MSCST Flash Loan Attack: Price Manipulation Exploit
$130K BSC Drain: Flash Loan Unlocks Unprotected Rewards
Overview
On December 29, 2025, the MSCST smart contract on Binance Smart Chain (BSC) was exploited through a flash loan attack, resulting in the theft of approximately 149 BNB (~$130,000). The attacker exploited a critical vulnerability in the releaseReward() function to manipulate the GPC/WBNB liquidity pool price on PancakeSwap and extract profit in a single transaction.
Technical Analysis of the Exploit
Incident Overview
Date: December 29, 2025
MSCST Smart Contract: 0xccd04073f4bdc4510927ea9ba350875c3c65bf81
Exploiter Address: 0xB0720D8541cD2b6fC35cCC39ec84e84383A7000b
Attack Transaction: 0x53fe7ef190c34d810c50fb66f0fc65a1ceedc10309cf4b4013d64042a0331156
Root Cause
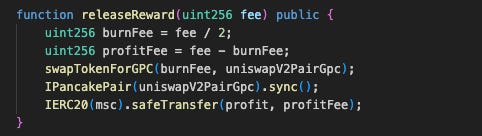
The MSCST Smart Contract contains a releaseReward function that accepts an amount parameter. The function swaps half of this amount from MSC tokens to GPC tokens, then transfers the swapped GPC directly to the GPC/WBNB pool. However, the function lacks access control, allowing anyone to call it. The attacker exploited this vulnerability using flash loan techniques to manipulate the GPC/WBNB pool price and extract profit
.
Attack Flow
Below are the detailed steps describing how the attacker exploited the access control vulnerability and flash loan technique for profit.
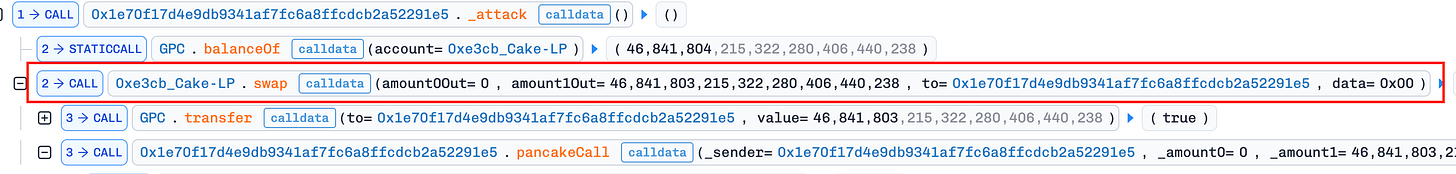
Flash Loan Liquidity: Borrowed 46.8M GPC tokens from a BSC flash loan provider (no collateral needed due to atomic repayment).
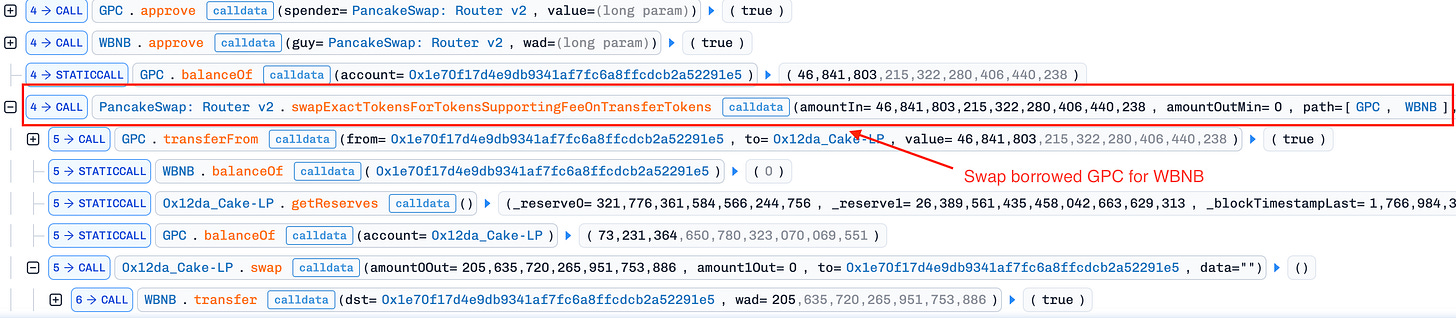
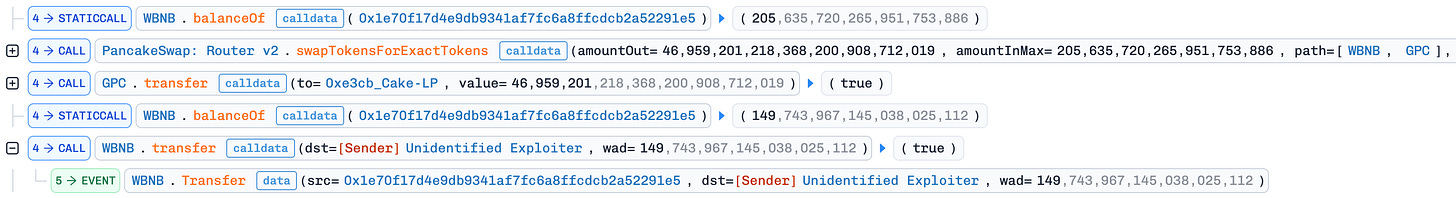
Price Manipulation (Push Down): Swapped the entire 46.8M GPC for 205 BNB in PancakeSwap pool 0x12dA…8D64D9, crashing the GPC price. This maximized profit by artificially depressing the price before calling
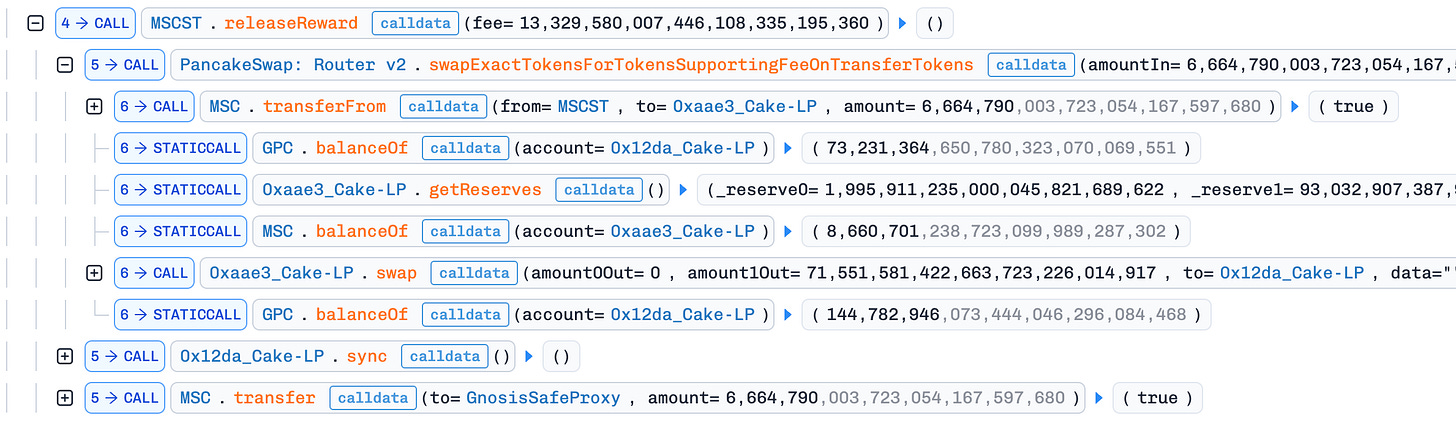
releaseRewardin the next step.Exploit
releaseReward(): The attacker invoked the unprotectedreleaseReward()function, which swapped half the MSC balance for GPC and added it directly to the GPC/WBNB pool. This drove the GPC price down further, amplifying the manipulation.Profit Extraction: After the steps above, the GPC price in the GPC/WBNB pool was artificially depressed. The attacker used the 205 WBNB obtained in step 2 to buy back GPC and repay the flash loan. Due to the suppressed GPC price, the attacker spent only ~55 BNB on the buyback and pocketed ~149 BNB (~$130K) in profit.
Lessons Learned
Gate reward functions with ACL: The public
releaseReward()function allowed anyone to trigger payouts during manipulated states. BasiconlyOwner, timelocks, or role-based access control would have blocked flash loan attacks entirely, preventing attackers from abusing internal accounting logic.Replace spot oracles with TWAP: Direct PancakeSwap reserve reads via
sync()created a trivially manipulable price feed. Protocols must use time-weighted average prices (30–60 min windows) or Chainlink oracles to filter out short-term distortions from flash loan sandwiches.Enforce slippage protection on swaps: Accepting zero minimum output enabled extreme price impacts without reverts. Every DEX operation needs realistic bounds (0.5–5% caps based on pool depth) to reject manipulative trades before they cascade into reward exploits.