Miner Project Attacked by Vulnerabilities in ERC-X Token Standard
The Miner project has been attacked by exploiting a vulnerability in their own implementation of the ERC-X, which is a new experimental token standard with the ambition of allowing the use of multiple standards such as ERC20, ERC404, ERC721, ERC721A, etc., in one. The estimated total value of the exploited funds is approximately $460,000.
Overview
Attacker:
https://etherscan.io/address/0xea75aec151f968b8de3789ca201a2a3a7faeefba
Attack transaction: https://etherscan.io/tx/0x75e3aeb00df69882a1b15d424e5e642650326ca3b923d7fd1922d57c51bc2c78
Vulnerable contract (MINER token): https://etherscan.io/address/0xe77ec1bf3a5c95bfe3be7bdbacfe3ac1c7e454cd
Exploit analysis
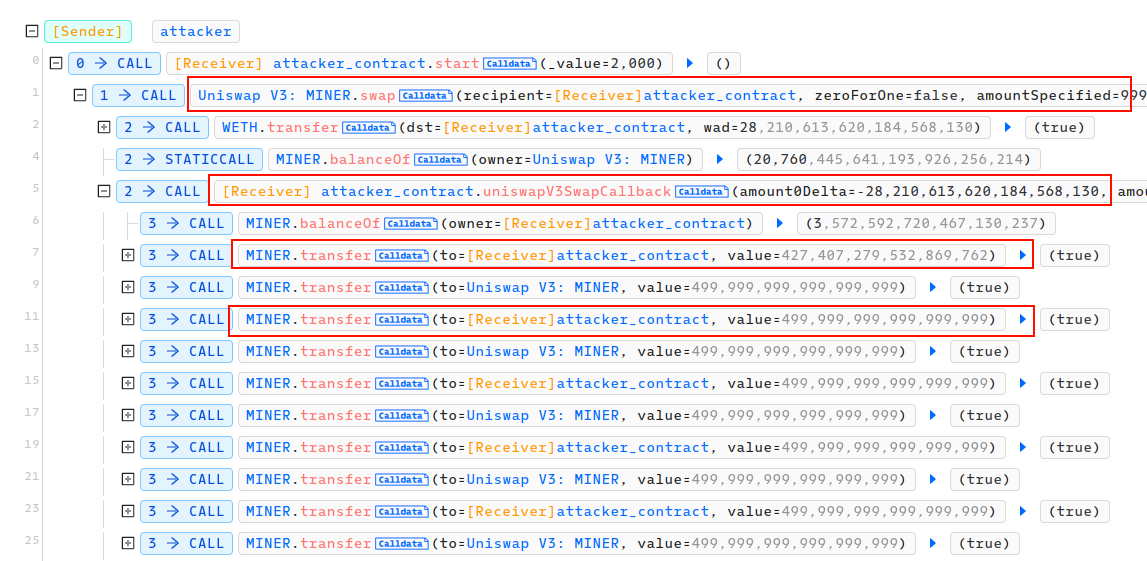
The issue occurs within the _update function of the ERCX contract (triggered by token transfer), where we can see an incorrect update of the recipient’s balance if the two addresses from and to are the same. It means that if the attacker try to transfer MINER tokens to his own address, the value of _balances[to] will be updated with the old value of toBalance instead of balances[to]. Consequently, the attacker's balance will be increased by the transferred amount. This issue is absolutely critical.
Using the above vulnerability, the attacker attempted to drain all the WETH tokens inside the Uniswap V3 pool of the WETH/MINER pair as follows:
Made a call to
UniswapV3Pool.swap()to swap 999.99 (~1000) MINER to WETH.Inside the
uniswapV3SwapCallbackhook (where we need to transfer the input tokens to the pool make our swap successful), the attacker repeatedly transferred MINER tokens to himself to increase his MINER token balance (using the bug), sent them to the pool, and then successfully drained all WETH tokens inside the pool.
Conclusion
Creating new token standards can be necessary in some cases. However, since the token contract is one of the most critical components in any web3 projects, both the design and implementation should be carefully audited to avoid critical issues like this.