DCF token hack analysis
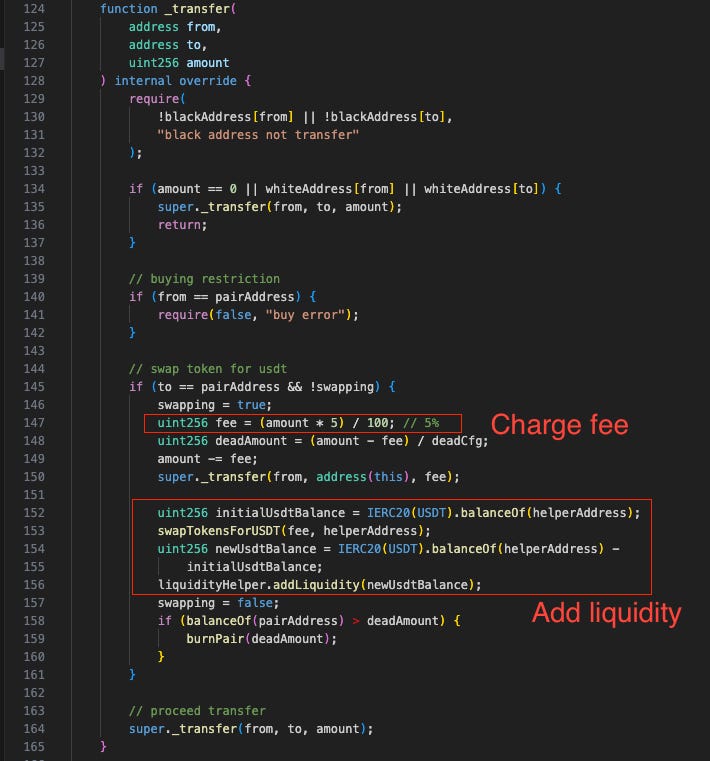
The DCF Token suffered an exploit on November 24, 2024, resulting in an estimated loss of approximately $400K at the time of the exploit. The root cause of the exploit was the lack of slippage protection when charging fee to add liquidity back to the pair.
Overview
Attacker: https://bscscan.com/address/0x00c58434f247dfdca49b9ee82f3013bac96f60ff
Vulnerable Contract: https://bscscan.com/address/0xA7e92345ddF541Aa5CF60feE2a0e721C50Ca1adb
Transaction attack: https://bscscan.com/tx/0xb375932951c271606360b6bf4287d080c5601f4f59452b0484ea6c856defd6fd
Exploit Analysis
The DCF Token contract charges a 5% of the tokens as fee when selling and automatically sells the fee into USDT and buy DCT to add to the USDT-DCT liquidity pool.
The problem is that all the buy/sell operations in the contract lack slippage price protection (the minimum received amount is set to 0). The attacker manipulates the price of DCT and DCF by buying the tokens with a flash loan, driving the price up significantly. They then transfer a small amount of DCF tokens into the pair to trigger a fee, which is later sold for USDT.
Because there is no slippage protection, the contract swaps USDT to DCF at an extremely inflated price and adds liquidity back to the pair. The attacker then sells all the DCF and DCT tokens they bought at the higher price, pay back the flashloan and take profit.
Lesson learned
Slippage protection is very important when using the Uniswap protocol. Contracts that automatically buy or sell tokens without slippage protection are attractive targets for exploiters, as they can easily perform sandwich attacks on automated transactions to take advantage of price fluctuations for profit. Always remember to use slippage protection when swapping, and avoid implementing automatic buy/sell functions in contracts whenever possible.
It is strongly recommended to conduct a security audit, whether it is a simple ERC20 contract with some minor changes or a complex DeFi protocol with hundreds of thousands of lines of code.