TokenHolder Hack Analysis
On October 7, 2025, the TokenHolder project fell victim to an attack that resulted in the loss of 20 WBNB - approximately $25,000. What makes this incident particularly striking is that the underlying vulnerability was so extremely simple that it’s hard to believe it ever made its way into production code. In this post, we’ll break down how the exploit occurred, why such a basic flaw went unnoticed, and what developers can learn from this surprising oversight.
Overview
Attacker address: 0x3feE6d8aaea76D06CF1ebEaF6B186af215F14088
Attacker’s contract: 0xe82Fc275B0e3573115eaDCa465f85c4F96A6c631
Vulnerable contract: 0x8c7f34436C0037742AeCf047e06fD4B27Ad01117
Attack transaction: 0xc291d70f281dbb6976820fbc4dbb3cfcf56be7bf360f2e823f339af4161f64c6
Analysis
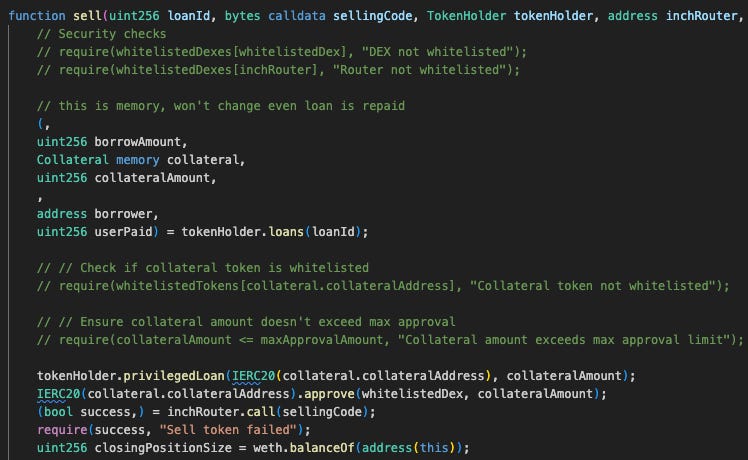
Here is the source code of the vulnerable contract (BorrowerOperationsV6):
You can quickly see that many of the require statements had been disabled. These checks are meant to validate the arguments passed into the function, ensuring that only proper inputs are processed. But, as you can tell, every one of them had been turned off - leaving the contract wide open to be attacked.
From there, the hacker’s remaining work was surprisingly simple. He created a contract that implemented just enough functions to masquerade as a valid TokenHolder and DEX, then invoked BorrowerOperationsV6.sell() to sell a fake loans - values returned directly from his contract. With all validation checks removed, the exploit executed flawlessly, allowing him to walk away with 20 WBNB ( 19.2 BNB after fees).
Summary
This incident highlights how even a small oversight can have serious consequences. Whether due to developer negligence or accidentally deploying test code in production, the result was a real financial loss. While the 20 BNB lost here is relatively small compared to the potential impact of such mistakes, it serves as a stark reminder that no error is too minor to ignore. Careful auditing and thorough testing before deployment are essential - continuing to review your code rigorously can prevent simple mistakes from turning into costly exploits.


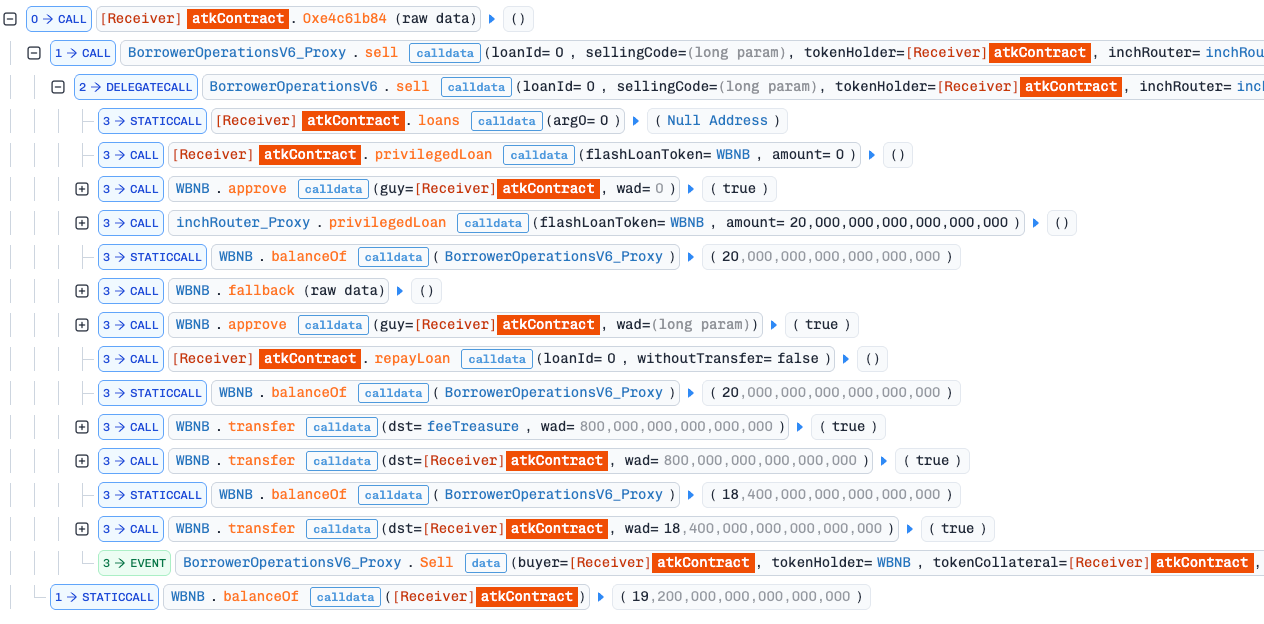
would like to know which software or website you use to trace the tx like in the article