Verichains Weekly Security Digest | July 2023 Week 3
Last week, the DeFi market suffered heavy losses with 6 major incidents, losing over $2,000,000. Among the affected projects, Rodeo Finance incurred the most substantial impact, facing losses amounting to approximately $888,000.
Last Week’s Incidents
🚨Project: Rodeo Finance
⛓️Chain: Arbitrum
💥Type: TWAP Oracle Manipulation
💸Loss amount: ~$888,000
Last week, the Rodeo Finance protocol fell victim to an exploit, resulting in approximately $888,000 being taken by the attackers. They executed their scheme by manipulating the price of TWAP Oracle through several transactions and further exchanged substantial amounts of WETH to unshETH.
Following this, the attacker utilized the Investor.earn() function to initiate a long position using the borrowed funds from the USDC pool. This action triggered a significant swap of 400,000 USDC to WETH, and then to unshETH in the Camelot pool, effectively manipulating the prices of WETH and unshETH. The flaw in the unshETH price oracle rendered the slippage control ineffective, contributing to the attacker's success.
Subsequently, the attacker converted their unshETH and Balancer's borrowed WETH to acquire USDC using Camelot pools. They then executed a reverse swap by using Uniswap v3 pools to convert the USDC back to WETH, ultimately repaying Balancer's flashloan.
In summary, the attackers strategically navigated through multiple transactions, exploiting vulnerabilities in the system to their advantage, and successfully executed their plan, resulting in a substantial financial loss for the Rodeo Finance protocol.
Rodeo Finance had since acknowledge the exploit, published a post mortem along with a remediation plan and are anticipated to relaunch later this July.
🚨Project: Libertify
⛓️Chain: Ethereum, Polygon
💥Type: Reentrancy
💸Loss amount: ~$452,000
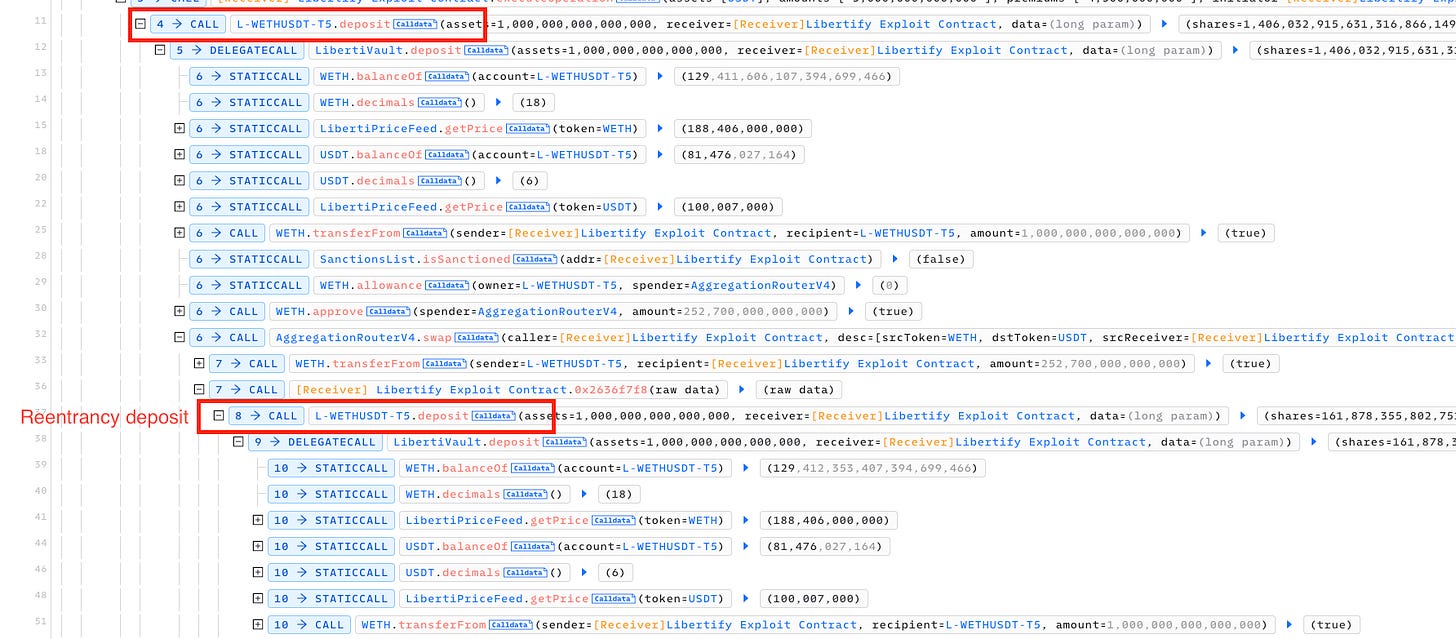
A DeFi project called Libertify was exploited for almost half a million due to a reentrancy issue. During the deposit process, a hacker can exploit the userSwap function and use reentrancy to manipulate the deposit flow, allowing them to alter the total supply and mint additional shares.
The project confirmed that only $232 of users’ funds was lost, while the rest were internal/company funds.
🚨Project: $LUSD
⛓️Chain: BSC
💥Type: Price Manipulation Attack
💸Loss amount: $9,464
A token called $LUSD was hacked for $9,464. The attacker capitalized on the loan contract's dependence on PancakeSwap's on-chain price by executing a flash loan. This manipulation enabled them to acquire a considerable amount of undervalued LUSD tokens, which they promptly converted into USDT to profit from the price manipulation.
🚨Project: CivFund
⛓️Chain: Ethereum
💥Type: Approval Issue
💸Loss amount: ~$180,000
Within the CivFund project, there's a smart contract identified by the address 0x7caec5e4a3906d0919895d113f7ed9b3a0cbf826. The contract's intended purpose is to enable users to add liquidity to a pool by utilizing the function 0x5ffe72b7. The function requires a parameter representing the address of the pool token. Upon calling this function with the pool token address, the contract invokes the mint function of the corresponding pool contract to create LP tokens. However, a critical vulnerability exists due to the user's control over the pool token address parameter, which opens the door for potential exploitation.
The attacker takes advantage of the vulnerability by defining two functions, namely mint() and token1(). The token1() function retrieves the tokens that the victim has approved for this contract, indicating what tokens the victim allows the contract to manage on their behalf. The mint() function is called when users add liquidity to the pool through the function 0x5ffe72b7. Inside mint(), the attacker introduces a callback function called "uniswapV3MintCallback," and manipulates the transferFrom function to direct tokens from the victim (sender) to the attacker's address (recipient). As a result, the attacker can maliciously control the minting process and siphon tokens from unsuspecting users to their own addresses.
At the time of writing, the project had acknowledged the exploit and published a post-mortem.
🚨Project: Platypus
⛓️Chain: Avalanche
💥Type: Logic Error
💸Loss amount: ~$51,000
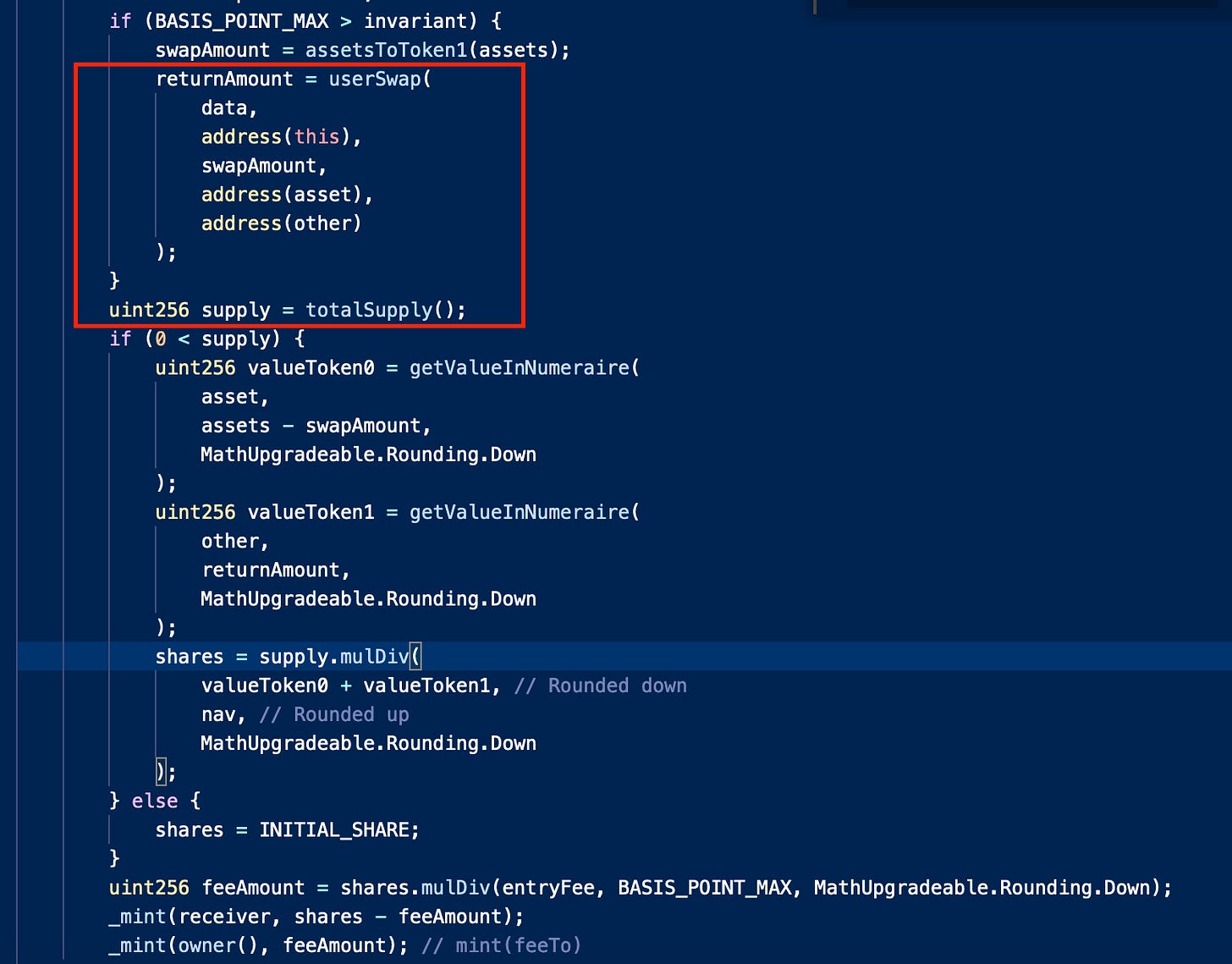
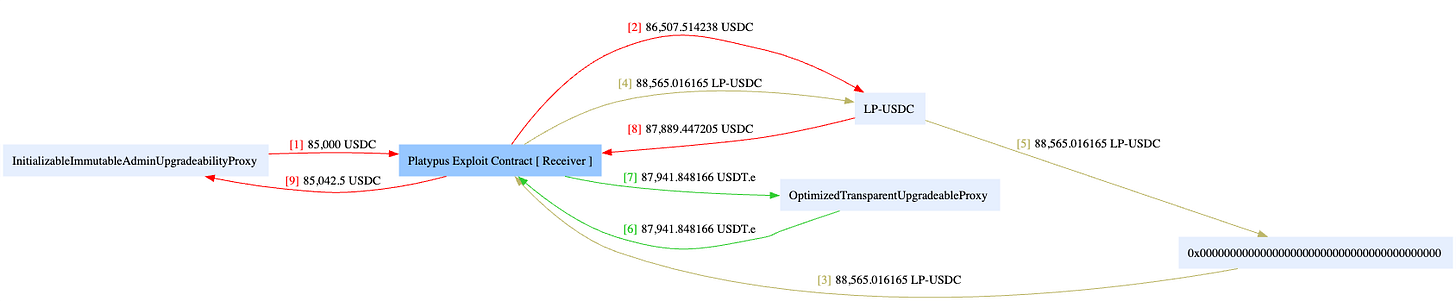
Platypus was exploited for the second time this year for ~$51,000. The _deposit method within the contract allows a user to transfer USDC tokens. However, when the user calls the _withdrawFrom method to withdraw the funds, the number of tokens received by the user is greater than the number of tokens deposited. This inconsistency is caused by a logical error in the calculation of the exchange rate.
At the time of writing, the team had acknowledged the issue and paused their pool operation.
Earlier this year, the protocol was hacked for over $8,000,000 due to a flaw in the USP solvency check mechanism, allowing the attacker to exploit a logic error and steal funds. However, the attacker forgot to code a way to collect the stolen funds. Platypusdefi recovered the 2.4 million USDC due to a mistake made by the attacker.
🚨Project: Arcadia Finance
⛓️Chain: Ethereum, Optimism
💥Type: Logic Error
💸Loss amount: ~$455,000
Arcadia Finance was attacked for an approximate $455,000 due to a missing reentrancy check in the liquidation process of a Vault. The attacker exploited this vulnerability by following a series of steps, which involved creating a new Vault, depositing funds, and borrowing a substantial amount from the Liquidity Pool. By taking advantage of the reentrancy issue, the attacker could manipulate the assets optimistically, leading to a successful liquidation where the debt was removed, leaving the Vault with zero assets and zero debt, thus passing the final health check. This loophole allowed the attacker to drain the liquidity pools and execute the exploit. To prevent similar attacks in the future, it is crucial for developers to thoroughly implement reentrancy checks and conduct rigorous security audits to identify and address potential vulnerabilities in their smart contracts.