Burned by Design: The Fatal Flaw Behind Future Protocol’s $4.6M Exploit
On July 2, 2025, the Future Protocol project on BNB Chain fell victim to an exploit that resulted in a loss of approximately $4.6 million. This analysis breaks down the attack mechanics, pinpoints the root cause, and highlights essential security lessons learned.
Incident Overview
Date: Jul 02, 2025
Platform: Binance Smart Chain (BSC)
Attacker Address: 0x18dd258631b23777c101440380bf053c79db3d9d
Vulnerable Contract: 0xb192d4a737430aa61cea4ce9bfb6432f7d42592f (FPC Token)
Attack Transaction: 0x3a9dd216fb6314c013fa8c4f85bfbbe0ed0a73209f54c57c1aab02ba989f5937
Exploit Mechanics
First, the attacker borrowed 23,020,000 USDT from the USDT-USDC pool via a flash loan.
Next, the attacker used the entire amount to manipulate the FPC token price in the FPC-USDT pool. They swapped all 23,020,000 USDT for FPC, driving the FPC reserve in the pool down to just 160,836 tokens.
(Note: During the swap, the attacker used a trick transfer USDT inside the pancakeCall, causing the event log to display 23,020,001 USDT used. However, only 23,020,000 USDT was actually used for the swap.)
Following that, the attacker used 247,441 FPC to swap back for USDT more than the pool's remaining FPC reserve of 160,836.76. Because of the flawed mechanics, this resulted in them receiving 27,693,883 USDT.
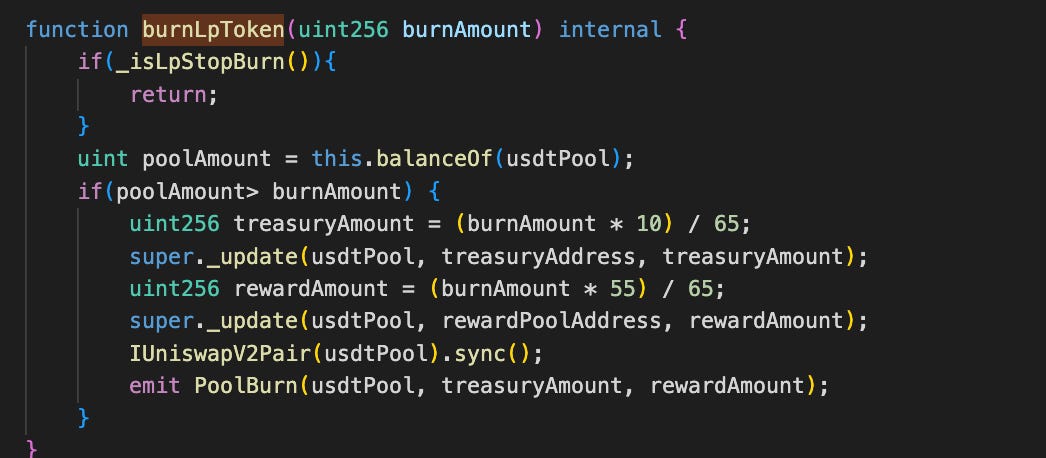
Deep dive to to this swap, when attacker transfer token to the pool.
During the swap, when the attacker transferred FPC to the pool, 65% of the input (247,441 FPC) was burned. Specifically, 160,836.76 FPC was sent from the pool to the treasury and reward pool. Immediately after, the pool was synced.
This caused the FPC reserve in the pool to drop drastically to just ~0.000065 FPC, while the corresponding USDT reserve remained high. As a result, the swap function calculated a massive USDT output in exchange for what remained of the 247,441 FPC.
Root Cause
The root cause of this vulnerability lies in the tokenomics design: burning FPC tokens directly from the pool's balance during sell operations, followed by an immediate call to sync. This directly reduces the pool's token reserve, violating the constant product invariant (K = x * y) used in UniswapV2. This broken invariant allowed the attacker to manipulate the pool's pricing mechanism and extract significant profit.
Lesson learned
Avoid Direct Token Burns from Liquidity Pools
Burning tokens directly from a liquidity pool's balance (e.g., during a
transferorswap) disrupts the constant product formula (x * y = k) used in AMM protocols like UniswapV2. Any manipulation of pool reserves outside the standard swap mechanism leads to broken pricing logic and opens up severe attack vectors.Always Validate Tokenomics with AMM Mechanics
Custom tokenomics (e.g., transfer taxes, burns, fees) must be thoroughly tested against AMM behavior. Special care is needed when deploying such tokens in pools, especially if their mechanics alter balances without respecting the assumptions of the AMM protocol.
Simulate Edge Cases in Security Reviews
Security audits and testing should include simulations of flash loan scenarios and unexpected behaviors like internal token transfers or unexpected reserve changes. This helps reveal unintended consequences of token logic interacting with DeFi protocols.