Vista Finance Hack Analysis
Vista Finance suffered an exploit on October 21, 2024, resulting in an estimated loss of approximately $29,000 at the time of writing. The root cause of the exploit is in the ERC20FlashMint integrated with the custom staking logic with Vista token contract.
Overview
Attacker: https://bscscan.com/address/0x3d71366228ebd5196d45ee72f82405da601190ad
Vulnerable Contract: https://bscscan.com/address/0x493361D6164093936c86Dcb35Ad03b4C0D032076
Transaction attack: https://bscscan.com/tx/0x84c385aab658d86b64e132e8db0c092756d5a9331a1131bf05f8214d08efba56
Exploit Analysis
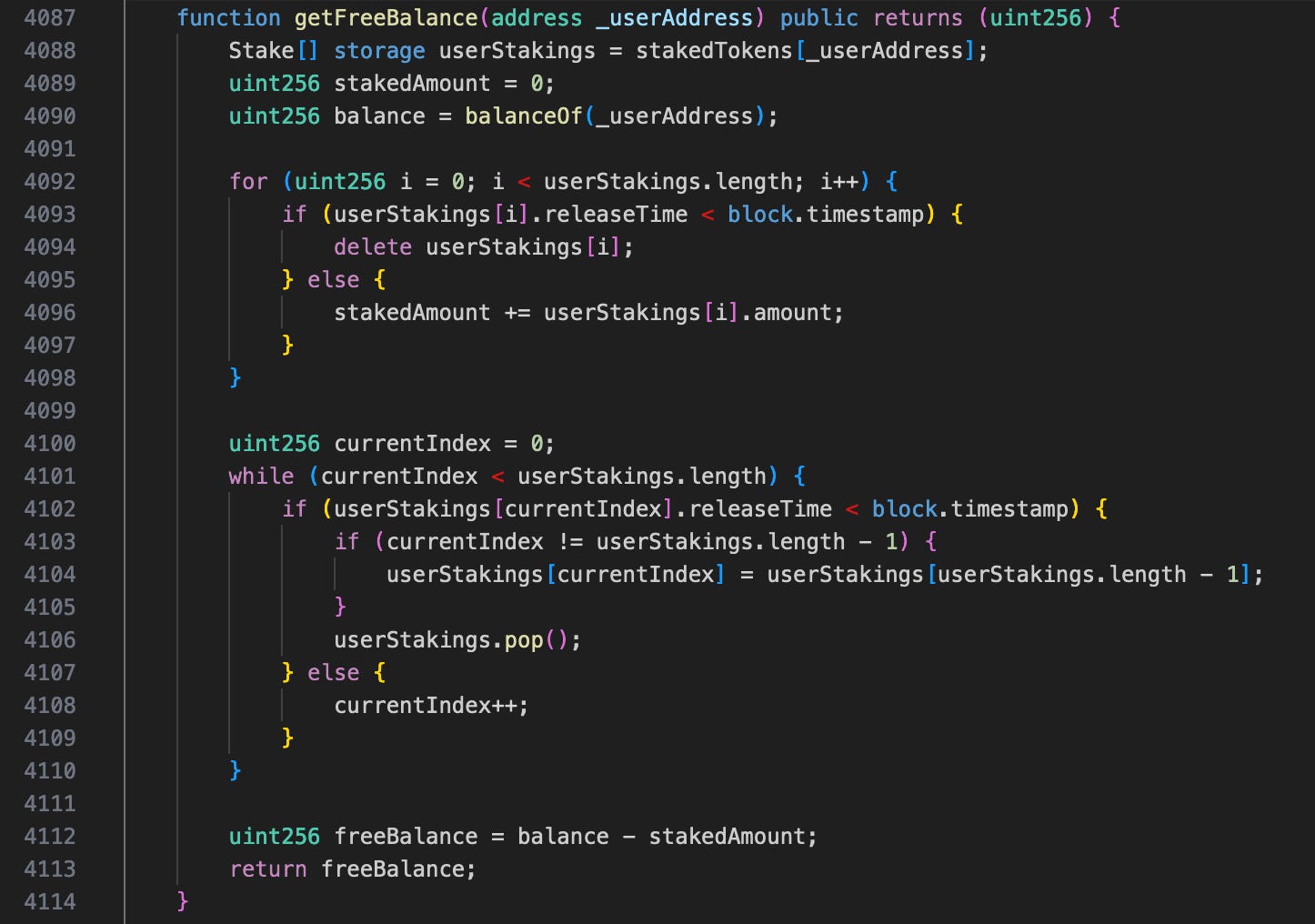
Vista Finance allows users to buy ICOs using BUSD to receive staked Vista tokens. The issue is that it does not transfer the staked tokens to a staking contract; instead, it only records the staked amount and calculates the user’s balance by subtracting the staked tokens from the tokens held.
The user’s balance seems to be correct if all transfer functions use the getFreeBalance function, but the integration of ERC20FlashMint into the Vista token causes it to be incorrect.
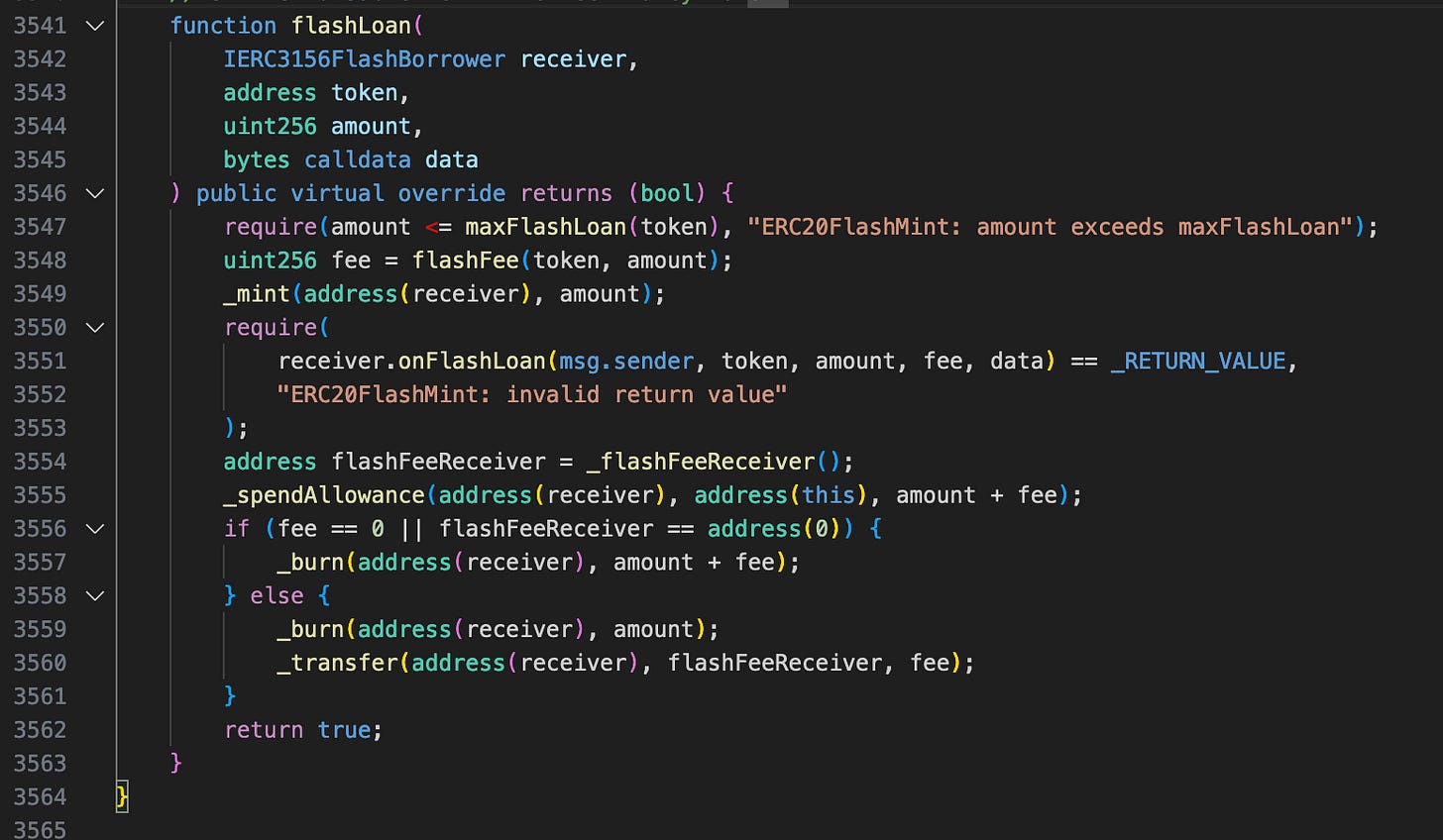
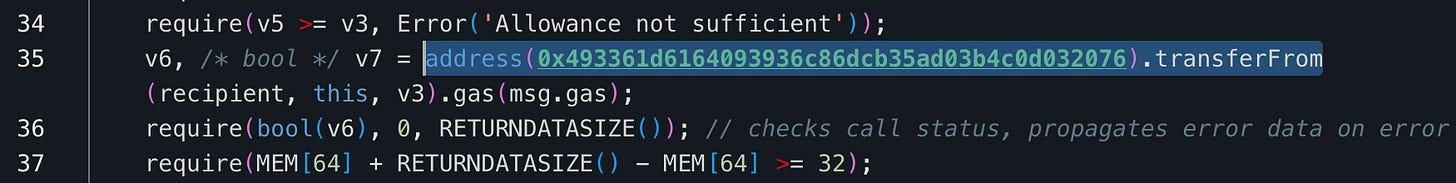
The flashLoan function mints tokens at the beginning of the flashloan and burns them at the end. The problem is that _burn does not use getFreeBalance but directly subtracts from _balances[account]. This means that even if the tokens are staked and cannot be transferred, they can still be burned to repay the flashloan.
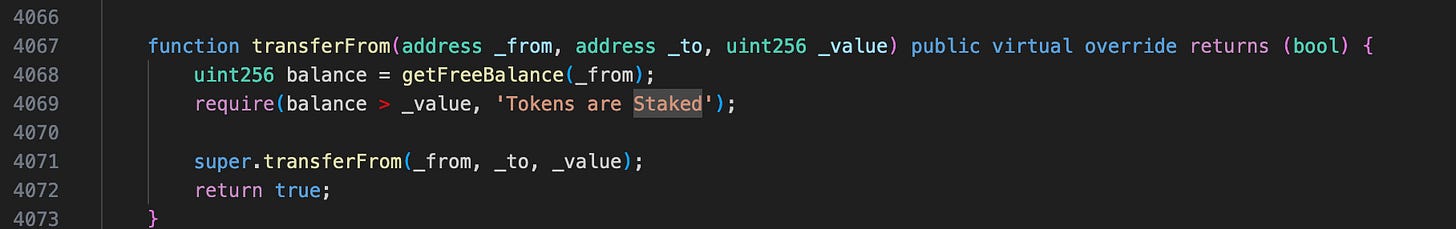
The attacker flashloaned 1,000,000 tokens and bought tokens from the ICO contract using $1,500, then sold the purchased tokens to 0xf738de9913bc1e21b1a985bb0e39db75091263b7 to make a profit. This selling process uses transferFrom function which relies on the actual balance from getFreeBalance function so the attacker will be unable to sell the bought tokens (as they were staked) without the tokens minted from flashloan.
The flashLoan function finally burned 1,000,000 tokens directly from _balances[account] to end the process. If the flashLoan function were to use the getFreeBalance function, the attacker would not have sufficient free balance, thus preventing the exploit.
Lesson learned
Developers must thoroughly review and understand the logic of third-party contracts when integrating them with their custom logic to prevent any inconsistencies.
It is strongly recommended to conduct a security audit, whether it is a simple ERC20 contract with some minor changes or a complex DeFi protocol with hundreds of thousands of lines of code.