SuperRare Exploit Analysis
SuperRare's staking contract (v1) on Ethereum was exploited, resulting in the unauthorized transfer of approximately 11.9 million RARE tokens worth approximately $680K.
SuperRare operates as a digital art marketplace and NFT platform that allows artists to create, sell, and collect rare digital artworks. The platform features its own native token (RARE) which is used for governance, staking rewards, and platform utility.
SuperRare Staking Contract
The SuperRare staking contract (v1) implements a reward distribution system using Merkle trees to efficiently distribute RARE tokens to eligible stakers. The core features include:
Merkle Root Management: Allow admins to update the root hash of reward distribution trees.
Token Claims: Users can claim their allocated RARE tokens by providing valid Merkle proofs.
Access Control: Privileged accounts should have exclusive rights to update critical parameters.
Key Information
Exploiter Address: https://etherscan.io/address/0x5B9B4B4DaFbCfCEEa7aFbA56958fcBB37d82D4a2
Attack Transaction: https://etherscan.io/tx/0xd813751bfb98a51912b8394b5856ae4515be6a9c6e5583e06b41d9255ba6e3c1
Exploit Analysis
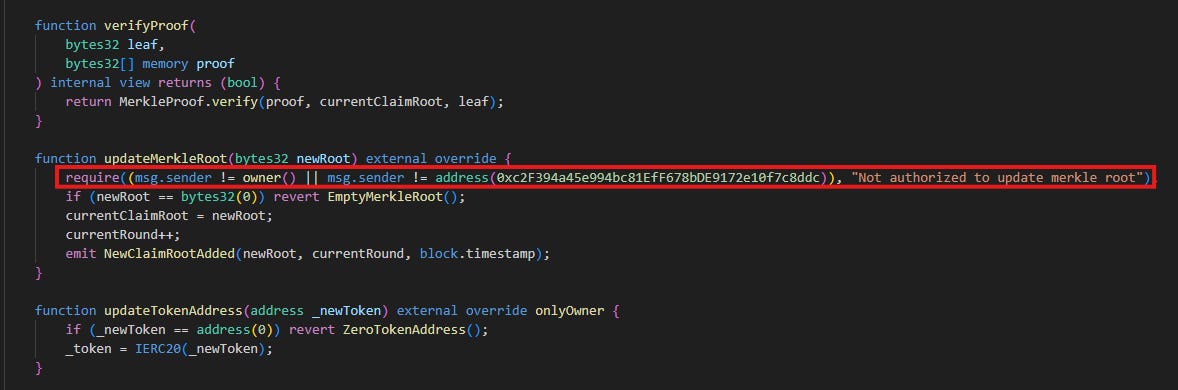
The vulnerability in SuperRare's staking contract stemmed from a critical flaw in the updateMerkleRoot function. This function was designed to allow only privileged accounts (such as the contract owner or authorized administrators) to update the Merkle root used for reward distribution validation.
The Vulnerability: Inverted Access Control
The root cause of the exploit was traced to incorrectly inverted validation checks in the updateMerkleRoot function. Instead of implementing proper access control to allow privileged accounts to update the Merkle root, the contract logic did exactly the opposite.
This meant that while the intended authorized accounts were locked out of updating the Merkle root, any external attacker could freely manipulate this critical parameter.
Attack Execution
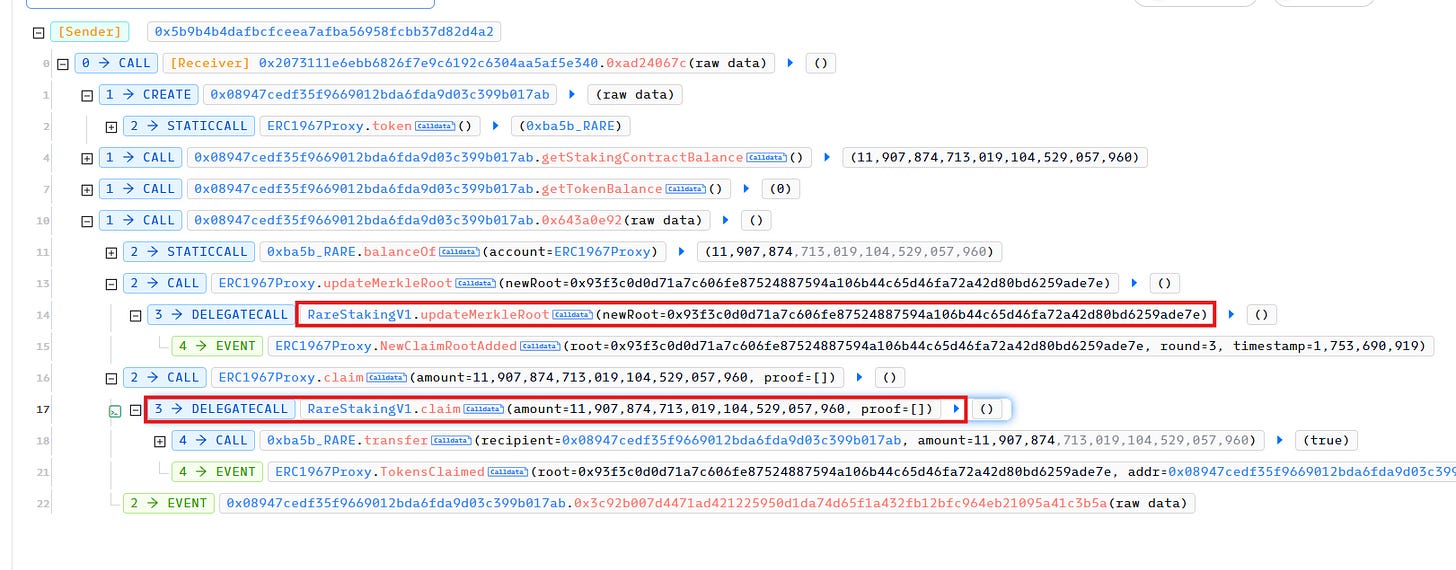
The attack transaction shows the following sequence:
Merkle Root Manipulation: The attacker called the vulnerable
updateMerkleRootfunction to set a malicious Merkle root that would validate their crafted claim proof.Fraudulent Claim: With the malicious Merkle root in place, the attacker submitted a claim transaction with fabricated proof data that appeared valid under the new root.
Token Extraction: The contract validated the attacker's fraudulent proof against the malicious Merkle root and released 11,907,874.71 RARE tokens to the attacker's address.
Technical Impact
The transaction logs reveal several key events:
NewClaimRootAdded: Shows the attacker successfully updated the Merkle rootTokensClaimed: Confirms the large unauthorized token claimTransfer: Documents the movement of RARE tokens from the staking contract to the attacker
The exploit was particularly damaging because:
The attacker could claim the maximum available token balance in the contract
No time delays or additional validation steps prevented the immediate token withdrawal
The inverted access control made the attack trivial to execute once discovered
Conclusion
The SuperRare exploit demonstrates how a single logic error in access control can lead to catastrophic losses in DeFi protocols. The vulnerability highlights several critical security principles:
Access Control Validation: Proper testing of permission systems is essential. Inverted logic in access controls can completely undermine security assumptions.
Principle of Least Privilege: Critical functions like Merkle root updates should have multiple layers of protection, including time delays, multi-signature requirements, or governance processes.
Comprehensive Testing: Edge cases in access control logic must be thoroughly tested, including scenarios where different account types attempt restricted operations.
Audit Focus Areas: Security audits should pay special attention to authentication and authorization logic, as these represent single points of failure.
The $680K loss could have been prevented through proper implementation of access controls, comprehensive testing of permission logic, and additional safeguards such as withdrawal limits or time delays for critical parameter updates. This incident serves as a reminder that even simple logic errors can have devastating financial consequences in the DeFi ecosystem.