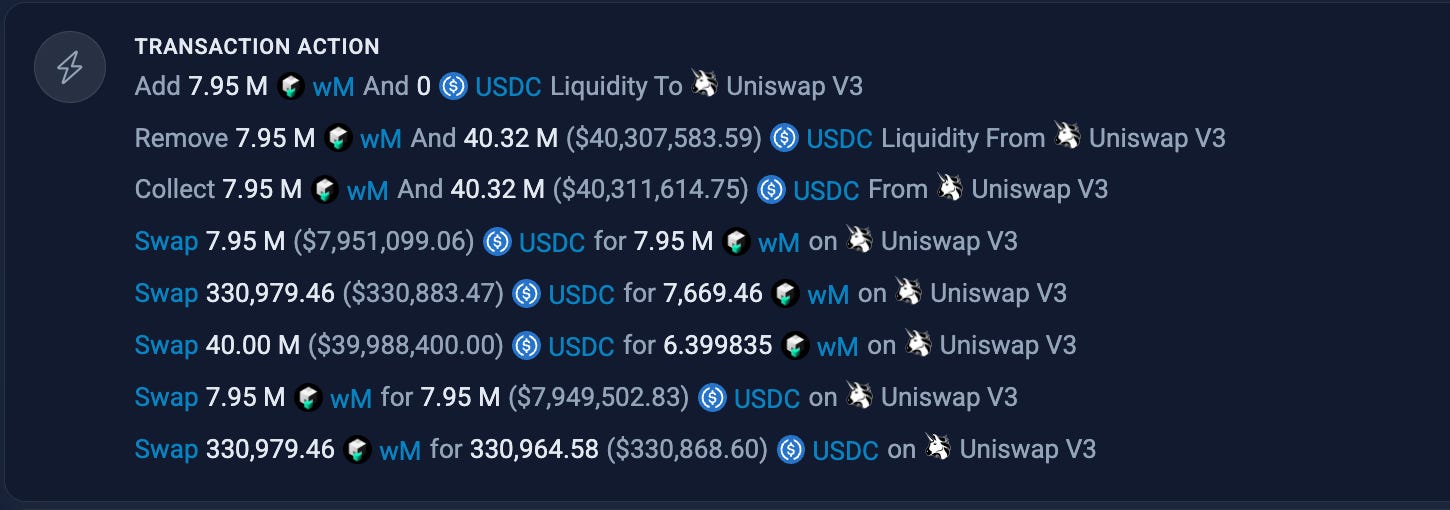
Manipulate the Pool: First, the attacker heavily distorted the swap rates in the relevant Uniswap V3 pool.
Call the Function: They then called
mintWithStable()with a largeUSDCdeposit. Due to the manipulated pool, the swap only returned 7,669 collateral tokens.Exploit the Flaw: The flawed Zoth contract didn't check the result of the swap. It looked at the initial deposit and incorrectly recorded that the attacker had provided 330,979 collateral tokens!
Cash Out: With the system believing they were fully collateralized, the attacker minted a massive amount of
ZeUSD. They then simply burned theZeUSDto withdraw the 330,979 collateral tokens they never actually deposited, walking away with a $285,000 profit.
Lessons Learned and Building Safer DeFi
The Zoth exploit is a powerful reminder that in DeFi, even a single misplaced variable can lead to devastating financial loss. The core lessons are clear:
Always validate the actual outcome of an operation, not just the initial input. The LTV check should have been based on
collateralReceived.Implement strict slippage protection on all swaps to prevent price manipulation.
Integrate reliable price oracles like Chainlink to ensure LTV calculations are based on real-time market data.
Preventing these kinds of sophisticated attacks requires more than just good coding practices; it demands a proactive, security-first mindset. That's where a professional security audit becomes essential.
At Verichains, we specialize in diving deep into smart contract logic to uncover precisely these types of vulnerabilities. Our expert auditors would have immediately flagged the incorrect LTV calculation and the lack of post-swap validation. We don't just scan for known issues; we simulate attack vectors, like the Uniswap manipulation seen here, to test a protocol's resilience under adversarial conditions.
Protect your project and your users' funds. Contact Verichains today to secure your smart contracts with an industry-leading audit.