Spectra Protocol Exploit: Arbitrary Call Strikes Again
Overview
On July 23, 2024, a malicious transaction targets the Spectra Protocol, resulting in the loss of 73K USD.
Chain: Ethereum
Attacker Address: 0x53635bf7b92b9512f6de0eb7450b26d5d1ad9a4c
Attack Contract: 0xba8ce86147ded54c0879c9a954f9754a472704aa
Victim Contract: 0x3d20601ac0ba9cae4564ddf7870825c505b69f1a
Tx: 0x491cf8b2a5753fdbf3096b42e0a16bc109b957dc112d6537b1ed306e483d0744
Summary of the Attack
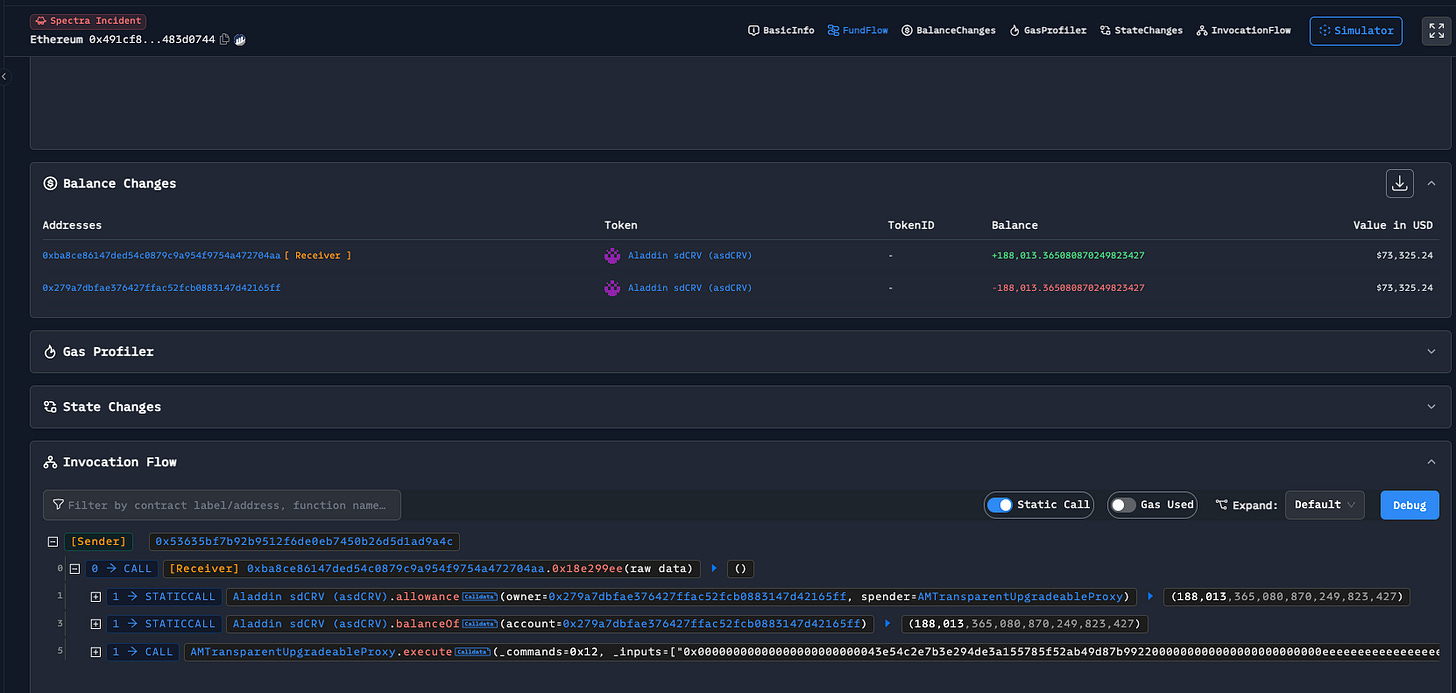
The breach was traced to an arbitrary call vulnerability in Spectra's router contract. This flaw allowed the attacker to drain tokens that had been approved for that contract. Although the attack compromised transactions from four individual wallets, the core protocol contract of Spectra remained secure, ensuring the safety of the funds within it. Spectra swiftly addressed the issue and restored normal operations.
The attacker used the `execute` function to carry out the attack. Here is a simplified version of the process:
The `execute` function called another internal function `_dispatch`.
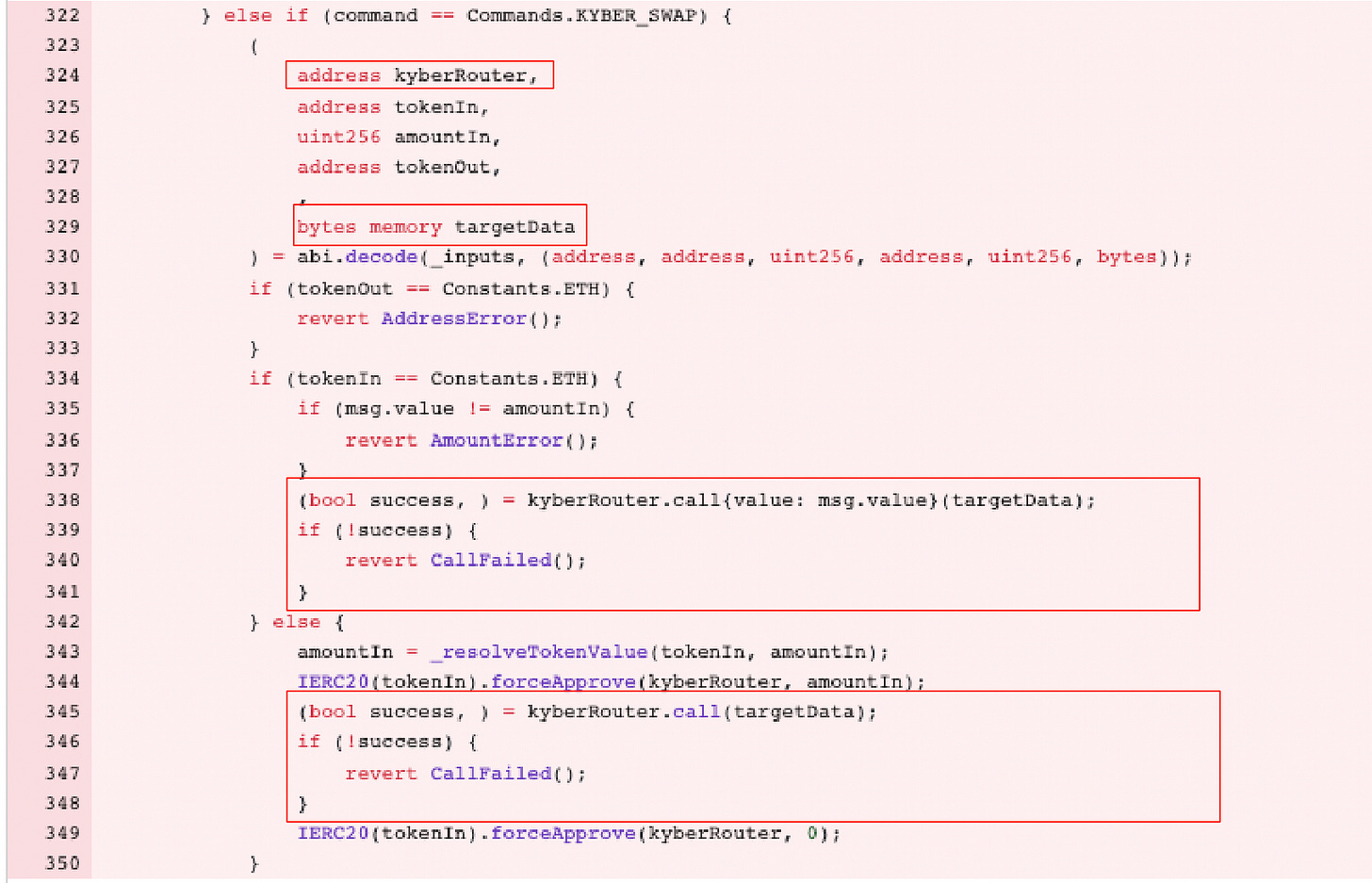
`_dispatch` determines the action based on the `_commandType`. In this case, `_commandType` was `0x12`, which corresponds to a `KYBER_SWAP`.
The attacker could control the `kyberRouter` and `targetData` variables, allowing them to manipulate the Spectra Protocol contract to call any contract with arbitrary parameters.
Conclusion
The vulnerability exploited here was due to inadequate parameter validation in the Spectra Protocol contract. The attacker crafted specific input data that allowed them to manipulate the contract into transferring tokens to an address they controlled.
This type of attack was highlighted in our training course at Bangkok HITB 2024. In this section, we cover various real-world attack types and provide strategies to secure your protocol effectively.
Recommendations
Multiple Layers of Validation: Ensure strict validation of all parameters passed to smart contract functions.
Comprehensive Audits: Engage multiple auditing firms for thorough code reviews and cross-verification before launching the protocol.
By addressing these vulnerabilities, projects can better safeguard against such attacks in the future.