Post-Mortem: Prism Protocol Liquidity Pool Burn Exploit
On December 11, 2025, at 11:54 AM UTC, Prism Protocol was exploited through improper role management that allowed a malicious contract to burn tokens directly from the PancakeSwap liquidity pair. By abusing the centralized SniperManager permission, the attacker drained liquidity and executed a highly profitable trade within a single transaction.
Incident Overview
Date: Dec 11, 2025
Platform: Binance Smart Chain (BSC)
Attacker Address: 0x24A619dCe92c38d5Fef9733f9A37050742141647
Attack Contract: 0x2E857bC277Eb049Fb4f27911e4c3498cEFC1A1dd
Prism Token Contract: 0x1284c1f20A7F0322A5E17618f764F0d3CBAcCeE9
Attack Transaction: 0xcf7cacfe38dcf090bbfcc91634de364e62ef3715fdc8d6f69e855772b0862237
Exploit Mechanics
All steps below were executed within a single transaction by the attack contract:
Purchased 67,750 PRISM from PancakePair using 0.01 BNB.
Invoked
BurnSniperTokenBoughton the PrismToken contract four times, reducing the Prism balance inside PancakePair from 485,826,708 PRISM to 480 PRISM.Sold the 67,750 PRISM obtained in step 1 back to the PancakePair, receiving 71.5 BNB, equivalent to approximately $62,000 USD at the time of the attack.
Root Cause Analysis
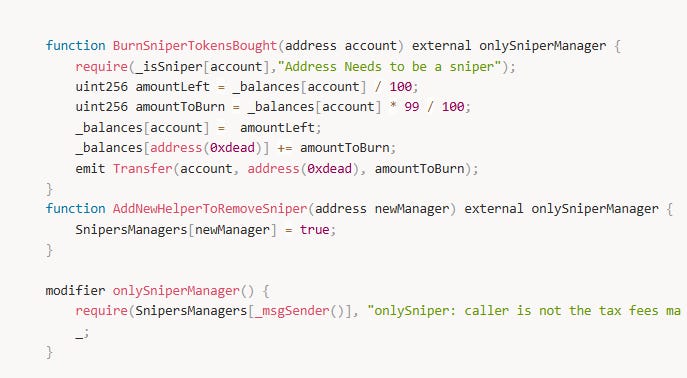
The core issue lies in how the Prism protocol allows a contract to burn tokens belonging to the PancakePair.
Specifically, the BurnSniperTokensBought function permits burning tokens from an address flagged as a sniper. While this function is protected by the onlySniperManager modifier—restricting access to authorized roles—the attacker was able to exploit role assignment rather than the function logic itself.
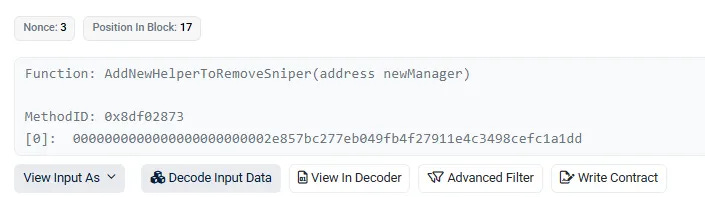
Upon reviewing Prism protocol interaction transactions, we identified transaction
0x23879edbd3366cdc774aaa72a8484b7f7ef641f68f01345764bf44d812d042a6 This transaction shows that a SniperManager role was granted to the attack contract prior to the exploit. As a result, the attacker gained permission to call BurnSniperTokensBought and burn tokens directly from the PancakePair.
Conclusion
The BurnSniperTokenBought function itself is not inherently vulnerable; it behaves as designed.
The true root cause of the attack was operational failure by the Prism protocol operator team, who mistakenly approved a malicious contract as a SniperManager.
Additionally, BurnSniperTokenBought represents a highly centralized control mechanism, which is inappropriate for a decentralized smart contract system. Granting privileged roles that can arbitrarily burn third-party balances—especially liquidity pool addresses—introduces significant systemic risk.