Fire Token incident analysis
On October 1, 2024, Fire Token was exploited, resulting in a loss of approximately $20,000 at the time of writing. Let’s examine the details of how this attack took place.
Attacker : https://etherscan.io/address/0x81f48a87ec44208c691f870b9d400d9c13111e2e
Attack Contract : https://etherscan.io/address/0x9776c0abe8ae3c9ca958875128f1ae1d5afafcb8
Vulnerable Contract : https://etherscan.io/address/0x18775475f50557b96C63E8bbf7D75bFeB412082D
Attack Tx : https://etherscan.io/tx/0xd20b3b31a682322eb0698ecd67a6d8a040ccea653ba429ec73e3584fa176ff2b
Exploit analysis
Fire Token is an ERC20 Token. The special thing about Fire Token is that it has the token swap functionality integrated from Uniswap v2. Additionally, the _transfer() function has also been modified to use that functionality.
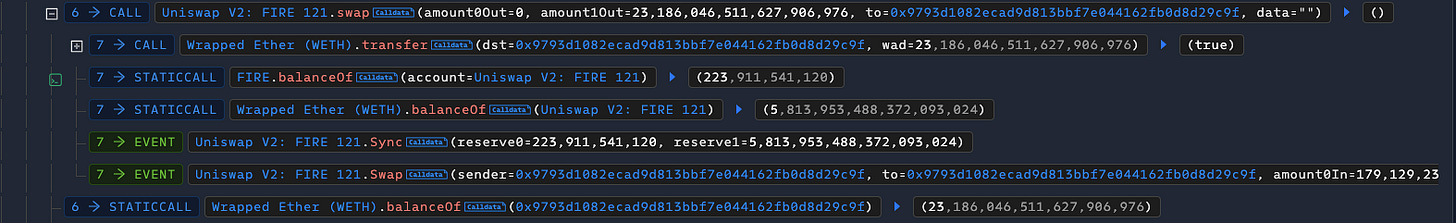
But the issue here is that the _transfer() function is vulnerable when transferring tokens to a Uniswap pair. If the user transfers tokens to a Uniswap pair, the balance of the Uniswap pair is automatically decreased and the sync() function is called right after that. This can happen because the system calculates the sell amount based on the transfer amount and tax amount and after that, the system transfers that sell amount to the dead address.
Any user can transfer multiple Fire tokens to a Uniswap pair. With that condition in _transfer(), the amount of the Uniswap pair will decrease, leading to a reduction of reserve value. With this flow, the attacker first exchanged 20 ETH to Fire, and he transferred all of the received tokens to the Uniswap pair. Because an amount of Fire was transferred to dead address, the reserve value of Fire got smaller too.
After that, the attacker used swap() of the Uniswap pair and got more tokens based on the discrepancy in the reserve value. He repeated this action until be reserve value dropped to the minimum value.
With this exploit, the attacker gained approximately 8.45 ETH (about 20,000 USD).
Conclusion
By sharing our insights on Fire Token exploit, this highlights the critical need for thorough security audits and robust smart contract design to prevent manipulation, especially in decentralized exchanges. Effective risk mitigation strategies must be in place to safeguard user funds in DeFi systems, as even minor flaws can result in significant financial losses.