Convergence incident - How a simple vulnerability caused a $210K loss
On August 1, 2024, the CvxRewardDistributor contract of the Convergence-Fi project was exploited, resulting in a loss of approximately $210,000. Let's examine the details of how this attack took place.
Overview
Attacker address:
https://etherscan.io/address/0x03560a9d7a2c391fb1a087c33650037ae30de3aa
Attack transaction: https://etherscan.io/tx/0x636be30e58acce0629b2bf975b5c3133840cd7d41ffc3b903720c528f01c65d9
Vulnerable contract (CvxRewardDistributor under TransparentUpgradeableProxy): https://etherscan.io/address/0x2b083beaac310cc5e190b1d2507038ccb03e7606
Exploit analysis
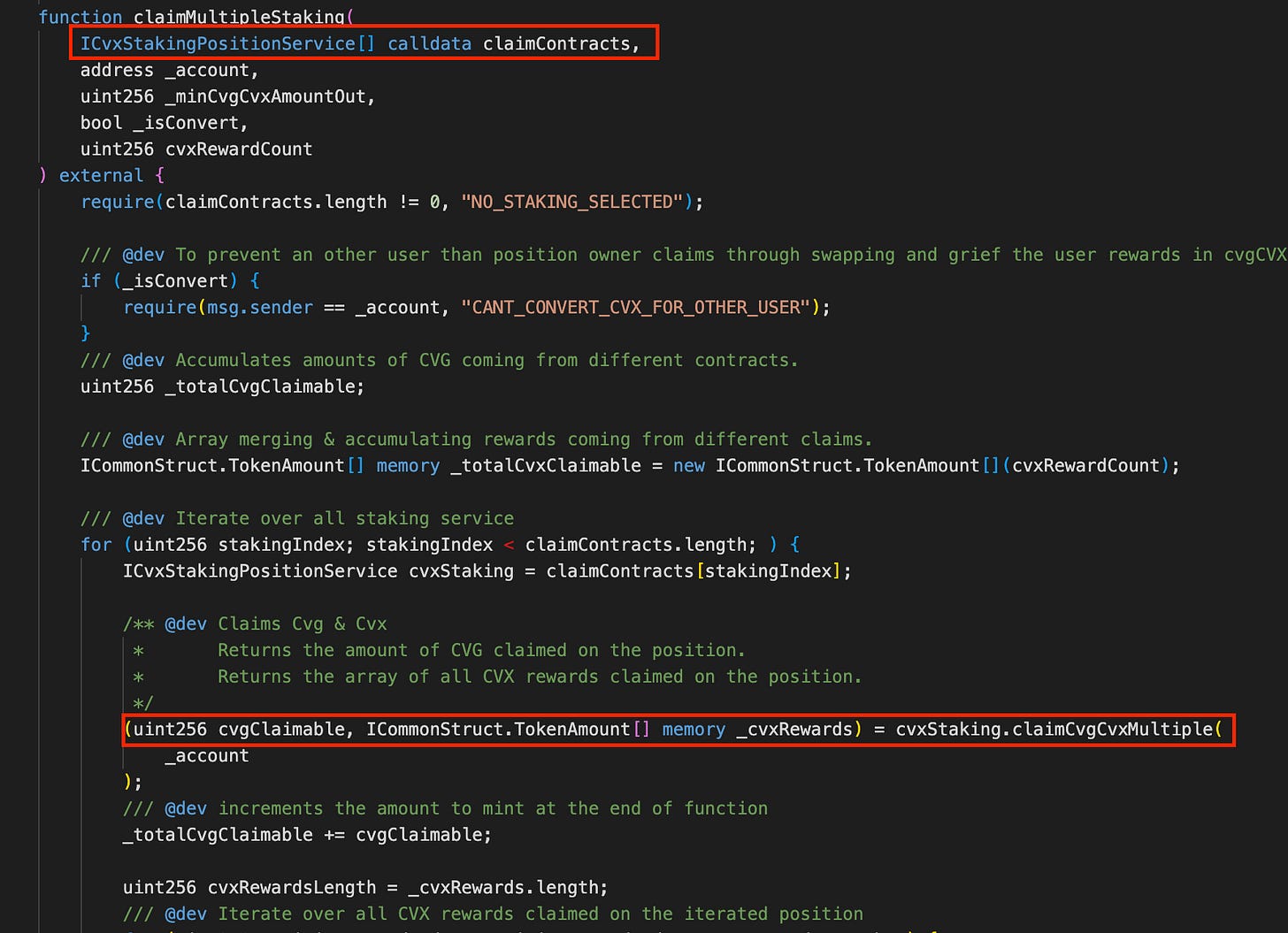
Looking at the attack transaction, we can see that in the claimMultipleStaking call, the attacker tried to inject his own newly created contract into the claimContracts parameter.
After digging deeper into the source code of the CvxRewardDistributor contract, we can see that the claimContracts parameter is not validated. Therefore, if the attacker injects his own controlled addresses into the claimMultipleStaking() function, he can manipulate the cvgClaimable variable, dramatically increasing the amount of CVG tokens that will be minted.
After the attack, 58 million CVG tokens were minted and swapped to WETH, which is approximately $210,000.
Conclusion
The attack is simple, yet severely critical. These types of vulnerabilities can easily be detected and prevented from the beginning with proper code review and auditing processes.
If you want to learn more about how real-world Web3 attacks are performed and how to trace them on-chain, check out our training at Bangkok HITB 2024. This advanced Web3 smart contract security course will cover various real-world attack types and provide common strategies to secure your protocol effectively.