Verichains Weekly Security Digest | June 2023 Week 3
In this week’s digest, Verichains join forces with AvengerDAO to educate users on safety and security when traversing Web3.
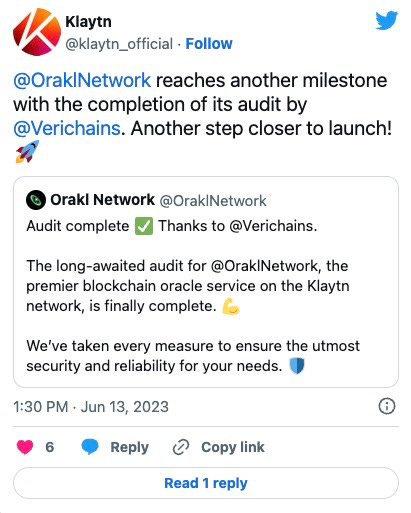
Verichains had also completed a smart contract audit for Orakl Network an oracle on the Klaytn Blockchain.
The DeFi market hemorrhaged more than $21 million last week.
Events And Partnerships
Verichains x AvengerDAO
Last year, on September 20th, Verichains joined forces with AvengerDAO, a flagship security initiative by BNB Chain. This collaboration aimed to ensure user safety by bringing together distinguished security vendors from all across Web3.
Together, we developed one of three essential components that form the backbone of the AvengerDAO system, the Meter. Also known as the Risk Scanner, it is a free-to-use tool that enables investors to safely explore the BNB Chain’s ecosystem by providing the ability to scan and assess contracts and addresses. By performing a scan, investors will receive a score on the Risk Band based on a variety of security assessments to help them understand the risk associated with the contract or wallet they are interacting with.
In addition to our contribution to the Risk Scanner, Verichains has also made a dedicated commitment to AvengerDAO by extending our security services to projects on the BNB Chain. This aligns with our mission to enhance transparency and improve security within Web3.
Earlier this week, AvengerDAO hosted its Bootcamp event, an event aimed at emphasizing the significance of security awareness and a great learning experience for anyone interested in consolidated information focused on safety and security when traversing Web3.
We encourage readers to join the event and check out our featured article highlighting the creation and ease of use of the "AvengerDAO Risk Scanner - Navigating Web3 with Enhanced Safety." Afterward, test your knowledge in our quiz for a chance to win up to $100 USDT.
For more information, click here: https://dappbay.bnbchain.org/campaign/avengerdao-10k-usdt
Orakl Network Security Audit
We are happy to announce the completion of Orakl Network’s smart contract audit, an oracle on the Klaytn Blockchain. Throughout the auditing process, we appreciate the close collaboration with the Orakl Network team and their swift response in addressing found vulnerabilities. We wish Orakl Network all the best with their upcoming launch.
Read Orakl Network’s public audit report here: https://github.com/verichains/public-audit-reports/blob/main/Verichains Public Audit Report - Orakl Smartcontracts - v1.3.pdf
Last Week’s Incidents
🚨Project: $UN
⛓️Chain: BSC
💥Type: Skim LP Vulnerability
💸Loss amount: $26,000
A token called $UN was exploited for $26,000 by a front-running bot. The bot exploited the system by repetitively transferring funds to a pair address and utilizing a technique called skimming to acquire extra tokens. Their objective was to trigger the execution of the sendreward() function, which likely initiated a reward distribution process. By redirecting the acquired tokens to their attack contract, the bot aimed to gain unauthorized access to funds or disrupt the system's intended functionality.
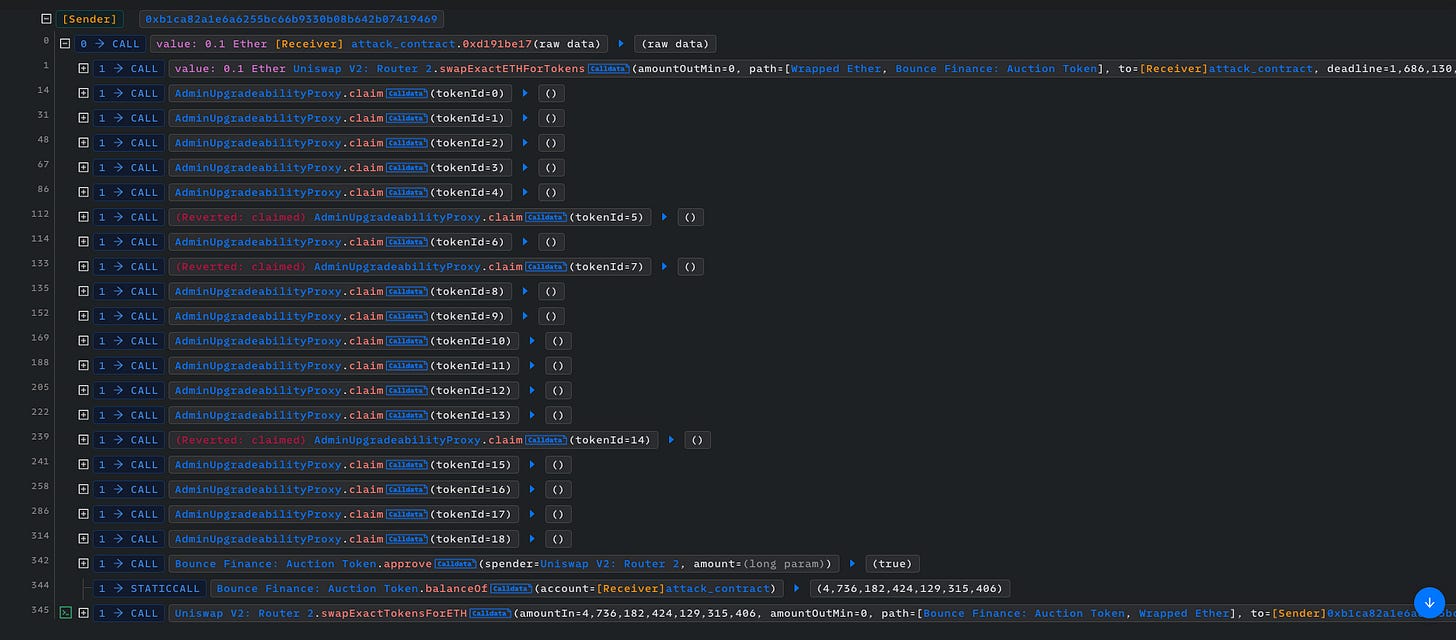
🚨Project: Bounce Finance
⛓️Chain: ETH
💥Type: Price Manipulation
💸Loss amount: $9,000
A DeFi auction platform called Bounce Finance was exploited for $9,000 last week. The attacker started by borrowing 0.1 ETH and exchanging it for Auction tokens. Subsequently, they took advantage of the claim() function within the Auction Finance contract. This function involved swapping ETH for Auction tokens, which led to an imbalance in the Auction pair.
Exploiting this opportunity, the attacker then executed a swap using the Auction tokens to receive a significant return of 4.7 ETH, surpassing their initial borrowed amount by more than 4 ETH. By leveraging the price discrepancy caused by the imbalance, the attacker successfully profited from the transaction.
Bounce Finance had yet to address the incident.
🚨Project: Atomic Wallet
⛓️Chain: N/A
💥Type: Supply Chain Attack
💸Loss amount: $21 Million (and counting)
In the largest hack last week, Atomic Wallet users lost $21,700,000 (and still counting). The attack likely utilized multiple vectors, including a software supply chain attack where a vulnerable or backdoor SDK was introduced during the wallet's development process, the exposure of encryption algorithm information allowing the brute-forcing of private keys, and the absence of dynamic protection in the Android app client, enabling the insertion of malicious software on users' devices.
At the time of writing, the firm had begun the remediation process and is engaging with Chain Analysis to trace the stolen funds.







Avenger Dao! Strong.