DeltaPrime exploit analysis
On November 11, 2024, DeltaPrime fell victim to a sophisticated exploit targeting both the Arbitrum and Avalanche networks, resulting in losses totaling approximately 4.75 million. This incident marks the platform’s second major security breach, following a 6 million exploit in September.
Overview
Attacker address: 0xb87881637b5c8e6885c51ab7d895e53fa7d7c567
Attacker contract: 0x0b2bcf06f740c322bc7276b6b90de08812ce9bfe
Attack transaction: 0x6a2f989b5493b52ffc078d0a59a3bf9727d134b403aa6e0bf309fd513a728f7f
Vulnerable contracts:
TraderJoeV2ArbitrumFacet: 0xd6002c3f5a53107cb11cc0b8de5f76f61f18cb5d
SmartLoan instance: 0xf81b4381b70ef520ae635afd4b0e8aeb994131fb
Hack Analysis
First, let’s examine the claimReward() function in the TraderJoeV2ArbitrumFacet contract. This function allows users to submit an arbitrary pair parameter, which is then used without proper validation. As a result, an attacker could exploit this by submitting a malicious pair, potentially causing unintended behavior or disrupting the system—such as enabling price manipulation.
Second, consider the swapDebtParaSwap() function in the IAssetsOperationsFacet interface, which the smart loan instance inherits. This function includes a _repayAmount parameter that is passed and recalculated twice before being sent to the _processRepay() function. Due to missing validation, the _repayAmount can be significantly altered between function calls, potentially leading to unexpected and severe consequences.
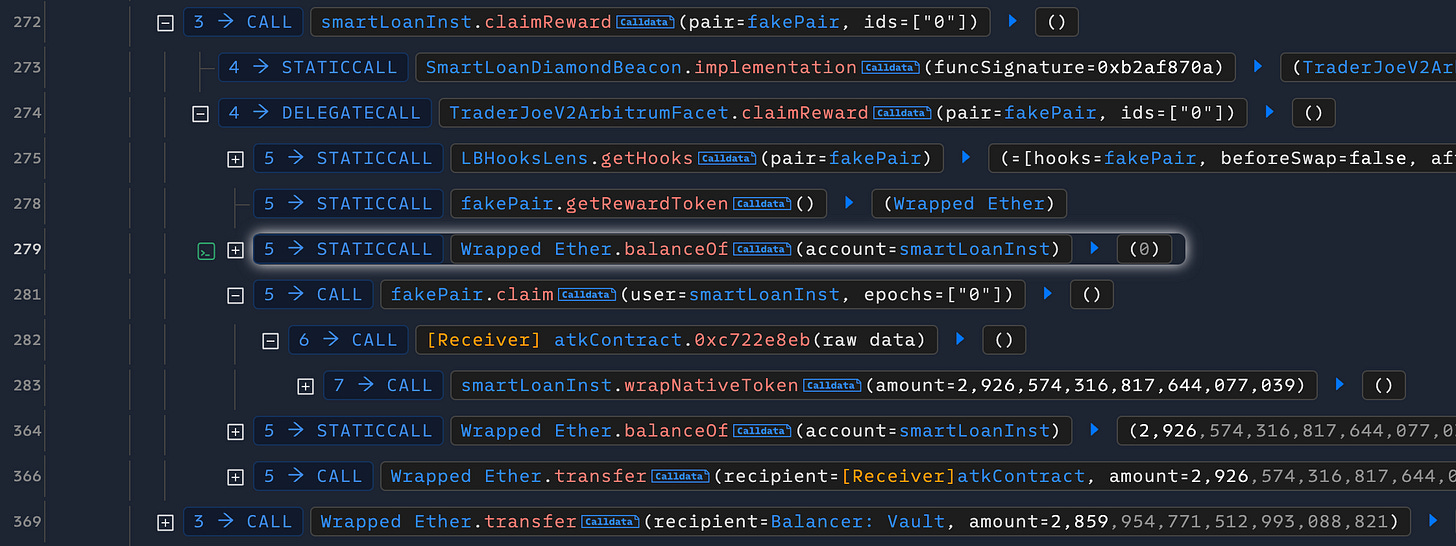
To exploit these vulnerabilities, the attacker first borrows 2,859 WETH via a flash loan (line 3). In the receiveFlashloan() callback, the attacker converts WETH to ETH (line 16) and transfers the ETH to the flash loan instance (line 20). Next, the attacker calls swapDebtParaSwap() on the flash loan instance, carefully setting the _repayAmount parameter to zero and _borrowAmount parameter to approximately 66 WETH (line 21).
After that, the attacker calls claimReward() on the flash loan instance with a malicious pair (line 272). This dummy pair is crafted to “swap” ETH back to WETH, tricking the system into believing that the 66 WETH mentioned earlier was the “swapping fee”.
Finally, the attacker repays the flash loan and successfully siphons 66 WETH from the DeltaPrime WETH pool.
To mitigate against the attack, the claimReward() was updated to accept only whitelisted pairs:
Conclusion
Input validation is crucial in software development, particularly for security-critical applications like smart contracts, because it ensures that only properly formatted and expected data is accepted. To prevent such issues, we strongly recommend implementing robust audit processes from the initial stages of development and throughout the entire lifespan of the project. Regular security audits, code reviews, and vulnerability assessments should be standard practice to identify and address potential risks before they are exploited.