Verichains Weekly Security Digest | August 2023 Week 1
In this week's digest, the DeFi market suffered a staggering loss of $46,000,000, with the most significant impact felt by CoinsPaid, losing a massive $37,300,000 in an intense and captivating hybrid attack.
Last Week’s Incidents
🚨Project: Palmswap
⛓️Chain: BSC
💥Type: Business Logic Flaw
💸Loss amount: $900,000
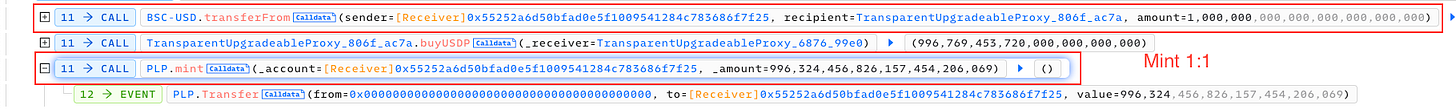
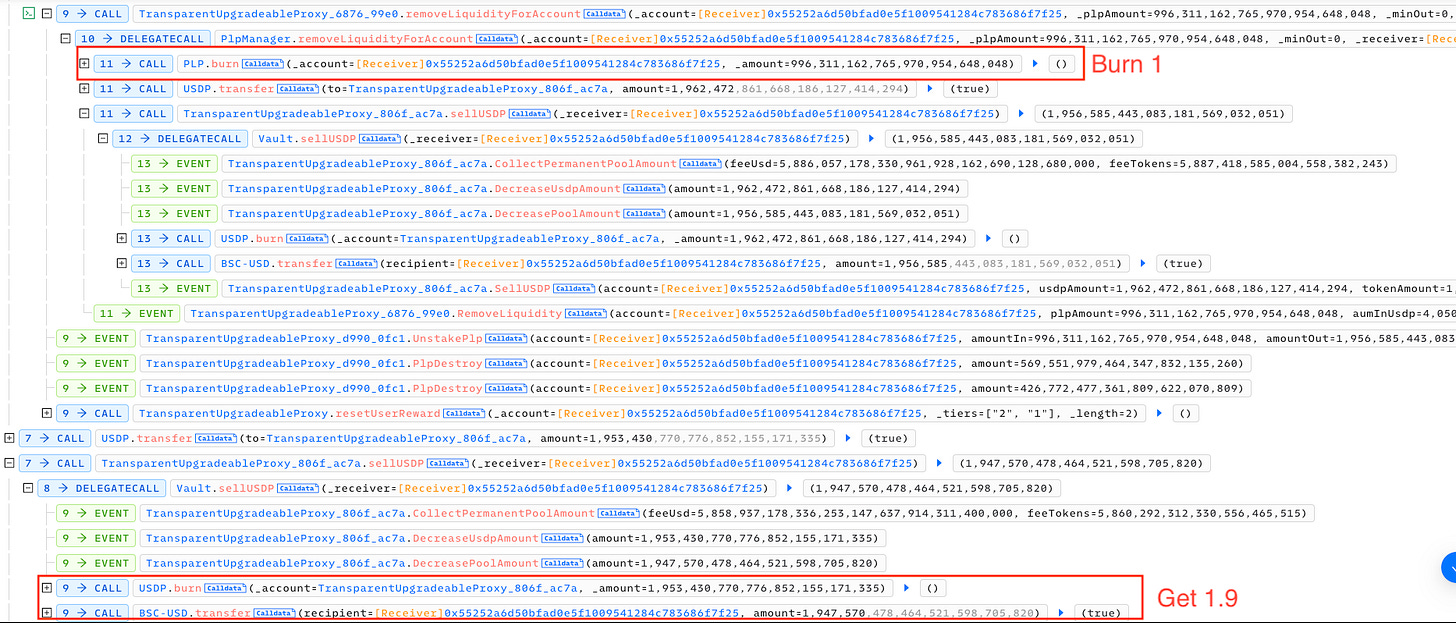
Last week, Palmswap was attacked for $900,000 due to a vulnerability in the calculations for adding and removing liquidity of $USDP and $PLP. Initially, the exchange rate between the two tokens was 1:1 when the attacker added liquidity.
However, the problem arose when the attacker attempted to remove the same amount of $PLP, as they were able to exchange it for 1.9 times more $USDP than the original amount added. This discrepancy allowed the attacker to exploit the system, gaining an unfair advantage and benefiting from the flawed liquidity mechanism. The silver lining is, the platform had recovered 80% of the fund through negotiation with the white hat.
🚨Project: Conic Finance
⛓️Chain: ETH
💥Type: Read-only Reentrancy
💸Loss amount: ~4,200,000
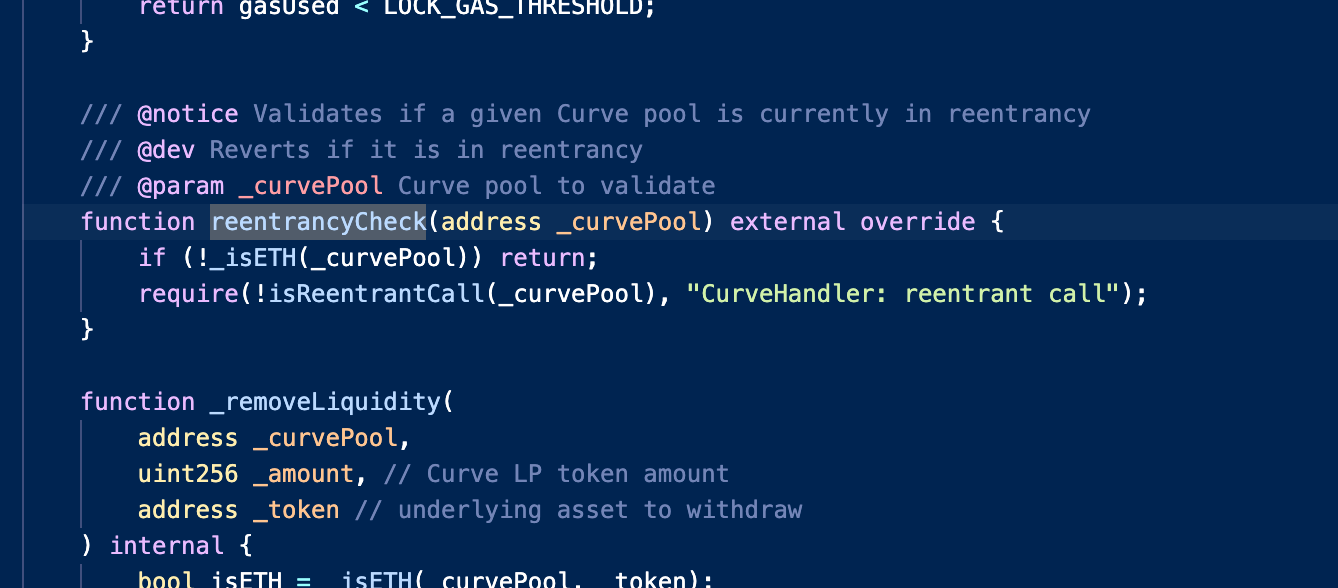
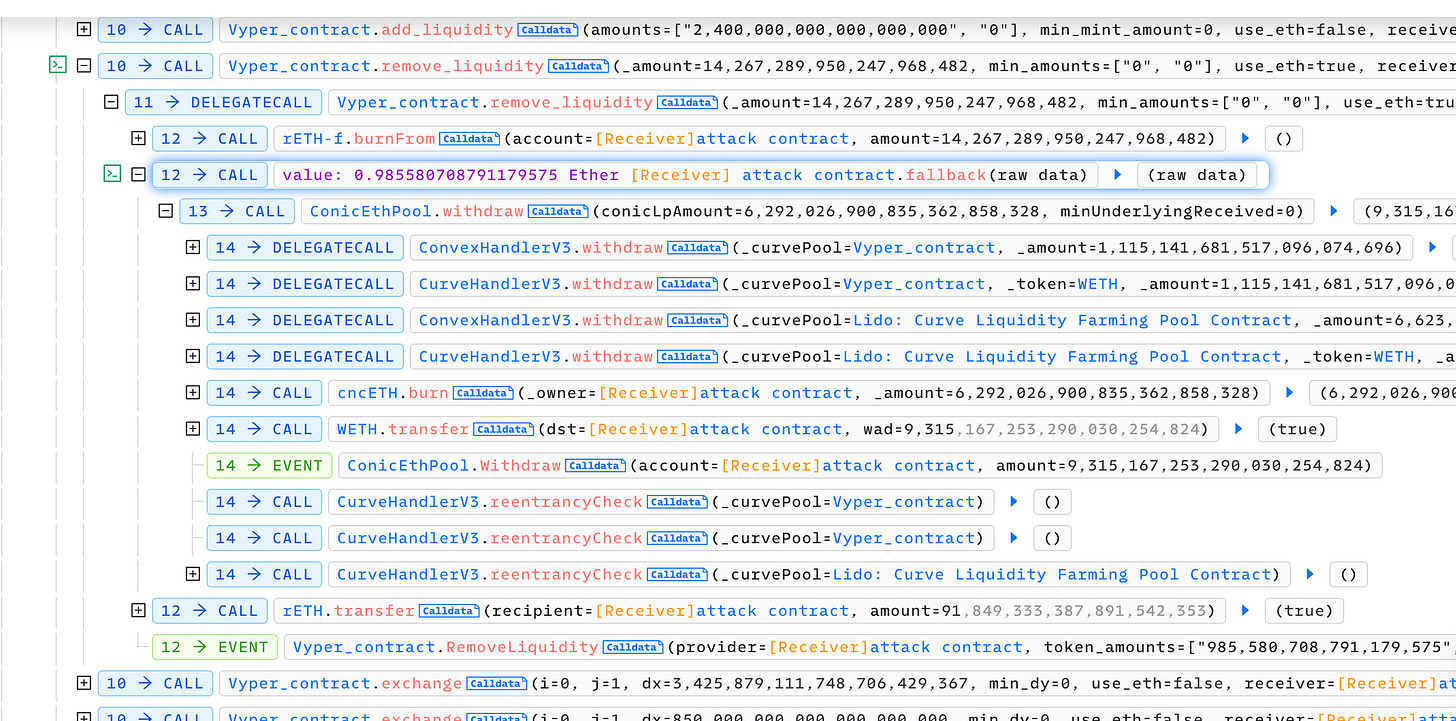
Conic Finance suffered 2 separate attacks last week, incurring over $4,200,000 in loss. In the first incident, the attacker utilized flash loans from Aave v2, Aave v3, and Balancer to borrow funds. They then converted these funds into WETH and deposited them repeatedly into the ConicEthPool. The attacker exploited a read-only reentrancy vulnerability present in the Curve LP pool contract, which allowed them to manipulate the oracle price result of the get_virtual_price function. By calling the remove_liquidity function on Curve pools, the attacker triggered ETH withdrawals and was able to perform reentrancy attacks. Although the ConicEthPool had a _reentrancyCheck function in place to prevent such attacks, it was erroneously handling the check for the WETH token, leaving the pool still vulnerable.
The attack targeted three pools, stETH/ETH (LidoCurvePool), cbETH/ETH, and rETH/ETH, setting the first two as depegged pools via ConicEthPool.handleDepeggedCurvePool(). The attacker successfully withdrew assets from the ConicEthPool, resulting in an estimated loss of approximately $3.25 million
.
In the second attack, Conic Finance suffered a sandwich attack by an MEV bot. It took advantage of Conic's imbalanced pools, repeatedly exchanging and depositing funds between crvUSD and USDC in the Curve pool, resulting in a profit of approximately $300,000 from the theft of about $934,000 worth of assets
Conic Finance has since acknowledged both attacks and published a post-mortem.
🚨Project: EraLend
⛓️Chain: ZKSync
💥Type: Price Manipulation
💸Loss amount: ~$3,400,000
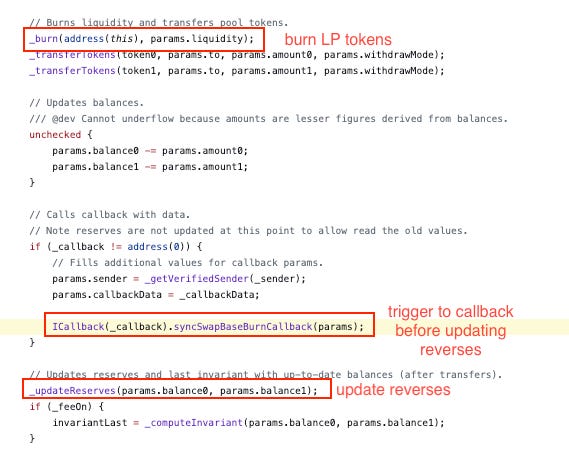
EraLend was under attack for approximately $3,400,000 due to a price calculation error that took place due to its ctoken's reliance on SyncSwap for determining prices. The attacker exploited a reentrancy vulnerability in SyncSwap's code, allowing them to burn their LP tokens while borrowing ctokens using outdated reserves. After executing the reentrancy attack, the reserves were updated, creating a situation where the attacker could repay the borrowed ctokens with fewer tokens than they initially borrowed. This discrepancy in repayment enabled the attacker to make a profit from the exploit.
The project had acknowledged the vulnerability but failed to contact the attacker. A 10% bounty is out for any information on the attacker that led to the successful recovery of the stolen fund.
🚨Project: $Carson
⛓️Chain: BSC
💥Type: Price Manipulation
💸Loss amount: ~14,400
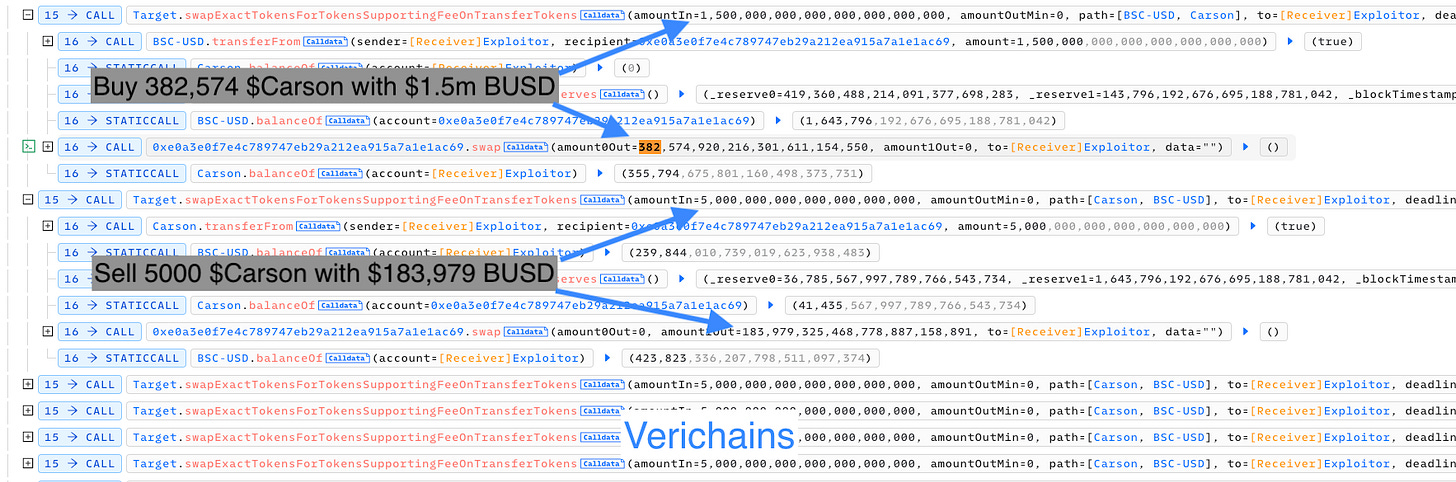
A token called $Carson suffered a flashloan attack, losing ~$14,400. The attacker took a flash loan of 1.5 million BUSD from multiple pools. With this borrowed amount, they purchased 382,574 tokens of $Carson. Afterward, the attacker engaged in a series of rapid token sales, divesting 5,000 tokens at a time until the entire borrowed fund was depleted. By carefully orchestrating the sales, the attacker ensured that each transaction yielded profits higher than the initial purchase price, allowing them to profit from the operation.
🚨Project: CoinsPaid
⛓️Chain: TRX, ETH, BTC
💥Type: Hybrid Attack
💸Loss amount: 37,300,000
In an alleged attack by the infamous black hat group, Lazarus, CoinsPaid was exploited for 37,300,000. At the time of writing, the root cause of the attack was not disclosed. However, it was mentioned that the attackers employed a hybrid attack involving social engineering, aggressive bribery attempts on critical personnel, and attacks through various internet-accessible applications to compromise CoinsPaid's infrastructure supporting transactions and modify transaction data.
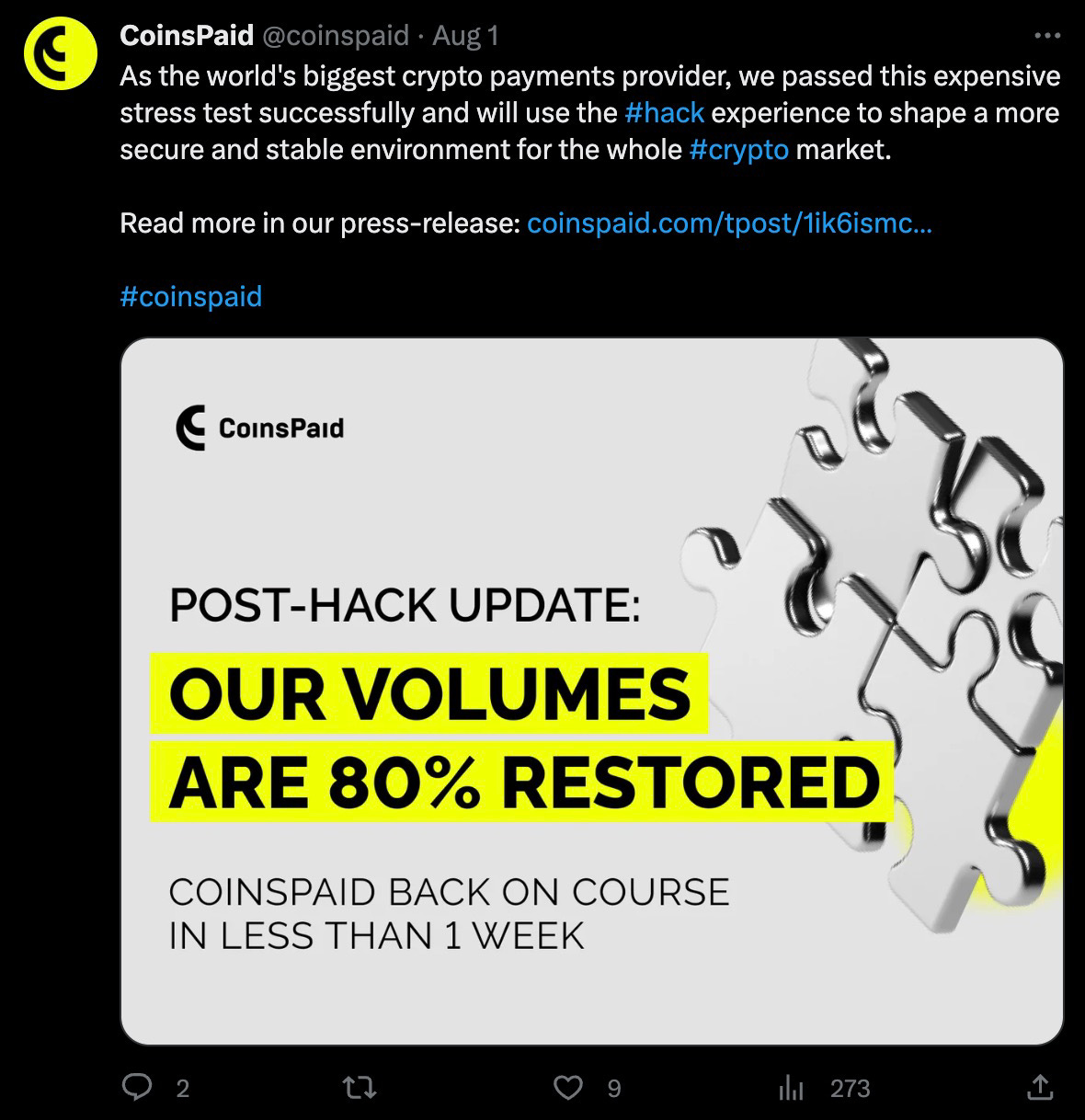
CoinsPaid has since restored 80% of its volume with no loss to its customers.