Verichains Weekly Security Digest | July 2023 Week 1
In this week’s digest, Verichains’ Co-founder Thanh Nguyen will be speaking at GM Vietnam, sharing our insight into MPC security research.
In last week’s incident, the DeFi market witnessed a multi-million dollar hack on PolyNetwork, losing upwards of $10,000,000.
Events And Partnerships
Verichains x GM Vietnam
Leading up the GM Vietnam, Vietnam’s premier blockchain event, Verichains is collaborating closely with Kyros Venture to educate the Vietnam blockchain community on the significance of Web3 security through a series of workshops and speaking engagements.
This week, Verichains Co-founder Thanh Nguyen will be speaking at GM Vietnam sharing his expertise in MPC technology in a session called: Unlocking the Future: MPC-Powered Blockchain Wallets for Enhanced Privacy and Security.
Join us at GM Vietnam and catch the latest insight from Verichains Co-founder on Friday, July 7th at 16:50 ICT, at Thiskyhall Sala Convention Center - Sofic Tower.
Last Week’s Incidents
🚨Project: Poly Network
⛓️Chain: Metis, Arbitrum, Avalanche, BSC, Ethereum, Fantom, Gnosis, Heco, OKT, Optimism, Polygon.
💥Type: Possible Compromised Private Keys
💸Loss amount: ~$10,000,000 (and counting)
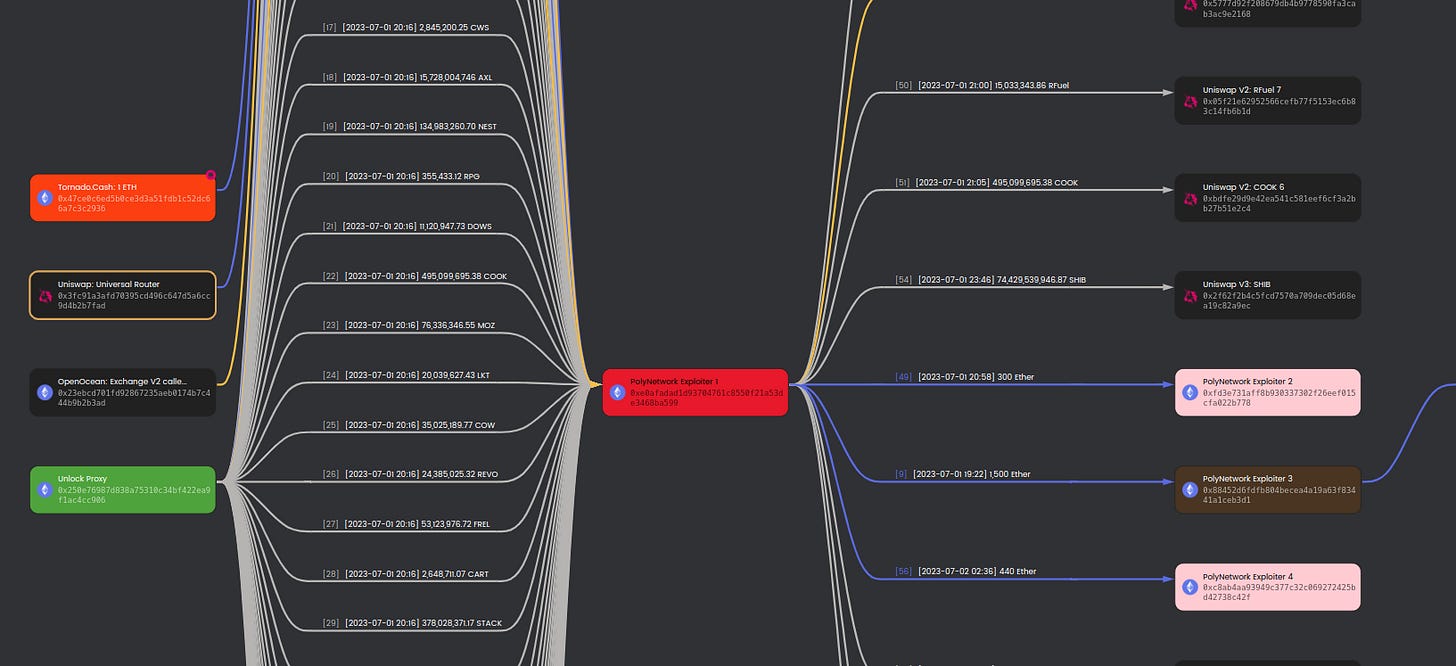
On July 2, 2023, the Poly Network protocol was exploited once again, following the previous attack in 2021. During the initial stages of the investigation, it was discovered that the attack occurred within the bridge contracts, which are responsible for cross-chain asset transfer. According to our investigation, significant amounts of various tokens were withdrawn from the LockProxy contract by triggering the verifyHeaderAndExecuteTx function of the EthCrossChainManager contract.
This function checks the validity of the header from the source chain, which is signed by a list of keepers. The header contains the state root, which will then be used to validate the Merkle proof.
It seems like there are no security vulnerabilities within the contract logic but the keeper accounts have been compromised, as the keeper account addresses were not changed prior to the attack. However, the Poly Network team has not yet confirmed any details regarding this matter.
The attack has affected over 58 assets across 11 blockchains, including Ethereum, BSC, Polygon, Avalanche, Metis, etc. All of these assets have been sent to the attacker's wallet at the address 0xe0Afadad1d93704761c8550F21A53DE3468Ba599. According to Beosin Alert, the attacker has exchanged the stolen assets into 5,196 ETH (~$10.1m) on the Ethereum blockchain. However, other tokens (~$260 million) may not be cashed out by the attacker due to low liquidity.
🚨Project: ShidoGlobal
⛓️Chain: BSC
💥Type: Access Control
💸Loss amount: $240,000
In an attack last week, a DEX called Shido Global was exploited for ~$240,000 due to a misconfigured contract called AddRemoveLiquidityForFeeOnTransferToken, which was responsible for handling the addition of liquidity for a pair of tokens. Due to this misconfiguration, the contract transferred all of its balance, including both BNB and SHIDOv1 to the attacker.
The attacker then took advantage of a feature in ShidoLock to exchange SHIDOv1 and SHIDOv2 tokens. By doing so, they were able to profit from a pool of SHIDOv2 tokens.
Since the attack, Shido had acknowledged the exploit, and a fix was deployed.
🚨Project: Themis Protocol
⛓️Chain: Arbitrum
💥Type: Price Manipulation
💸Loss amount: $370,000
A DeFi project called Themis Protocol was exploited for ~$370,000 due to a flawed oracle. The attacker executed a flashloan to manipulate the price of a balancer LP. With the borrowed ETH, the attacker artificially manipulated the LP price and then proceeded to borrow additional ETH from Themis, taking advantage of the manipulated price. The flaw in the oracle allowed the attacker to deceive the system, enabling them to profit from this manipulation and borrow more ETH than would have been possible under normal circumstances.
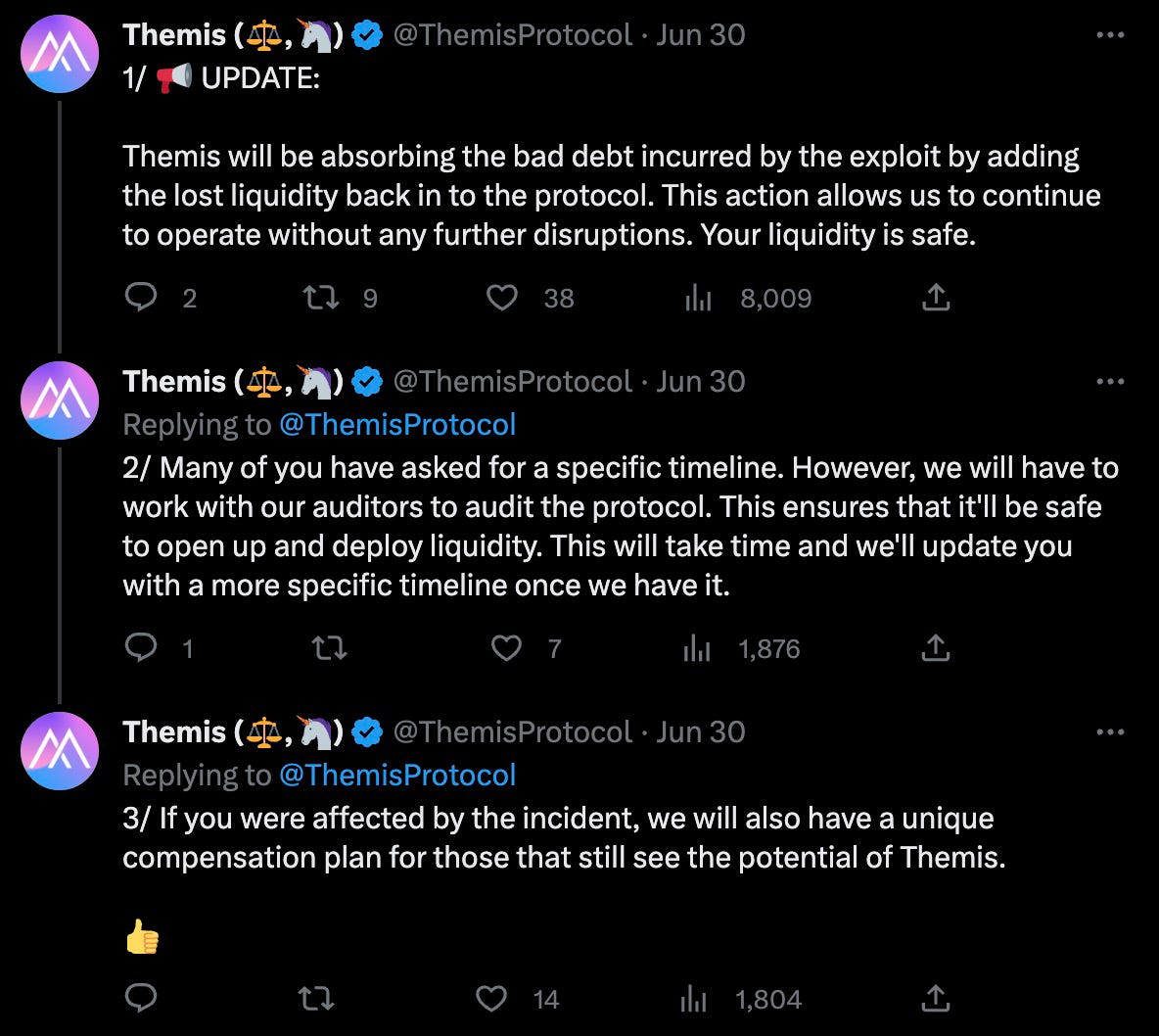
Since the attack, Themis Protocol had acknowledged the exploit and is absorbing the bad debt incurred by adding lost liquidity back to the protocol, ensuring the safety of their user’s liquidity. Furthermore, a compensation plan is also in place to reimburse affected users.