Coin31 Token Incident Analysis
On November 2, 2024, the Coin31 token was attacked, resulting in an approximate $26k loss on the BSC mainnet. The hack targeted an unprotected function in the token contract, which controls the approval of the Coin31 token.
Overview
Attacker: https://bscscan.com/address/0x01414e2c189c880b25cf238c38f39d300a641ff6
Vulnerable Contract: https://bscscan.com/address/0x52fbd9a94587f8ce757d1bd0a89abfe8d6233591
Attack Transaction: https://bscscan.com/tx/0x28f8e92e64595edf2680a40c5ca1dcfddf2a74fde6f2b51efc09d31edef09d0f
Exploit Analysis
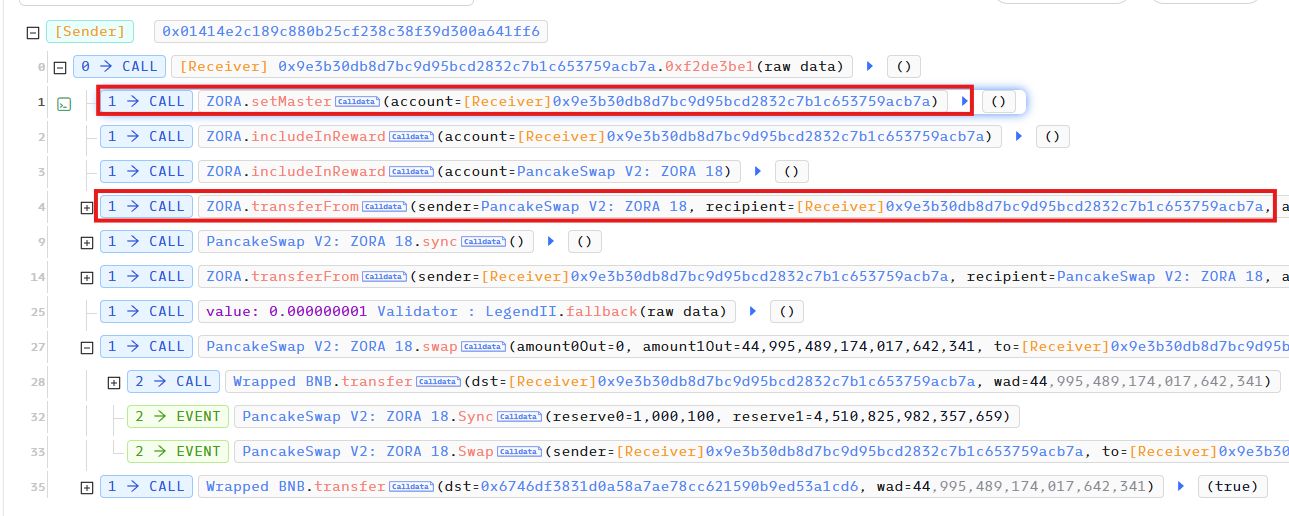
In the exploit transaction, the attacker called the setMaster function and set the master address to point to their contract. This function is unprotected, allowing anyone to set the master address to any value if it has not been initialized. The source code of the setMaster function is shown below:
The setMaster function lacks an access control mechanism, allowing anyone to set the master address and _allowances of the _pair contract to the maximum value. This critical vulnerability enables an attacker to drain the Coin31 token pool.
Lessons Learned
For contracts managing token approvals or holdings, even minor errors can lead to significant security vulnerabilities. Conducting a security audit before deploying contracts in a production environment is critically important.