Compound V2 Forked Vulnerability - $20M Sonne Finance Hack
Introduction
In a recent incident, Sonne Finance, a decentralized lending protocol, fell victim to a sophisticated attack resulting in the loss of approximately $20 million in cryptocurrencies. The attacker exploited a known vulnerability in Compound v2 forks, highlighting the importance of robust security practices in DeFi protocols.
Incident Overview
Attack Target: 0xe3b81318b1b6776f0877c3770afddff97b9f5fe5
Attacker Address: 0xae4a7cde7c99fb98b0d5fa414aa40f0300531f43
Attack Transactions: https://optimistic.etherscan.io/tx/0x9312ae377d7ebdf3c7c3a86f80514878deb5df51aad38b6191d55db53e42b7f0
Timeline
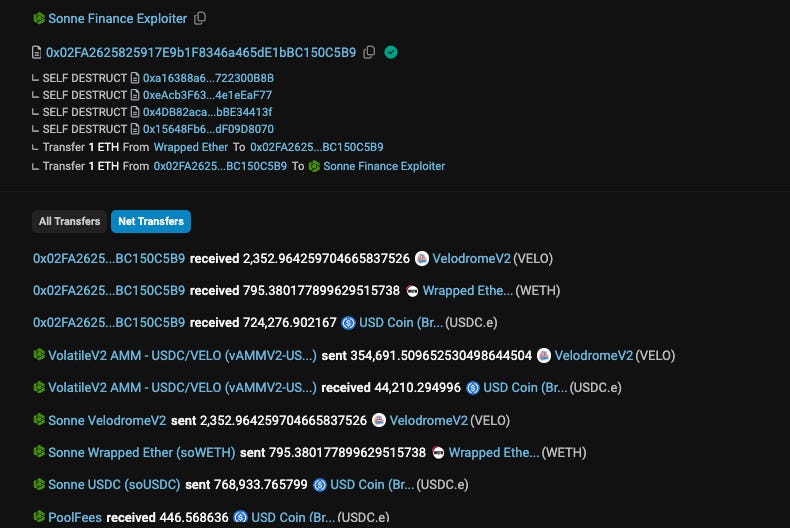
On May 14, around 10:00 PM +UTC, Sonne Finance was ongoing attack.
Within 25 minutes, the hacker had stolen $20 million in WETH, Velo (VELO), soVELO, and Wrapped USDC (USDC.e).
After the attack the Sonne Finance have reached out to the exploiter via on-chain message:
Decoding
On May 4, 2024, the team initiated Sonne Improvement Proposal 15 to introduce VELO, Velodrome Finance's native coin, to their market. After 2.3 million SONNE tokens voted in favor of the proposal, transactions were planned on the multisignature wallet. The attacker waits for a new market with empty liquidity before beginning the hack.
Step by step
Wait for a new market with empty liquidity deployed.
Mint the smallest cToken.
Donate a large underlying tokens to inflate the exchange rate(*).
Borrow a different asset with the manipulated exchange rate.
Burn cToken to recover donation.
(*) Donation attack: Directly transfer (donate) VELO Token to the soVELO contract, changing the exchangeRate, allowing the attacker to lend out approximately 265 WETH with only 1wei soVELO as collateral.
How the Exchange Rate is manipulated?
In short: exchangeRate = (totalCash + totalBorrows - totalReserves) / totalSupply
When attacker donates by directly transfer to cToken contract, the balance of underlying token is increased (totalCash is increased). It causes the function to return the incorrect value.
In a result, the health check always return true when attacker borrows all WETH and USDC available in the protocol.
Conclusion
For more about mitigation: Hundred Finance Exploit and Compound v2 - Compound Community Forum
During the design and development phases of the project, it is essential to uphold the integrity and rigor of the underlying logic. This involves addressing issues related to deposits, pledges, updating state variables, and managing the trade-offs in multiplication and division calculations. To ensure the logic is comprehensive and free of loopholes, it is important to consider as many scenarios as possible.