Verichains Weekly Security Digest | August 2023 Week 2
In this week’s security digest, the DeFi market lost over $62,000,000. Of particular significance was the Curve Finance reentrancy attack, which garnered significant attention as it resulted in a loss exceeding $59 million, outpacing the losses experienced by CoinsPaid in the preceding week.
Last Week’s Incidents
🚨Project: Curve Finance
⛓️Chain: Ethereum, BSC
💥Type: Reentrancy Attack
💸Loss amount: $59,000,000
Last week, the DeFi market was shaken by a $59,000,000 reentrancy attack on Curve Finance. Right after the attack had taken place, Verichains security researchers swiftly published a comprehensive write-up, analyzing the root causes of the attack. A vulnerability in the Vyper compiler used for Curve Pools, enabled a reentrancy attack despite the nonreentrant decorator protection. This was due to a missing check between Vyper versions 0.2.15 and 0.3.0, allowing separate reentrancy lock slots for functions and failing to prevent attacks.
Read the full write-up here: https://blog.verichains.io/p/curve-pools-hack-59-million-lost
🚨Project: Metronome DAO
⛓️Chain: Ethereum
💥Type: Price Manipulation
💸Loss amount: $1,600,000
In the second largest attack last week, Metronome DAO was attacked for $1,600,000 via read-only reentrancy in Vyper programming language version 0.2.15. By repeatedly calling the "add_liquidity" function before making withdrawals, the hacker managed to exploit the imbalance in the liquidation of a pair, thereby profiting from the vulnerability. This could have enabled the hacker to manipulate the system to their advantage due to the flaw in the affected version of Vyper.
At the time of writing, the project had recovered a significant portion of the exploited funds with plans to recover more.
🚨Project: Unverified
⛓️Chain: Arbitrum
💥Type: Price Manipulation
💸Loss amount: ~$845,000
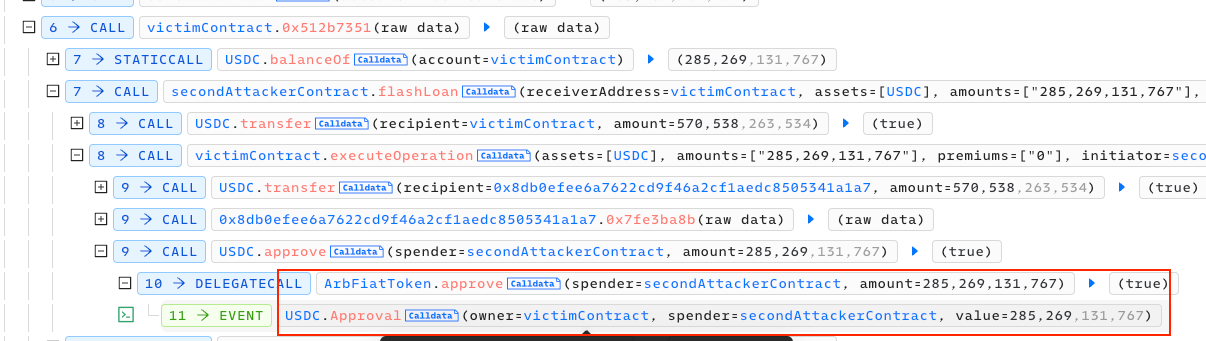
An unverified contract was attacked for $845,000 due to an insufficient configuration of its flash loan mechanism, enabling the attacker to withdraw tokens after the flash loan is repaid. The contract that calls this function fails to adequately validate user inputs. This vulnerability provides an opportunity for a potential attacker to craft a deceptive flash loan contract and initiate the approval process, thereby exploiting the system.
🚨Project: Leet Swap
⛓️Chain: Base
💥Type: Price Manipulation
💸Loss amount: $620,000
LeetSwap, a DeFi project on Coinbase L2, Base was attacked for $620,000 due to the LeetSwapPairV2 contract on the Base chain contained a critical vulnerability within its public function called "_transferFeesSupportingTaxTokens()". This vulnerability enabled anyone to initiate the function, resulting in the transfer of all token balances within the contract to a designated Fee Wallet. This action led to a disruption in the liquidity balance within the contract. Seizing the opportunity, the attacker took advantage of this imbalance by swapping small tokens, which resulted in substantial profits due to the compromised liquidity structure.
In the most recent project update, they have successfully secured a 10% white hat fee as compensation for the secure retrieval of their funds.
🚨Project: Uwerx
⛓️Chain: Ethereum
💥Type: Price Manipulation
💸Loss amount: $324,000
$324,000 was stolen from the Uwerx DEX. In this situation, when users sell a particular token, the WERX contract applies a 2% fee on the transfer and burns 1%. However, due to an issue where the uniswapPoolAddress is set to 0x01, the burn process fails. Exploiting this flaw, a hacker executes the "skim()" function, enabling them to transfer the token to 0x00, a dead address, consequently causing an imbalance in the Uniswap pool's liquidity.
Taking advantage of the vulnerability, the hacker executes a series of steps: First, they initiate a flash loan of 20,000 ETH and exchange it for 5 million WERX. Subsequently, the hacker transfers $4.4 million worth of WERX to the Uniswap pool before performing the skim operation. Following this, the hacker swaps the remaining 623k WERX tokens to the dead address 0x00. As a result of these actions, the hacker manages to generate a profit of 174 ETH from this exploit.