BunniXYZ Vulnerability Exposed: How Precision Bugs Drained Millions
Bunni.xyz Exploit Analysis
Overview
On September 2, 2025, attackers exploited BunniXYZ and drained approximately $8.4 million across deployments—$2.4 million from Ethereum and $6 million from Unichain. The root cause was a precision and accounting bug in Bunni’s Liquidity Distribution Function (BunniHook), which reallocates LP capital after trades. Carefully sized swaps pushed the LDF into an unsafe state, over-crediting the attacker’s balance during rebalances. The attacker repeatedly extracted the inflated funds before emergency controls halted operations.
Background on BunniXYZ
BunniXYZ is a decentralized exchange built on Uniswap V4 that offers advanced liquidity management. Its Liquidity Density Function maximizes returns for liquidity providers, and its incentive programs reward participation. Despite rapid growth and strong adoption, BunniXYZ has faced security challenges—including notable exploits—that highlight the need for improved protocol safety.
Technical Analysis of the Exploit
Incident Overview
Date: September 2, 2025
Attacker EOA Address:
Attack Transactions:
Ethereum: 0x1c27c4d625429acfc0f97e466eda725fd09ebdc77550e529ba4cbdbc33beb97b
Unichain: 0x4776f31156501dd456664cd3c91662ac8acc78358b9d4fd79337211eb6a1d451
Root Cause
The exploit stemmed from a precision and rounding bug in BunniXYZ’s custom Liquidity Distribution Function (LDF)—a liquidity management mechanism distinct from Uniswap V4’s standard model. The attack used multiple precisely sized swaps and withdrawals that exploited a rounding error in the withdrawal logic. This created an artificial liquidity shortage and enabled profitable sandwich attacks on the recalculated liquidity. The bug made the pool’s total liquidity appear much lower than reality, misleading the contract’s accounting and allowing the attacker to drain over $8 million across Ethereum and Unichain pools.
Attack Flow
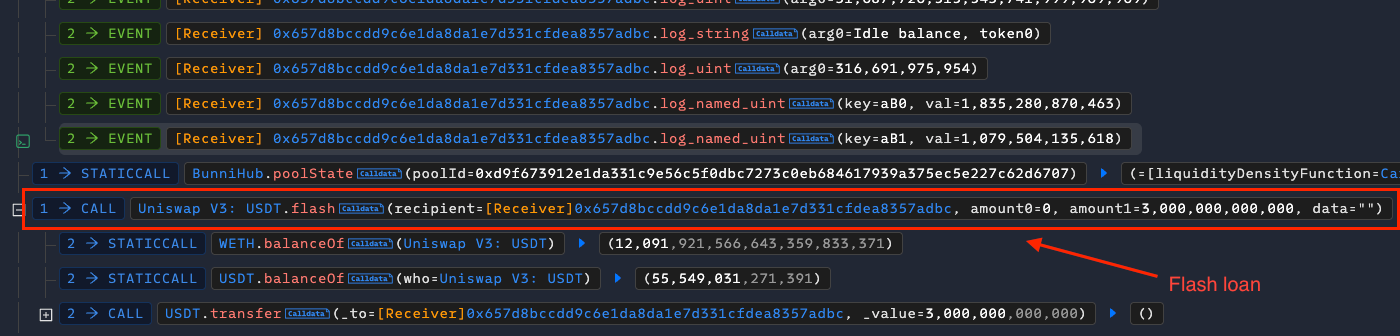
Step-by-step breakdown of the BunniXYZ exploit transaction on Ethereum - 0x1c27c4d625429acfc0f97e466eda725fd09ebdc77550e529ba4cbdbc33beb97b:
The attacker borrowed 3 million USDT via flash loan from a Uniswap V3 liquidity pool, providing the capital needed for the exploit at no upfront cost.
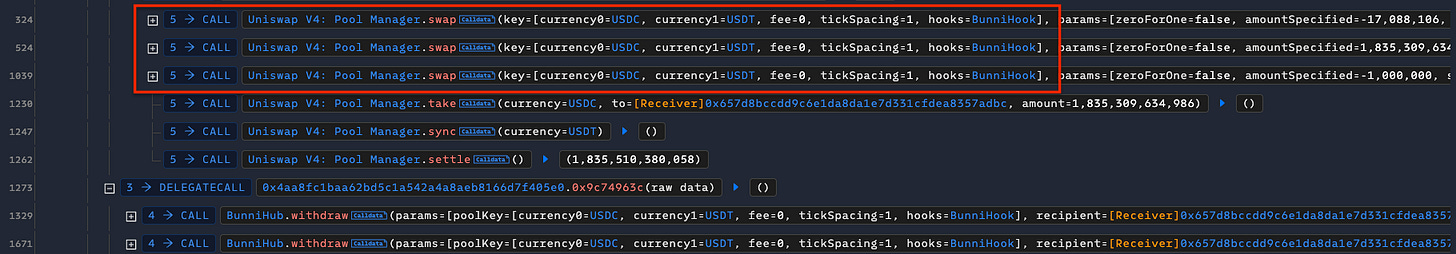
The attacker executed a series of precisely sized swaps between USDT and USDC in Bunni’s USDC/USDT pool. These swaps manipulated the pool’s internal price tick and shifted its liquidity distribution.
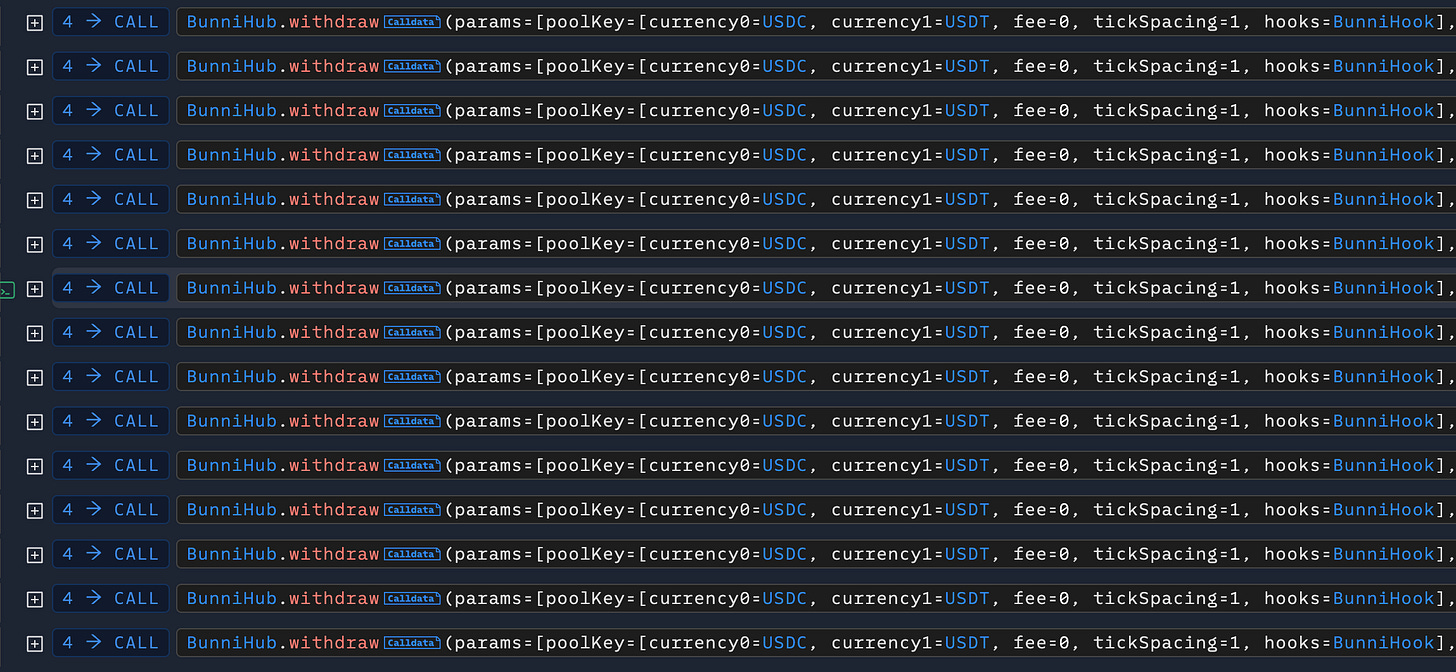
Then, the attacker executed 44 small withdrawals through the BunniHubLogic::withdraw() function. A rounding and precision flaw caused these withdrawals to drastically reduce the pool’s active stablecoin balances—especially USDC—while burning minimal liquidity shares. This artificially created a liquidity shortage that misrepresented the pool’s true liquidity.
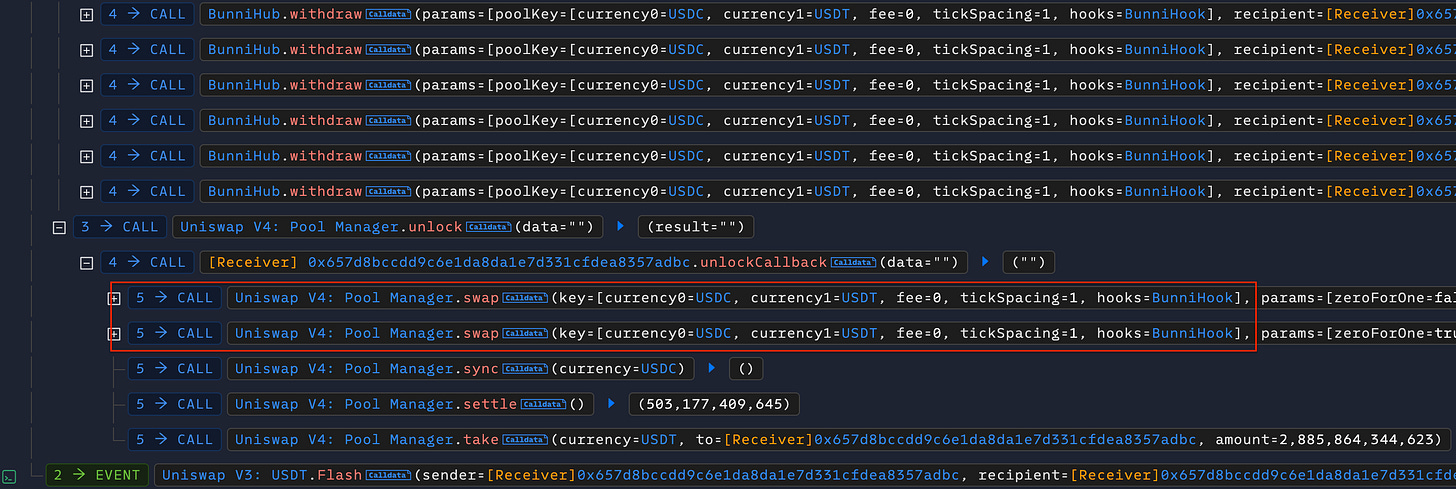
After depleting the pool’s liquidity, the attacker triggered large swaps that caused the pool’s spot price tick to shift sharply. This artificially inflated apparent liquidity, which the attacker exploited for profitable sandwich trades and wrongful token extraction.
Finally, the attacker collected excess tokens resulting from the flawed accounting and repaid the flash loan along with fees, completing the atomic exploit.
Conclusion
The BunniXYZ hack exposed a critical vulnerability in its custom Liquidity Distribution Function (LDF). Attackers exploited a precision rounding bug by executing carefully sized swaps and withdrawals that manipulated the rebalancing calculations. This allowed them to withdraw far more tokens than entitled. The exploit drained over $8 million across Ethereum and Unichain pools. BunniXYZ responded quickly by pausing smart contracts and launching an investigation to secure user funds.
Lessons Learned
Adopt Rigorous Multi-Layer Testing: Protocols should implement comprehensive testing—including unit, integration, fuzz, and formal verification tests—early and continuously throughout development to catch logic flaws and edge-case vulnerabilities before deployment.
Guard Against Precision and Rounding Bugs: Financial calculations must handle precision and rounding carefully. Small arithmetic errors can lead to major exploits.
Implement Robust Flash Loan Protections: Flash loans amplify exploits. Protocols need strong detection and mitigation mechanisms to prevent manipulative trades during flash loan windows.
These lessons help build safer, more resilient protocols that protect user funds and ensure long-term ecosystem stability.


🙌
https://substack.com/@leontsvasmansapiognosis/note/c-166519863