UwU hacked cause by price oracle manipulated
UwU Lend provides a contract allows other contracts to obtain asset prices in order to calculate the value of these assets for borrowing purposes. However, flashloan can manipulates it
Summary
UwU Lend provides a contract called
FallbackOracleallows other contracts to obtain asset prices in order to calculate the value of these assets for borrowing purposes.However, flashloan manipulates the getPrice function.
An attacker borrowed tokens and flashloaned assets from the Curve Finance Pool to manipulate the price CRV.
He takes a profit and returns the loan.
Contract vulnerable: 0x9bc6333081266e55d88942e277fc809b485698b9
Tx Attacks:
0xca1bbf3b320662c89232006f1ec6624b56242850f07e0f1dadbe4f69ba0d6ac3
0xb3f067618ce54bc26a960b660cfc28f9ea0315e2e9a1a855ede1508eb4017376
0x242a0fb4fde9de0dc2fd42e8db743cbc197ffa2bf6a036ba0bba303df296408b
Timeline
Jun-13-2024 07:46:23 AM +UTC: Contract is attacked again. 0x9235….6110
Jun-10-2024 12:12:35 PM +UTC, the contract is hacked
Apr-16-2024 09:27:59 PM +UTC, an owner of the contract updated a new Oracle address for crvUSD is
0xd252953818bDf8507643c237877020398FA4B2E8(sUSDePriceProviderBUniCatch)
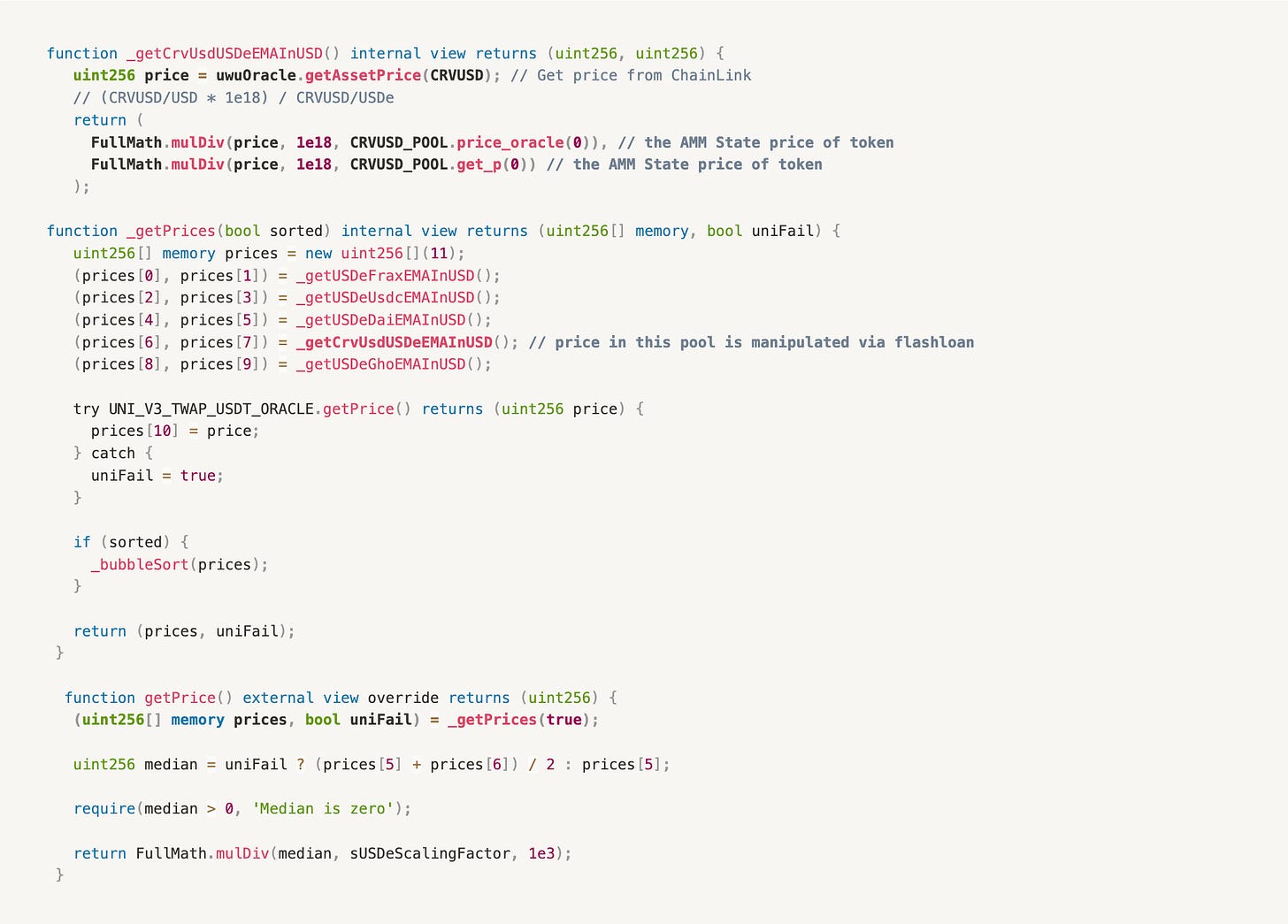
Incident Analysis
The root cause is in 0xd252....B2E8 (sUSDePriceProviderBUniCatch). The price of assets is derived from some different oracles, like Chainlink and the asset pool. After that, the price is calculated by their average.
Following comments in the code, the flows call in order: getPrice() ⇒ _getPrices(…) ⇒ _getCrvUsdUSDeEMAInUSD()
The root cause because the contract uses multiple Oracles including price in the CRVUSD pool and ChainLink. After that, the final price is calculated on that
Hence, the CRVUSD pool can be manipulated by flash loan attack
Details of attack methodology
An attack using flashloan to manipulate the price in pools. He loaned multiple pools to get large WETH and WBTC
He deposits those tokens to borrow sUSDe at a low price into the LendingPool contract
Current price of sUSDe
After that, he exchanges all assets to increase the price of sUSDe and liquidate his borrowing positions.
Finally, he deposited manipulated sUSDe to borrow more base tokens for profit
Conclusion
The attack exploited a vulnerability in the price oracle, where the attacker used real-time spot prices and median price calculations to manipulate the sUSDE price.
The team resolved the issue by replacing the new Oracle contract. However, the attacker hacked again. Following the next blog to delve into their incomplete patch.