Inside the Impermax V3 Hack
Overview
In April 2025, Impermax V3 suffered a flash loan attack, resulting in approximately $300,000 stolen from the protocol's liquidity pools. The attacker exploited a flaw in the protocol's calculation of collateral value for Uniswap V3 LP positions. The attack followed a systematic approach: first manipulating the LP pool's price tick, then accumulating substantial fees through swaps, borrowing against the LP position, incorrectly reinvesting fees, and finally triggering a self-liquidation of the position. This sequence caused the position value to plummet, forcing the protocol into bad debt and allowing the attacker to extract funds without risk.
Background on Impermax V3
Impermax V3 is a decentralized finance (DeFi) protocol built for liquidity providers and market makers. It allows users to borrow against their liquidity provider (LP) tokens, enabling them to leverage their positions. This permissionless protocol helps users optimize their risk-reward balance through leveraged yield farming while maintaining their LP token holdings.
Technical Analysis of the Exploit
Incident Overview
Date: April 26, 2025
Attacker Address: https://basescan.org/address/0xE3223f7E3343c2C8079f261D59ee1e513086C7C3
Attack Contract: https://basescan.org/address/0x98E938899902217465f17CF0B76d12B3DCa8CE1b
Root Cause
The Impermax V3 hack exploited a critical flaw in the protocol's valuation of uncollected Uniswap V3 fees as collateral. By assigning full value to pending fees, the protocol created a vulnerability that allowed the attacker to generate artificial fees through manipulated swaps in a low-liquidity pool. When these fees were auto-compounded at extreme price ticks, their value collapsed dramatically. The attacker then used the restructureBadDebt function to bypass liquidation procedures and retain the borrowed funds. This exploit revealed three core weaknesses: fee overvaluation, flawed reinvestment logic, and inadequate liquidation controls - exposing design flaws in how the protocol handled edge-case scenarios rather than issues in its mathematical foundations.
Attack Flow
The attacker exploited the Impermax V3 platform through multiple transactions. This attack flow analysis is based on one of these transactions: 0x14ea5b572a01234c9499174ada90d6a20af016749458297a8b071d8271f3ed77
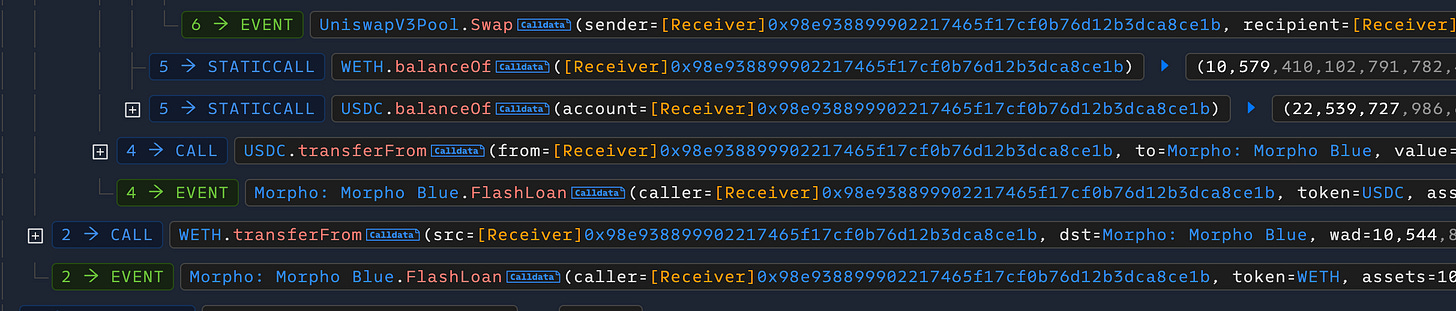
The attack began when the threat actor obtained a large flash loan from the Morpho platform to fund the exploit.
Next, they opened an Impermax V3 collateral position using LP tokens from a low-liquidity Uniswap V3 pool. The attacker then artificially manipulated the price range of the pool and executed multiple swaps to generate and accumulate fees on their LP position within this manipulated range.
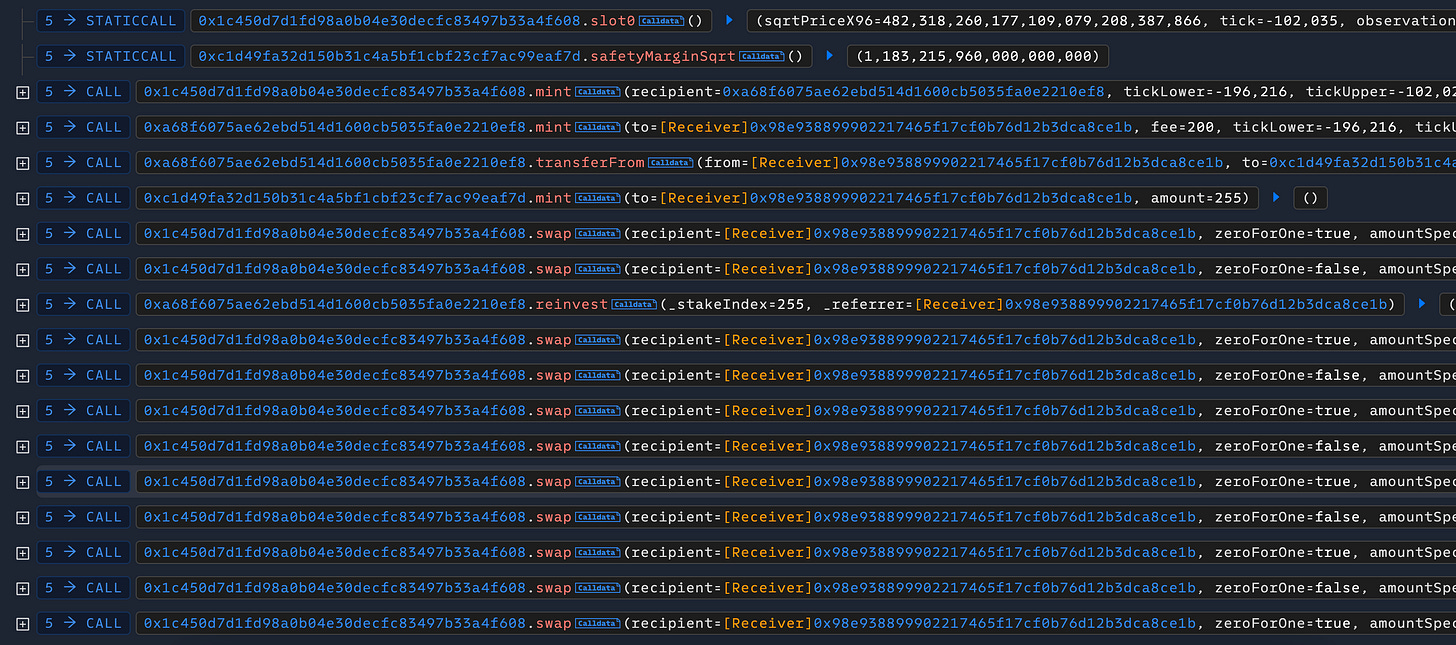
The attacker used the LP tokens, including the uncollected fees, as collateral to borrow assets from the Impermax protocol. They then triggered the reinvest function, which auto-compounded the accrued fees at an incorrect tick. This caused the position's true value to plummet once the price normalized—a classic example of impermanent loss.
Next, the attacker shifted the price back toward the current tick, causing the collateral value to plummet while maintaining possession of the borrowed assets. By executing the restructureBadDebt function, the attacker bypassed normal liquidation processes and closed the position, effectively transferring losses to the lenders while retaining the borrowed funds.
Finally, the attacker repaid the flash loan and secured their profits from the exploit. They then transferred the stolen funds through multiple addresses and transactions to obscure the money trail.
Mitigation
The mitigation strategy for the Impermax V3 attack tackles key vulnerabilities while strengthening protocol resilience:
Implement a more precise position valuation algorithm that accurately accounts for both liquidity and undistributed fees, ensuring proper conversion into future liquidity.
Add price verification checks between Uniswap V3 pool and oracle prices, preventing manipulation by requiring prices to stay within safe margins of each other.
Enhance fee reinvestment logic to ensure appropriate parameter adjustments when compounding fees, directing liquidity to suitable price ranges to prevent impermanent loss-based self-liquidation.
Revamp the bad debt handling mechanism to trigger actual liquidations instead of simply rewriting debt records, preventing loss distribution among lenders.
Perform thorough testing of the revised valuation and liquidation algorithms, focusing particularly on edge cases, to enhance security across this complex DeFi protocol with its multiple dependencies.
Together, these measures improve how liquidity position valuations and bad debt are handled, reducing exploitable vulnerabilities and strengthening overall protocol security.