Verichains Weekly Security Digest | July 2023 Week 4
In this week’s digest, the DeFi market lost a total of $760,000 in a series of attacks. Most notably 4 different projects were hacked using the same set of codes, losing $230,000 in total.
Last Week’s Incidents
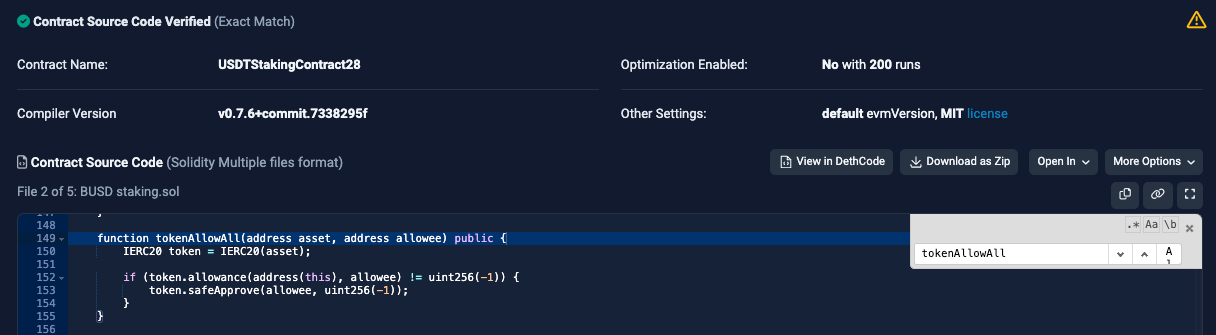
🚨Project: USDTStakingContract28
⛓️Chain: Ethereum
💥Type: Access Control
💸Loss amount: $21,000
Last week, a contract named “USDTStakingContract28” was exploited for $21,000. It was found to lack sufficient restrictions on the "tokenAllowAll" function, which allows users to grant approval for transfers to any entity they control. This particular vulnerability poses a significant risk to the security and integrity of the contract. To mitigate potential exploits and ensure the system's safety, it is crucial to conduct a comprehensive security audit to identify and address any weaknesses or loopholes within the contract's codebase.
🚨Project: $BNO
⛓️Chain: BSC
💥Type: Miscalculation
💸Loss amount: $500,000
A token called $BNO was hacked for over half a million dollars due to a flaw in the reward calculation mechanism. The "emergencyWithdraw" function, designed for instant ERC20 token withdrawal, failed to account for NFT stake records. By exploiting this vulnerability, the attacker deposited both NFTs and ERC20 tokens and executed the "emergencyWithdraw" exclusively for the ERC20 tokens. This allowed the attacker to bypass the reward calculation check, enabling them to claim undeserved rewards and causing significant financial loss to the pool and its users.
🚨Project: APE DAO
⛓️Chain: BSC
💥Type: Price Manipulation
💸Loss amount: $7,000
A token called $APEDAO was hacked for $7,000 due to a price manipulation attack. The attacker manipulated the price of the $APEDAO token in the pair contract by conducting repeated token transfers, exploiting the "skim" function to withdraw excess tokens, and burning a substantial number of $APEDAO tokens held in the contract.
🚨Project: FIRE FIST, AI-Doge, QX, Utopia
⛓️Chain: BSC
💥Type: Bad Randomness
💸Loss amount: $230,000
In a series of attacks, 4 consecutive projects were hacked using the same method with an accumulated loss of $230,000. In these projects, their smart contract contains an "_airdrop" function within the "transfer()" method to distribute tokens randomly to addresses. However, the method's lack of true randomness poses a significant vulnerability. The issue arises from the use of manipulable inputs like the last airdrop address, block numbers, and "from" and "to" addresses for generating random addresses. This predictability enables malicious actors to influence the airdrop outcome, leading to exploitation.