Technical Analysis - Improper Use of Private iOS APIs in some Vietnamese Banking Apps
Technical analysis reveals that BIDV and Agribank mobile banking apps exploit private iOS API side channel issue to detect other apps installed on users’ iPhone/iPad devices.
Bài viết tiếng Việt có thể xem tại đây
Introduction
Yesterday, reports emerged in the Vietnamese infosec community that two popular banking apps – BIDV SmartBanking and Agribank – were using hidden / private iOS API to detect other apps installed on users’ iPhones.
This behavior was initially highlighted by @opa334, developer of TrollStore, on infosec.exchange two days ago and later in a Facebook post on Vietnamse J2TEAM forum. The controversy quickly gained traction because such behavior suggests a violation of Apple’s policies and an invasion of user privacy.
The initial information in the Facebook post mentioned suspicions regarding our BShield Mobile Security solution, leading to a misunderstanding that inaccurately affected the reputation of BShield and Verichains.
Therefore, we conducted a thorough technical analysis of the mentioned bank apps BIDV SmartBanking (v5.2.62, updated on Mar 14, 2025) and Agribank Plus (v5.1.8, updated on Mar 25, 2025), detailed in this write-up, which also examines implications for users and the banking apps.
Disclaimer:
This analysis was released strictly for security research, transparency, and customer protection purposes. This document also aims to clarify false claims regarding BShield's involvement, promote technical transparency.
While we strive for accuracy, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the information, products, services, or related graphics contained in this blog for any purpose. The information provided in this article is not intended to encourage, guide, or support any actions that violate the policies of Apple, Google, or current legal regulations. We shall not be held liable for any damages or consequences arising from the misuse of the information presented in this analysis.Technical Analysis
TLDR;
The apps (BIDV SmartBanking and Agribank Plus) were reported of using the private iOS API SBSLaunchApplicationWithIdentifierAndURLAndLaunchOptions to detect TrollStore and other applications installed on users’ devices.
Technical analysis reveals that BIDV SmartBanking (v5.2.62, updated on Mar 14, 2025) and Agribank Plus (v5.1.8, updated on Mar 25, 2025), developed by VNPay. For app protection on Android and iOS, VNPay uses commercial solutions including Mobile App Shield DexProtector/Licel and Dexguard/iXGuard, together with a self-developed code likely named “VNPay Runtime Protection” or “VNPShield”.
VNPay Runtime Protection employs a mechanism exploiting side-channel issue of iOS private API SBSLaunchApplicationWithIdentifierAndURLAndLaunchOptions to detect app presence on user iOS devices, combining with a very weak XOR encryption trying to hide the private API strings from scanning. This side-channel issue works on latest iOS versions on non-jailbroken device. According to Apple Security Bounty Program, this issue likely falls under the category "Device attack via user-installed app – Unauthorized access to sensitive data", qualifying for a $5,000 bug bounty.
Exploiting private APIs to enumerate installed apps violates Apple App Store policies and pose a significant risk of App removal by Apple, potentially impacting millions of bank customers.
This policy violation has NO relation to BShield of Verichains. The primary purpose of application shielding is to proactively protect banking applications against malicious apps on user devices, preventing account takeover, theft of money and personal data. From time to time, we are aware of various new detection methods, including certain tricks utilizing N-day exploits or private APIs. However, as an bank-grade Mobile App Protection solution protecting more than 100 millions users, BShield strictly uses only stable and legitimate detection techniques. We do NOT use risky or dangerous methods, ensuring full compliance with store policies, prioritizing user and business security amid rising threats targeting banking apps.
Mechanism of Obfuscation
To hide their use of the private API, the apps employ a very weak XOR encryption to obfuscate sensitive strings, such as API names and application bundle identifiers. This technique likely aims to conceal API strings from static analysis tools, making it harder to detect the misuse of APIs. At runtime, the encrypted strings are decrypted by XORing them with the key to reveal their original values.
The key is “94826663" on BIDV app (“41818020” on Agribank app) and encrypted data is stored in the data section. The decryption function, named RE_Decrypt_10233F108, can be represented in Python as:
From the decrypted strings, we noted that this code likely a part of a module named VNPay Runtime Protection. Returning to the original code, we observed string usage patterns as below:
The code block works as below:
Creating metadata for constants stored in the data section.
Call swift_initStaticObject to initialize the static object and the value stored at another location in the data section (in this case, the result will be a Swift String object).
Calling RE_Decrypt_10233F108 to decrypt strings to process.
This could be simplified as v40 = dlopen(XOR_DECRYPT(X), 1), where X is the encrypted string in the data section.
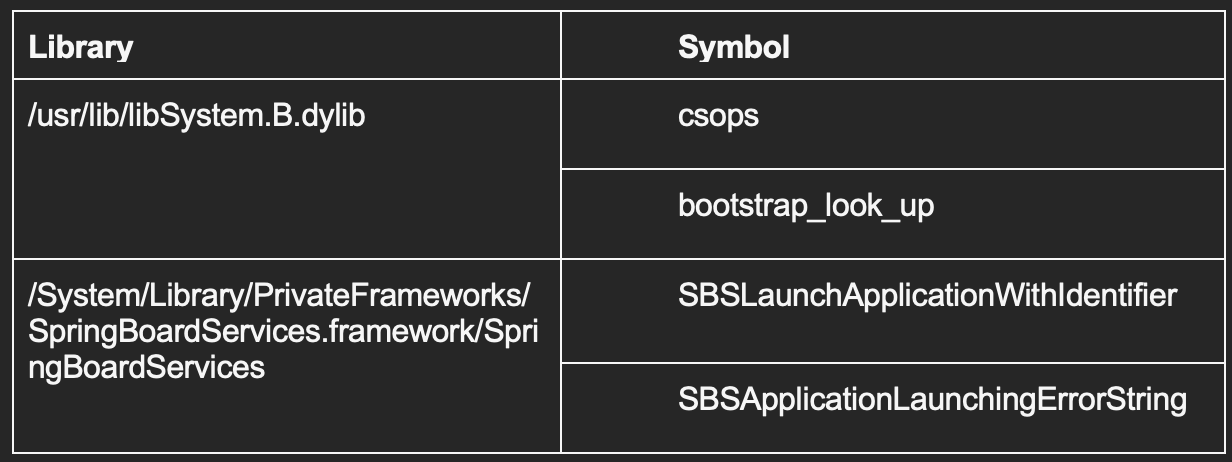
The above code snippet equivalent to invoke the csops function from /usr/lib/libSystem.B.dylib
"/usr/lib/libSystem.B.dylib".csops(a1, a2, a3, a4);Similarly, the code using the same method to invoke other private APIs, for examples:
Private API to detect Apps installed on users’ iOS devices
The code check for installed application by calling private iOS API SBSLaunchApplicationWithIdentifier with the bundle ID of the app. Typically, developers launch apps through schemes if supported. However, this API directly launches any app if the calling app has Apple-issued entitlement. Hence, this private API could be used as a side channel to verify app existence through returned error codes.
Note that this API from SpringBoard is a private API and not officially provided by Apple for developers so using it violates Apple Store policy.
List of some targeted apps checks:
org.coolstar.SileoStore
com.opa334.Dopamine.roothide
com.roothide.manager
com.cokepokes.AppStorePlus
xyz.willy.Zebra
com.opa334.Dopamine
com.kahsooa.piqwkk.dummy
LLDB screenshot below at breakpoint in SBSLaunchApplicationWithIdentifierAndURLAndLaunchOptions showing the check for ”com.opa334.Dopamine.roothide”.

The private API is used as a side channel to verify app existence through returned error codes:
If installed: returns security policy error (error number 9) due to lack of Apple entitlement).
If not installed: returns application not found (error number 7) .
This demonstrates a side-channel exploit via private iOS verifying if an app is installed, executed in class call VNPShieldBridgingManager. We confirmed that SBSLaunchApplicationWithIdentifier private API could be used as a side channel to verify app existence through returned error codes, works on latest iOS versions on non-jailbroken devices.
When running the banking application that exploit this private API to detect software installed on a user's device, the app's console log will show error messages indicating attempts to launch applications without permissions.
Apple Store Policy Violation
According to Apple’s App Store Review Guidelines (Sections 2.5.1 and Legal 5), using non-public (private) APIs or hidden system calls without explicit user consent breaches data transparency, user control, and security standards, undermining user trust.
Specifically, Guideline 2.5.1 mandates that apps "may only use public APIs" and must utilize these APIs strictly for their intended purposes. Any use of internal, undisclosed system frameworks or functions will result in app rejection or removal. Apple enforces these guidelines to maintain app stability, protect user privacy, and uphold platform security.
Beyond just compliance, abusing private APIs can be a security and privacy issue. Apple’s rules exist partly to prevent apps from accessing data or capabilities users didn’t consent to. For example, using hidden system calls to probe a device’s state can violate user privacy and platform security. Scanning a user’s device for other installed apps without permission is explicitly disallowed and undermines user trust.
Attempting to bypass iOS sandbox restrictions or gather unauthorized data (e.g., installed app lists) is a major violation, raising serious red flags for Apple and security-conscious users. Such practices risk app bans or removal from the App Store, potentially impacting millions of bank customers.
In this analysis, we confirm that SBSLaunchApplicationWithIdentifier private API could be used as a side channel to verify app existence through returned error codes, works on latest iOS versions on non-jailbroken devices. From Apple Security Bounty Program, this shall likely fall into “Device attack via user-installed app - Unauthorized access to sensitive data” for the $5,000 bug bounty.
Conclusion
Technical analysis reveals that BIDV SmartBanking (v5.2.62, updated on Mar 14, 2025) and Agribank Plus (v5.1.8, updated on Mar 25, 2025), developed by VNPay. For app protection on Android and iOS, VNPay uses commercial solutions including Mobile App Shield DexProtector/Licel and Dexguard/iXGuard, together with a self-developed code likely named “VNPay Runtime Protection” or “VNPShield”.
VNPay Runtime Protection employs a mechanism exploiting side-channel issue of iOS private API SBSLaunchApplicationWithIdentifierAndURLAndLaunchOptions to detect app presence on user iOS devices, combining with a very weak XOR encryption trying to hide the private API strings from scanning. This side-channel issue works on latest iOS versions on non-jailbroken device. According to Apple Security Bounty Program, this issue likely falls under the category "Device attack via user-installed app – Unauthorized access to sensitive data", qualifying for a $5,000 bug bounty.
Exploiting private APIs to enumerate installed apps violates Apple App Store policies and pose a significant risk of App removal by Apple, potentially impacting millions of bank customers.
This policy violation has NO relation to BShield of Verichains. The primary purpose of application shielding is to proactively protect banking applications against malicious apps on user devices, preventing account takeover, theft of money and personal data. From time to time, we are aware of various new detection methods, including certain tricks utilizing N-day exploits or private APIs. However, as an bank-grade Mobile App Protection solution protecting more than 100 millions users, BShield strictly uses only stable and legitimate detection techniques. We do NOT use risky or dangerous methods, ensuring full compliance with store policies, prioritizing user and business security amid rising threats targeting banking apps.















Hello Verichains! Could you check Raiffeisen Bank Romania please? They seem to also detect TrollStore then auto close the app on launch, spawning a browser to their website "jailbreak" warning. no bank account needed. https://apps.apple.com/us/app/raiffeisen-smart-mobile/id1255136212 Store link. This would be also a EU GDPR issue? (scanning user private data?)