WXC Exploit Analysis
On August 11, 2025, a critical vulnerability was exploited in the WXC token contracts, resulting in an estimated loss of approximately 37.5 BNB. The attacker exploited the burn mechanism of the WXC token when there is token selling on the pool.
Overview
Attacker: https://bscscan.com/address/0x476954c752a6ee04b68382c97f7560040eda7309
Vulnerable Contract: https://bscscan.com/address/0x4c100d30d9c511b8bb9d1c951bbc1be489a0172f
Exploit TXs: https://bscscan.com/tx/0x1397bc7f0d284f8e2e30d0a9edd0db1f3eb0dd284c75e30d226b02bf09ad068f
Exploit Analysis
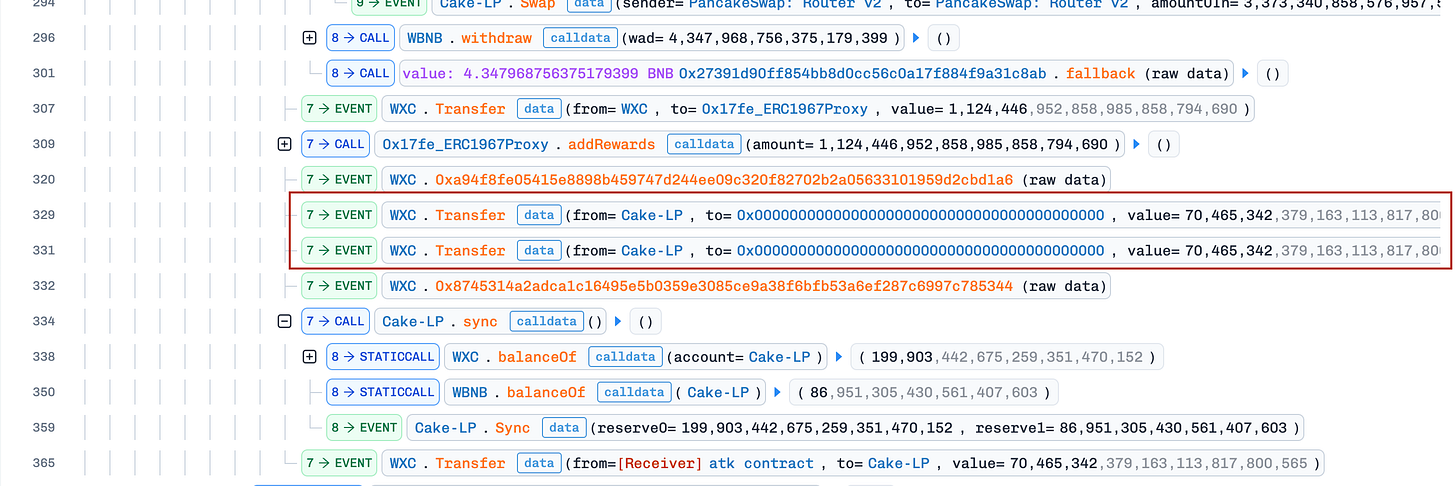
The WXC token contract includes logic to burn WXC tokens when someone sells the token into the pool. The problem is that it burns tokens from the PancakeSwapV2 pool itself, which decreases the pool’s WXC balance.
The attacker first flash-loaned WBNB, swapped it to WXC at the current price, and then swapped back to WBNB. This swap back triggered WXC’s logic to burn the pool’s WXC balance in the middle of the swap, pushing WXC’s price higher. Attacker using this to take more WBNB from pool than in a normal swap, completing the exploit.
Conclusion
When adding any logic to a token contract, especially fee or burn logic on transfers, always proceed with caution, as it may directly reduce an AMM’s pool balance during swaps and create vulnerabilities that attackers can exploit.
Furthermore, conducting a security audit is strongly recommended for all projects, even though they are smart contracts, backends, wallets, or dapps.