Cozy Protocol Incident
On August 29, 2025, Cozy Finance was exploited through a vulnerability on the OP Mainnet Network, resulting in the loss of approximately $427,000. Let’s take a closer look at how the attack was carried out.
Original Attacker : https://optimistic.etherscan.io/address/0xce196f0a4f0c08e152ae66ecbc06675f44f68e66
Vulnerable Contract : https://optimistic.etherscan.io/address/0x562460d8cfb40ada3ea91d8cf98eaf25d53d53d8
Attack Tx : https://optimistic.etherscan.io/tx/0x71e72cae2149920bc89ae3287edf8c7e65d454d7fd5e24b590c1b4ea36c0a517
Analysis
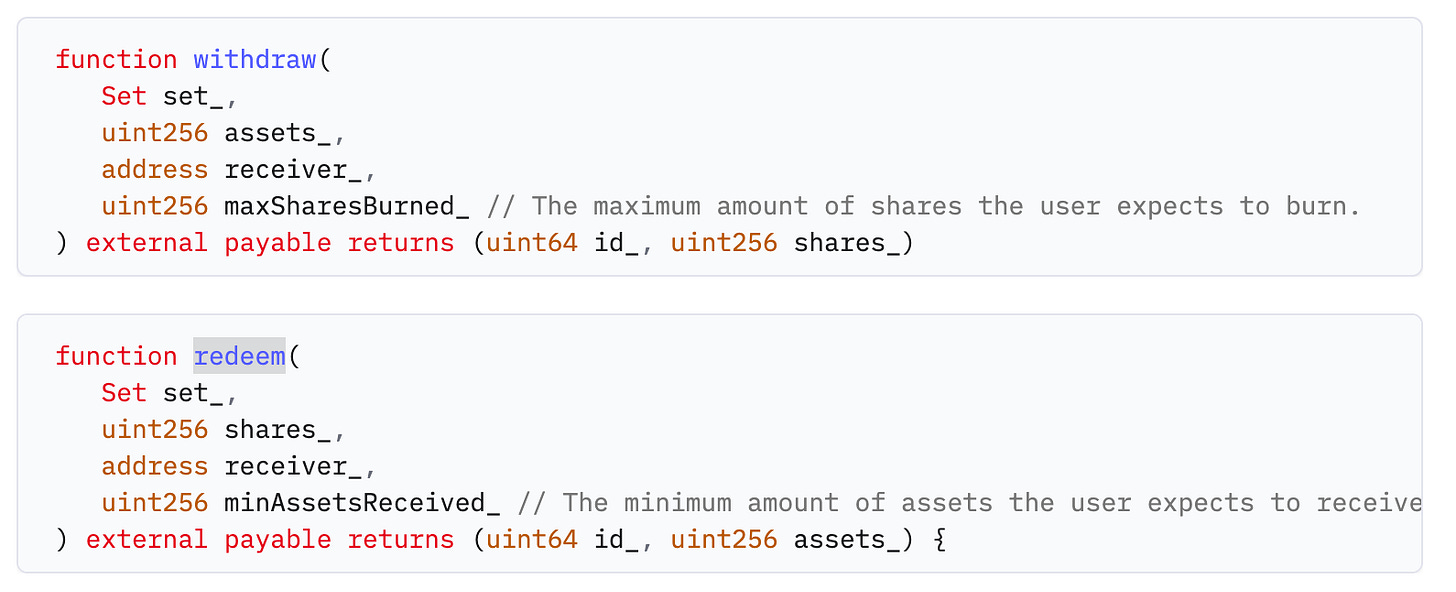
Cozy is an open-source protocol for automated, trust-minimized Protection Markets. Protection Markets let you provide and receive protection against predefined conditions-like losing funds due to a smart contract hack. Anyone can create and use Protection Markets. Users can use CozyRouter to queue withdrawals of assets or redemptions of shares. The recommended way to programmatically queue these actions is to call withdraw or redeem.
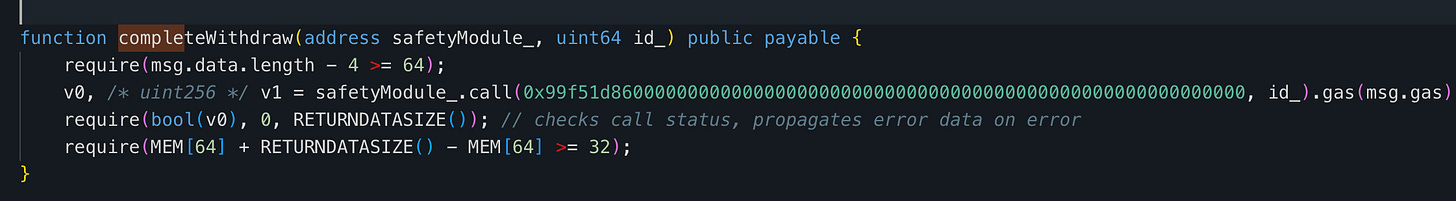
The user completes the withdrawal of assets or redemption of shares by calling completeWithdraw or completeRedeem. Both methods require an id_ argument, which is included in the RedemptionPending event emitted when the redemption is queued.
On August 28, a victim called redeem for approximately $376,661 with id_ = 6. However, the completeWithdraw function does not verify the caller’s identity.
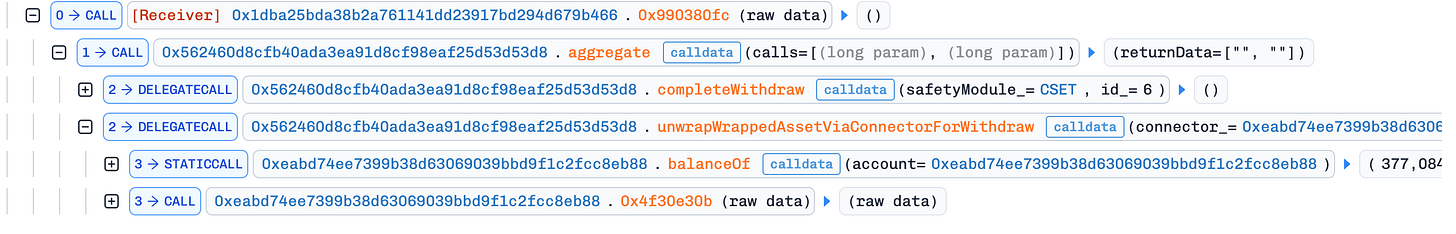
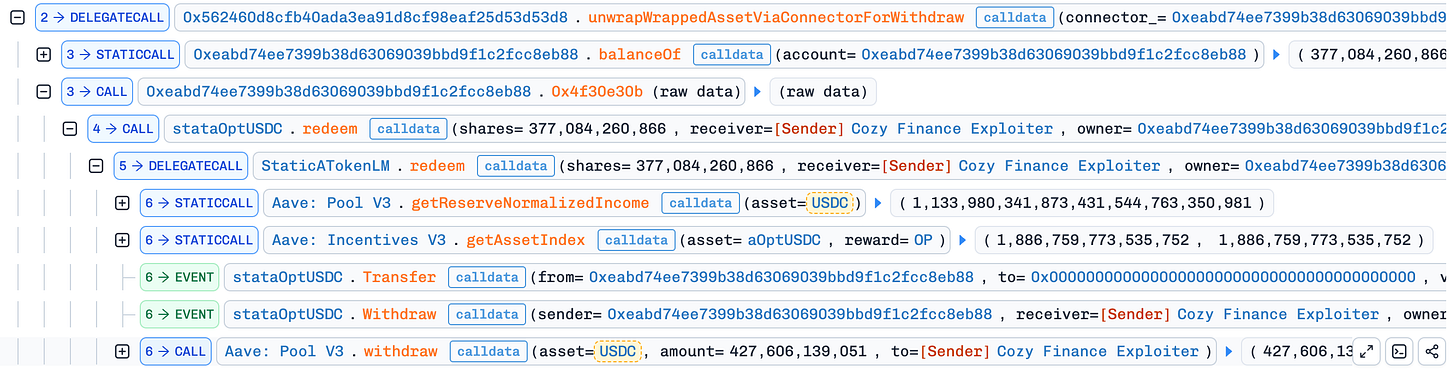
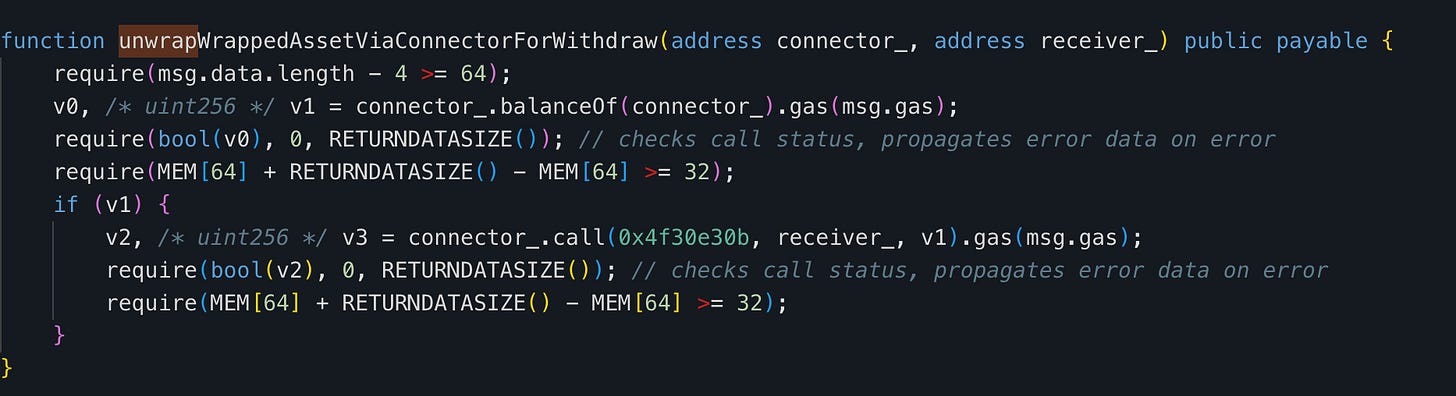
An attacker only needs to provide user’s redemption ID. The attacker used a different account to call completeWithdraw with the same id_ as the victim, then called the unwrapWrappedAssetViaConnectorForWithdraw function.
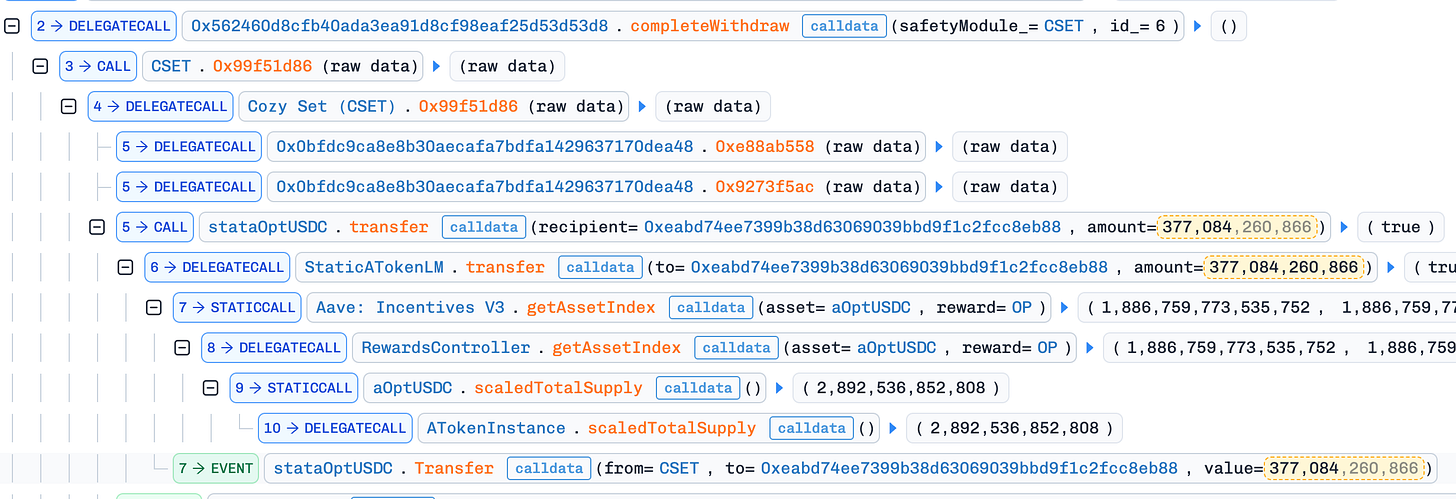
The completeWithdraw function likely used shares from the victim’s redemption to withdraw stataOptUSDC to the connector.
The unwrapWrappedAssetViaConnectorForWithdraw function automatically converted yield-bearing tokens (like aOptUSDC) into USDC when withdrawing to the attacker.
This incident occurred because the function didn’t validate the receiver_ argument. The total loss was approximately $427,000.
Conclusion
This incident serves as a reminder that even well-designed protocols can be compromised by subtle oversights. Developers must thoroughly audit all user input and ensure that sensitive actions can only be performed by authorized parties. For users, it underscores the need to stay informed about the security practices of DeFi platforms and to exercise caution when interacting with new protocols.