Lack of Access Control to Incidents
On October 29, 2025, an unknown project was exploited through a vulnerability on the custom logic, resulting in the loss of approximately $218,000. Let’s take a closer look at how the attack was carried out.
Original Attacker : https://basescan.org/address/0x2a49c6fd18bd111d51c4fffa6559be1d950b8eff
Vulnerable Contract : https://basescan.org/address/0xc0ffee479e4cd49eafba87449225e17c53251226
Attack Tx : https://basescan.org/tx/0x4449114ceaedd11e8f1363c5e53507198323a63cb6958dc26078fc016d0d4b27
Analysis
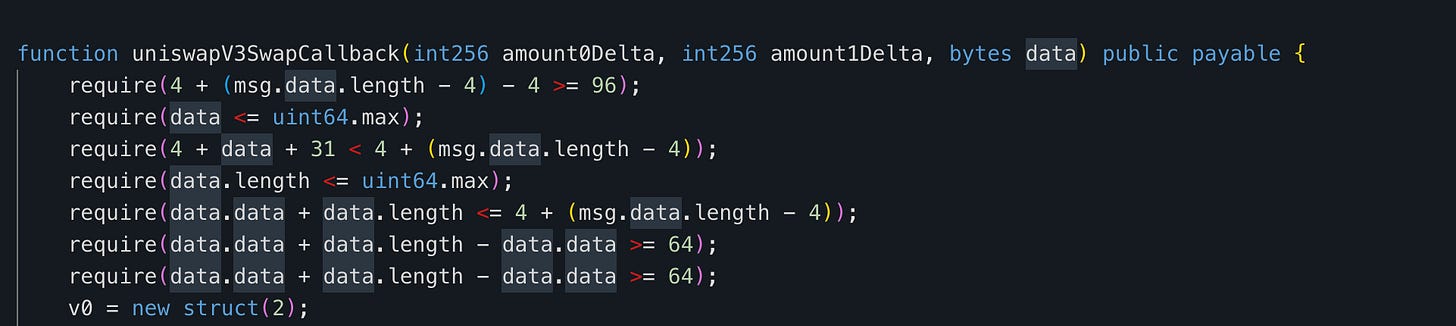
The project re-implements the uniswapV3SwapCallback. When the pool triggers this callback, the manager contract sends the required input tokens to the pool to complete the swap. The pool then performs the exchange and transfers the output tokens back to the manager contract, which subsequently delivers them to the user. Thus, the manager contract acts as an intermediary between users and pools during the swap process.
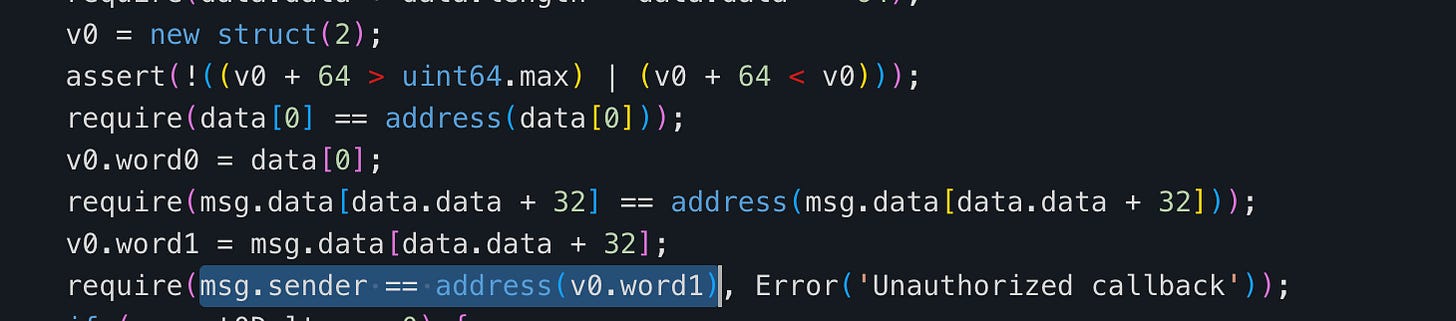
However, the function checks the msg.sender against the data parameter instead of verifying whether the msg.sender is the pool. This allows anyone to call this function with data that includes their own address.
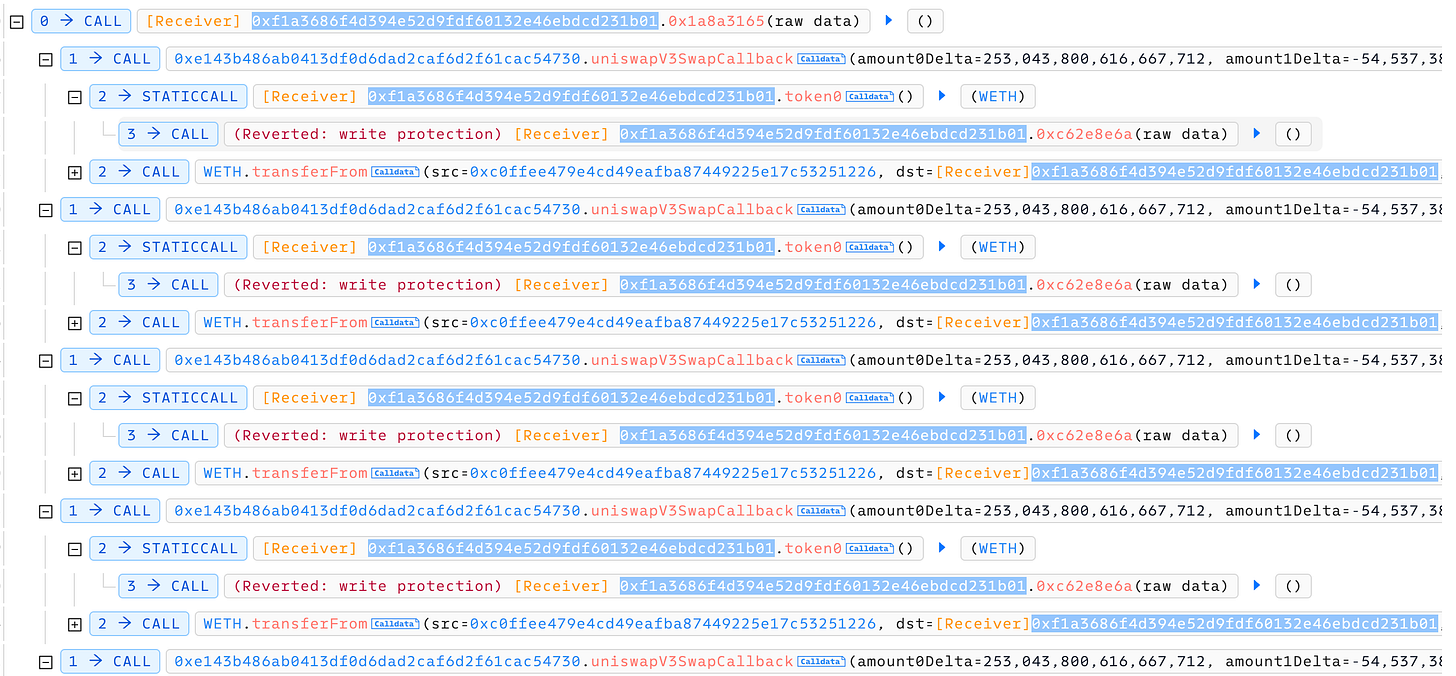
The attacker exploited this vulnerability to launch a sophisticated attack against the protocol. They deployed a malicious smart contract specifically designed to repeatedly call the uniswapV3SwapCallback function in a loop, manipulating the callback mechanism to their advantage. Through this exploit, the attacker was able to drain funds from the protocol, ultimately walking away with approximately $218,000 worth of WETH (Wrapped Ethereum). This incident highlights the critical importance of implementing proper access controls in callback functions to prevent unauthorized execution.
Conclusion
This incident reminds us that even well-designed protocols can be compromised by subtle oversights. Developers must thoroughly audit all user input and ensure only authorized parties can perform sensitive actions. For users, this highlights the importance of staying informed about DeFi platform security practices and exercising caution when interacting with new protocols.