Sumer Money hack - Reentrancy and exchange rate manipulation
The sdrETH contract of the SumerMoney project, a forked version of the CEther contract from Compound, was recently attacked. The attack vector is not new; the attacker leveraged a reentrancy vulnerability to manipulate the exchange rate between the wrapped sdrToken and the underlying token.
Overview
Attacker address:
https://basescan.org/address/0xbb344544ad328b5492397e967fe81737855e7e77
Attack transaction: https://basescan.org/tx/0x619c44af9fedb8f5feea2dcae1da94b6d7e5e0e7f4f4a99352b6c4f5e43a4661
Vulnerable contract (sdrETH token): https://basescan.org/address/0x7b5969bb51fa3b002579d7ee41a454ac691716dc
Exploit analysis
The attacker first performed a flash loan to borrow a large amount of 150 WETH and 645,000 USDC from the Balancer Vault. Then, he attempted to push these assets into the sdrETH and sdrUSDC contracts to mint the corresponding wrapped tokens.
With these assets as collateral, the attacker attempted to borrow all the available underlying assets in the sdrETH market, which amounted to approximately 150 ETH. After borrowing, the attacker immediately called the repayBorrowBehalf function, repaying the borrowed ETH plus "1 wei". Since the repayBorrowBehalf function refunds the excess amount to the payer using the low-level address.call method, it eventually triggers the reentrancy attack flow. Leveraging this vulnerability, the attacker can manipulate the exchange rate in their fallback function before the totalBorrows is updated.
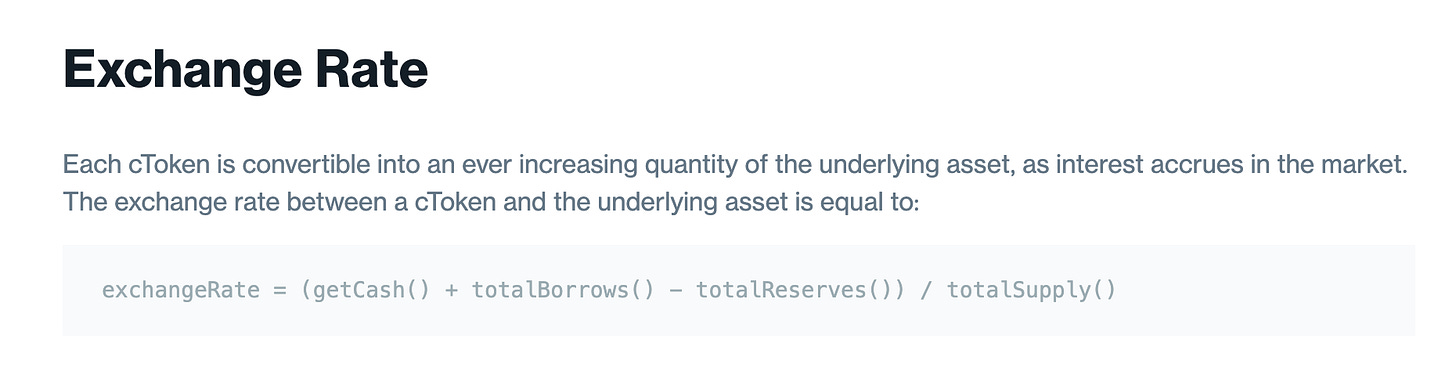
Check out the Compound documentation regarding the exchange rate, and we can see that if the totalBorrows() isn't correctly decreased after repayment, the exchange rate would be much higher than it should be.
The attacker then proceeded to borrow all the remaining assets in the sdrcbETH and sdrUSDC markets.
With the manipulated exchange rate of the sdrETH market, the attacker only needed approximately 74 sdrETH to redeem back his original amount of 150 ETH, while the sdrUSDC amount was redeemed as normal.
After repaying all the loans and completing the attack, the attacker profited approximately 10 cbETH and 310,000 USDC.
Conclusion
Web3 developers should exercise caution when customizing common protocols such as Compound, especially when introducing new features or modifying existing ones.
Although the reentrancy attack is a well-known vulnerability in smart contracts and has been exploited in many previous projects, it remains a common attack vector in the Web3 space. This attack highlights the importance of security audits and the necessity for developers to adhere to best practices in future projects.