The $PORT3 Exploit: How a Missing ecrecover Zero-Check Cost Millions
Port3 Network (PORT3) Security Incident Analysis
Overview
The Port3 Network ($PORT3) has crashed from $0.03720 to ~$0.00644—an 83% drop that decimated liquidity due to a critical oversight in their signature verification logic. A hacker exploited a classic Solidity vulnerability to mint unauthorized tokens. Below are the confirmed on-chain details:
Targeted Protocol: Port3 Network
Vulnerable Contract:
0xb4357054c3da8d46ed642383f03139ac7f090343Attacker’s Wallet:
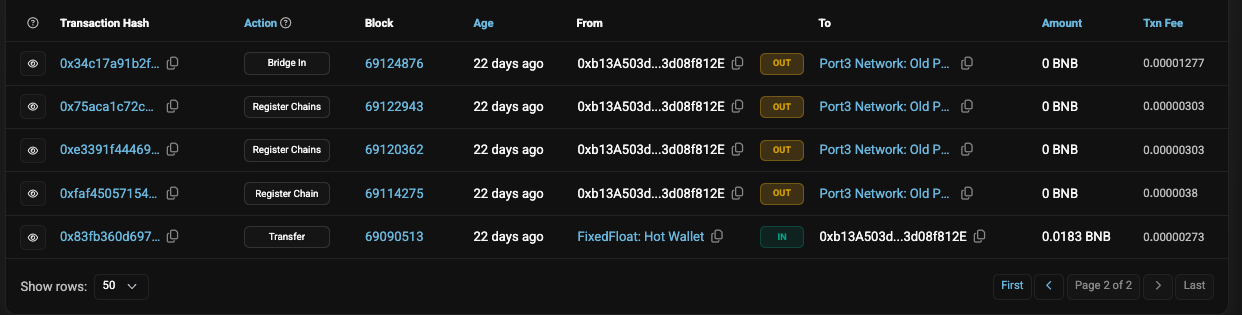
0xb13a503da5f368e48577c87b5d5aec73d08f812eAttacker’s profit: Minted 1 billion $PORT3 token worths $13.07 million. Swapped 156M PORT3 for roughly 144.53 BNB ($119.48K).
Technical Deep Dive
Looking at the initiated transactions by the attacker,
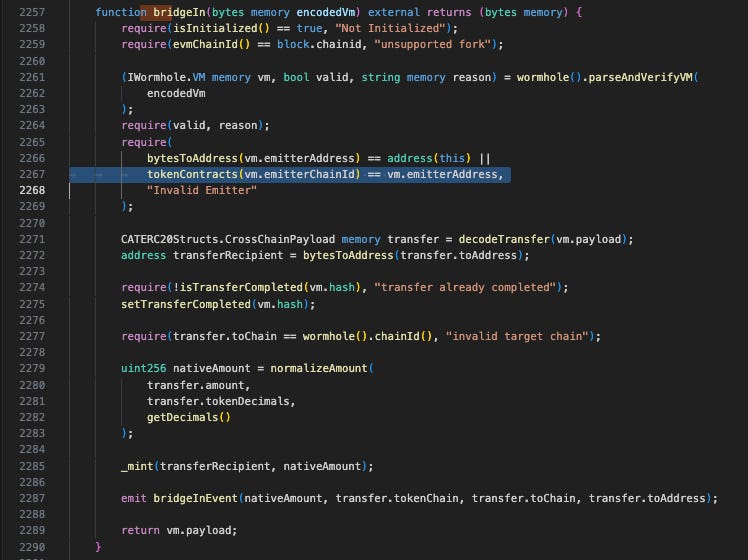
The attacker calls first registerChain and registerChains. After that, call bridgeIn again. The free mint of PORT3 token was completed by utilizing bridgeIn.
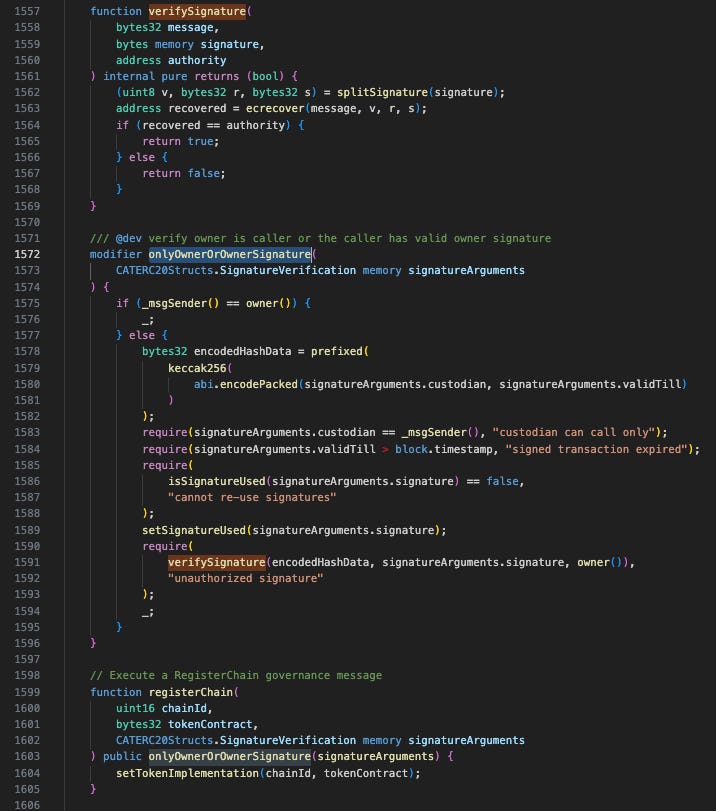
Let’s take a look at how the registerChains function is implemented in the contract of the PORT3 token’s contract:
The verifySignature Flaw The core vulnerability lies inside the signature verification logic. Here is the step-by-step failure:
The Port3 team had unset/renounced
owner‘s address. This means theowner()function returns default the zero address (0x0000...0000).The attacker calls
registerChainwith an invalid (fake) signature.Inside
verifySignature, the code callsecrecover. In Solidity, ifecrecoverfails to verify a signature, it does not revert; instead, it returnsaddress(0).The code then checks
if (recovered == authority).recoveredis0x0(due to the invalid signature).authorityis0x0(due to renounced ownership).Result:
0x0 == 0x0evaluates toTRUE.
Because the code failed to explicitly check that recovered != address(0), the contract accepted the fake signature as valid ownership proof. Therefore, anyone can pass this verification, and the attacker can add the token address to _state.tokenImplementations via registerChains, and then bypass detection in bridgeIn to complete _mint operation.
Conclusion
This incident is a textbook example of why developer assumptions are dangerous. The developers assumed ecrecover would only return a valid address or fail. They forgot the edge case: it returns 0 on failure.
Even if you think the owner will never be 0x0, write your code to handle that possibility. Code lives longer than current operational plans.
Auditors must look for functions that return “default values” (like 0, false, or 0x0) instead of reverting, and ensure those default values cannot be exploited.
$PORT3 didn’t die because of a sophisticated cryptographic break. It died because of a missing zero-check. In Web3, a single missing line of code is the difference between security and a $13 million loss.
Stay safe!


Brilliant postmortem on this exploit. The ecreover zero-address edge case is one of those Solidity gotchas that keeps biting projects because devs assume functions fail loudly instead of returning defaults. What makes this especially brutal is that renouncing ownerhsip to address(0) seemed like good practice for decentralization, but it turned the zero-check omission into a critical vulnerability instead of just sloppy code.