Numa Incident Analysis
The Numa protocol is a decentralized platform running on Arbitrum (Ethereum L2) that brings real‑world assets on-chain through a transparent burn‑and‑mint design . Users deposit liquid‑staking tokens (e.g., Rocket Pool’s rETH) into Numa’s vaults to mint $NUMA tokens, which can be exchanged 1:1 for synthetic assets - collectively dubbed nuMoney like nuUSD, nuBTC, nuGOLD, and more . Benefits include real sustainable yield from underlying staking rewards, zero-slippage swaps among synthetics, and interest-free leverage and lending built around the non‑custodial yield-bearing model .
On August 10, 2025, the Numa protocol suffered an exploit that resulted in a loss of approximately $313,000. The attacker took advantage of a flaw in the VaultManager’s collateral valuation logic by flash-minting nuBTC. This artificially inflated the total synthetic value within the system, which in turn weakened the collateral backing of cNuma. As a result, many user accounts became under-collateralized and were liquidated, allowing the attacker to seize assets from those positions.
Overview
Attacker wallet: 0xef1df44e122872d0fef75644afc63a5c35f97674
Attacker contracts:
Numa’s contracts:
Analysis
Numa builds upon and inherits this Compound architecture, effectively forking its core lending and collateral evaluation mechanisms. However, Numa adapts the model for a broader purpose: integrating synthetic assets, liquid-staking tokens, and leveraged-long derivatives into its vault system. While the borrowing and liquidation checks are still rooted in Compound’s Comptroller and collateral-factor logic, Numa’s introduction of novel asset types - such as cNuma - adds complexity to the collateral valuation process, ultimately creating the unique attack surface that was exploited in the this incident.
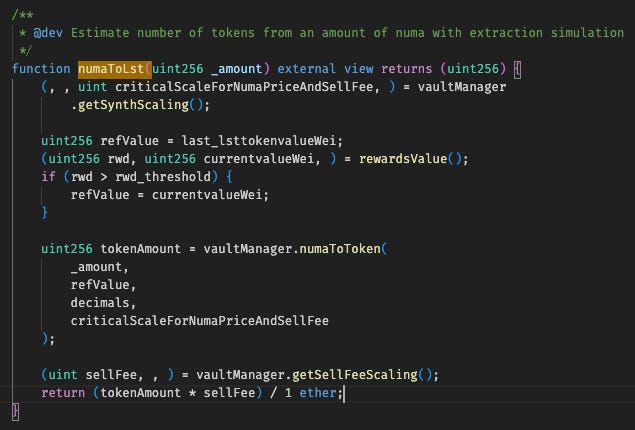
In Numa, the price of cNuma collateral is indirectly derived through a series of contract calls. The NumaVault contract computes the value via numaToLst(), which returns the result of tokenAmount * sellFee. Here, tokenAmount comes from the VaultManager’s numaToToken() function, calculated as:
In this formula, EthBalance represents the total value available in all vaults, while synthValueInEth reflects the total ETH-equivalent value of all synthetic nuTokens minted. This design ties the collateral value of cNuma directly to the relative proportion of real assets (EthBalance) versus synthetic liabilities (synthValueInEth).
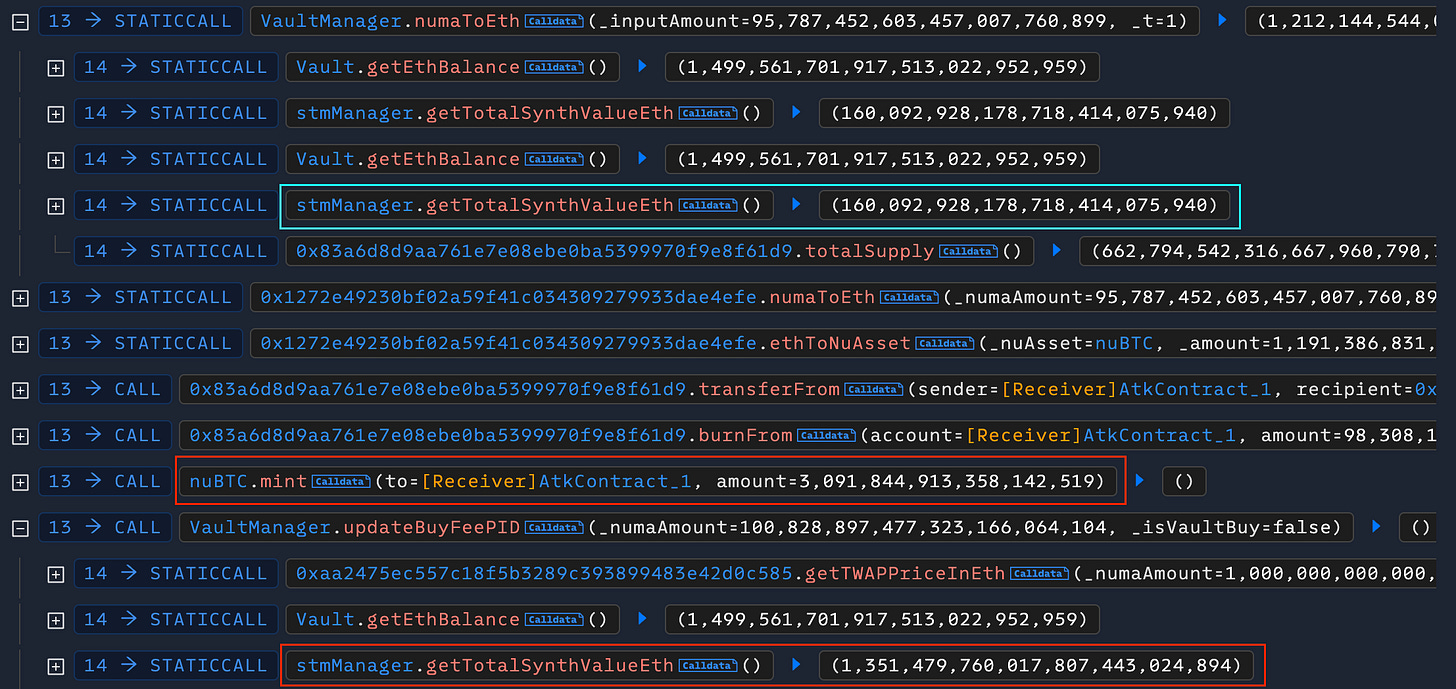
The exploit capitalized on this relationship. By flash-minting nuBTC, the attacker significantly increased synthValueInEth in a single transaction, causing the numerator (EthBalance - synthValueInEth) to shrink sharply. This reduced the calculated tokenAmount, and by extension the cNuma price, without affecting actual vault asset balances. The resulting artificial drop in collateral value triggered mass liquidations, allowing the attacker to acquire assets from undercollateralized accounts at a profit.
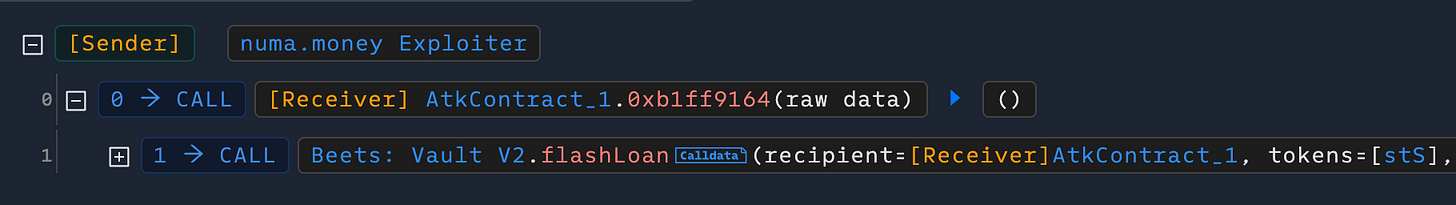
The attack began with a flash loan of stS tokens from the Beets Vault, which the attacker used to mint approximately 3.08 nuBTC. This minting action caused synthValueInEth to surge from about 160,092 to 1,351,479, bringing it close to the total EthBalance.
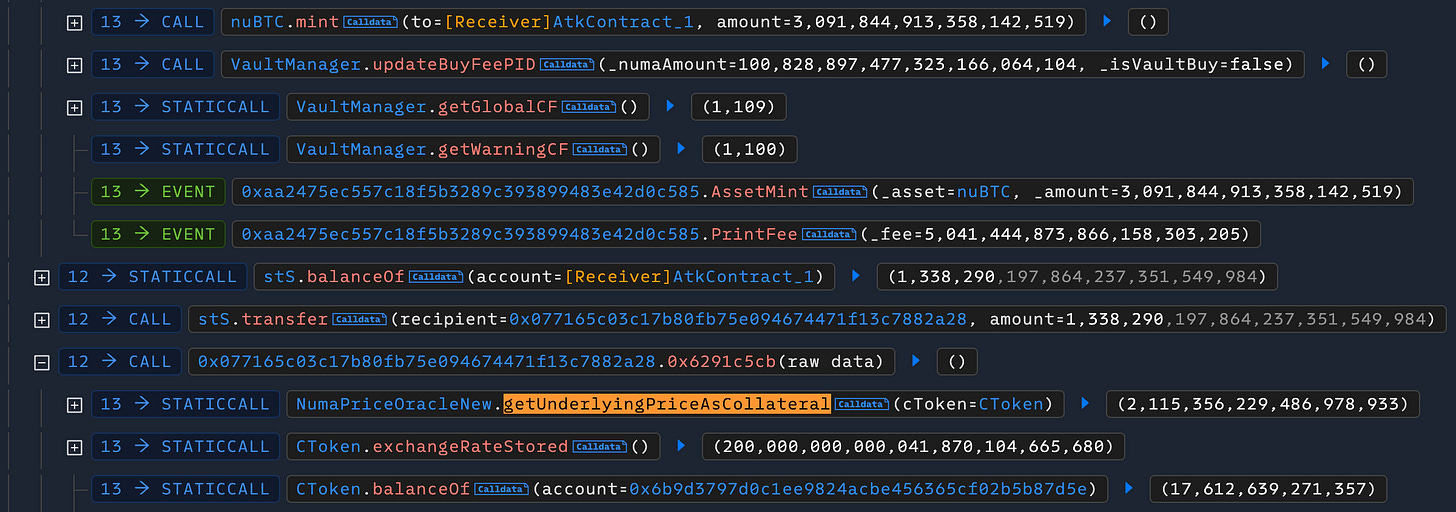
This sharp increase in synthetic liabilities drastically reduced the (EthBalance - synthValueInEth) component in the collateral pricing formula, causing a steep drop in cNuma’s valuation. As a result, the value of the underlying collateral plummeted from 7.579 to 2.115. At this point, the attacker was able to liquidate victim accounts and capture the resulting profit.
Summary
The Numa incident is a clear reminder that forking a proven protocol like Compound does not automatically inherit its security guarantees. Any modification - especially those introducing new asset types or altering core valuation logic - requires a deep and comprehensive understanding of the original protocol’s mechanics. Even subtle changes can unintentionally create exploitable attack surfaces that undermine the entire system.
To safeguard against such risks, conducting a thorough security audit is essential before deploying a modified protocol to production. This process should include stress-testing new logic under adversarial scenarios, reviewing the interplay between legacy components and new features, and verifying that no hidden dependencies can be manipulated.