Exploiting Radiant Lending Pool: A Deep Dive into Attack
On the 2nd of January 2024, the Radiant Lending Pool faced a critical exploitation, resulting in the theft of $4 million by a sophisticated attacker.
Summary
On the 2nd of January 2024, at 18:53 UTC, the Radiant Lending Pool faced critical exploitation, resulting in the theft of 1900 ethers by an attacker ($4m). This breach involved using a flash loan to manipulate the liquidity index of the pool and exploit a rounding error, allowing the attacker to siphon funds successfully.
The Radiant Capital is a decentralized lending platform where users can earn interest by depositing assets and lending out other assets as collateral. The platform is built on top of the Aave protocol. The Radiant Capital is a fork of the Aave protocol with some modifications.
First of all, a pool provider init a new market with no initialized data in a pool like as the timestamp is zero at the tx 0x0e5330ad77b9b806cb9f6ea595d58552f341dbad0691e0599ab5f1caf214c247
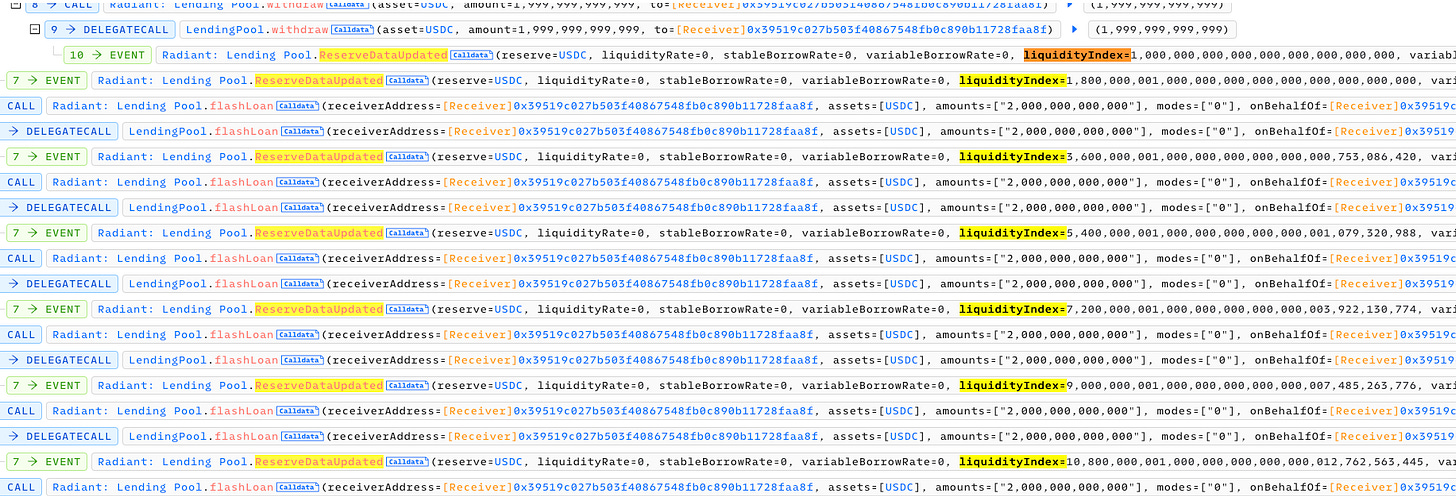
The attacker then executed a flash loan, borrowing a huge amount from the pool and promptly depositing it back. Following this, the pool provider updated the liquidity index to an extraordinarily high value (271800000000,999999999999998631966035920 *1e27), as observed in the transaction details, tx 0x1ce7e9a9e3b6dd3293c9067221ac3260858ce119ecb7ca860eac28b2474c7c9b
To maximize gains, the attacker engaged in deposit and withdrawal maneuvers, deliberately triggering a rounding error in the liquidity index calculation. This process involved depositing to mint interest at a 1:1 ratio and subsequently withdrawing to burn a small portion of the generated interest.
The fundamental issue behind the bug lies in the rounding error within the calculation of the scaled amount in the burn function of the AToken contract. This vulnerability surfaces when a new market is activated in the lending market, derived from the Compound/Aave protocols, without initializing all market properties, essentially creating an empty pool. Exploiting this vulnerability becomes relatively straightforward for an attacker.
Additionally, the exploitation leverages a well-known rounding issue present in the current Compound/Aave codebase. This particular issue has previously been exploited in the Onyx Protocol, Hundreds Finance, and Midas Capital incidents.
Technical details
The bug in question is not a novel occurrence. Rather, it is a recognized rounding issue within the Compound/Aave codebase. Although this bug has been rectified in the Compound/Aave codebase, it persists within the Radiant Capital codebase.
During the initial update, a pool provider sets both the liquidity index and variable borrow index to 1e27. The lastUpdateTimestamp is observed to be zero in the transaction recorded at block 166405628.
In the initial transaction of the hack, the attacker closely monitored and swiftly executed actions moments later at block 166405687. The attacker employed a sequence of three hacks to withdraw balances from the pool.
The attacker initiated a flash loan of 3 million USDC from the AAVE pool. Subsequently, the attacker deposited 2 million USDC into the Radiant Lending Pool. Employing another flash loan on the Radiant pool, the attacker executed withdrawals, extracting 99% of the deposited balance in each iteration. This process was repeated over 150 times, strategically manipulating the liquidity index to an exceptionally high value.
The outcome of this transaction was a manipulated liquidity index set at 271800000000.999999999999998631966035920 *1e27. This value significantly surpassed the initial 1e27 observed before the manipulative actions occurred.
In the subsequent transaction, the attacker persisted in executing a flash loan of 3.5 million USDC from the AAVE pool. The attacker deposited a precise amount of 2.718.000,000010 USDC into the Radiant pool. Additionally, the attacker borrowed approximately 906 ETH from the Radiant pool.
Each deposit operation resulted in users receiving interest in the form of rUSDCn. Subsequently, when users withdrew an equivalent amount of rUSDCn, the corresponding rUSDCn was burned, and the user received the same amount in USDC. This intricate process allowed the attacker to manipulate the pool balances effectively.
The attacker initiated a deposit of 543.600,000002 USDC, resulting in the minting of 543.600,000002 rUSDCn. The subsequent immediate withdrawal amounted to 407.700,000000 USDC, leading to the burning of 15 rUSDCn.
In a repetitive loop, the attacker systematically carried out a cycle of depositing and withdrawing a substantial amount of USDC, while intentionally burning only a minimal amount of rUSDCn. This strategic manipulation allowed the attacker to exploit the rounding error present in the system, optimizing their gains during each iteration of the process. The attacker leveraged this pattern to efficiently exploit the vulnerability in the code, ultimately gaining an advantage in the overall transaction sequence.
Timeline
- Jan 02, 18:53:23: The pool initialization occurs with insufficient data.
- Jan 02, 18:53:38: The attacker executes a flash loan, manipulating the liquidity index.
- Jan 02, 18:53:46 to 18:53:49: The attacker exploits a rounding error, withdrawing from the pool.
- Jan 3, 2024, 00:14 AM UTC: The Radiant Capital team receives notification of the exploit from the attacker. They promptly pause the protocol and initiate an investigation.
https://twitter.com/RDNTCapital/status/1742338729925112272
- Jan 3, 2024, 08:05 PM UTC: The Radiant Capital team identifies the root cause of the exploit.
https://twitter.com/RDNTCapital/status/1742638364933714112
- Jan 4, 2024: The pool remains paused as the Radiant Capital team continues to address the exploit and assess necessary remedial actions.