Step Hero's Reentrancy in Referral System
On February 21, 2025, StepHeroNFTs was exploited, resulting in a loss of approximately $90,000. Let's examine the details of how this attack took place.
Attacker : https://bscscan.com/address/0xFb1cc1548D039f14b02cfF9aE86757Edd2CDB8A5
Vulnerable Contract : https://bscscan.com/address/0x9823E10A0bF6F64F59964bE1A7f83090bf5728aB
Attack Tx : https://bscscan.com/tx/0xef386a69ca6a147c374258a1bf40221b0b6bd9bc449a7016dbe5240644581877
Exploit analysis
Step Hero is an innovative NFT fantasy role-playing game (RPG) that operates seamlessly across both the Binance Smart Chain (BSC) and Polygon networks. This cutting-edge platform has successfully merged the exciting world of NFT gaming with Decentralized Finance (DeFi) mechanics, creating a unique ecosystem where entertainment meets financial opportunity. Players can immerse themselves in an enchanting fantasy world while simultaneously generating potential returns on their investments.
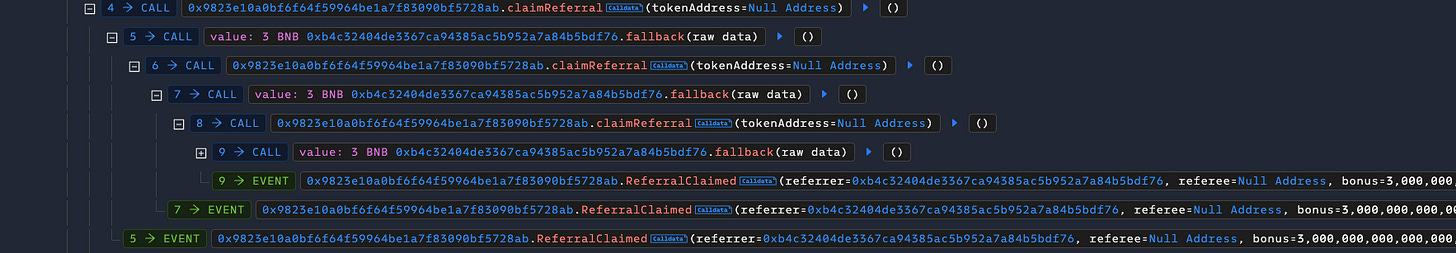
However, a critical security vulnerability was identified in Step Hero's referral fee claiming mechanism. The issue stems from the system's architecture, where the claiming function makes direct calls to a private function without implementing proper reentrancy guards. This oversight creates a significant security risk, as it enables referrers to exploit the system by repeatedly claiming fees, provided the contract maintains sufficient balance.
The vulnerability was eventually exploited through a sophisticated reentrancy attack targeting Step Hero NFTs. The attack vector involved calling the claimReferral function, which processes the referral payment. Due to the lack of proper protection, the receiving contract could recursively call the claimReferral function multiple times, effectively draining funds from the system. This incident highlights the crucial importance of implementing robust security measures, particularly reentrancy guards, in smart contract development.
Although this contract is unverified, the claimReferral function was modified through the bytecode decompilation. This function calls directly into a private function, which lead to this issue.
Conclusion
This security breach serves as a stark reminder of the importance of thorough security auditing and the implementation of standard security practices like the checks-effects-interactions pattern and reentrancy guards. The incident resulted in significant financial losses and damaged user trust, emphasizing that even innovative platforms must prioritize security fundamentals in their smart contract development.